Claude Security Explained: Benefits, Challenges & Compliance

What is Claude Security?
Claude security is the application of security controls and review processes to Anthropic’s Claude models, particularly Claude Code, to prevent security vulnerabilities during coding, file creation, and enterprise use. It is the practice of protecting source code, user data, and development workflows by combining AI analysis, permission management, and compliance-oriented practices. This distinction is especially important at a time when shadow AI discovery shows how often teams experiment with models outside approved governance.
Types of Security Risks in Claude
Claude Code introduces new opportunities for secure automation, but it also carries risks that organizations must evaluate carefully. The most common issues fall into distinct categories that reflect both model behavior and integration in development workflows.
- Prompt Injection Attacks: Malicious instructions hidden in input text can override Claude’s intended behavior and lead to harmful actions, including exfiltrating sensitive data.
- Hidden or Malicious Code Execution: Claude can generate code snippets with embedded threats, such as remote execution payloads or unsafe defaults that slip into production.
- Data Leakage in Outputs: Outputs may unintentionally reveal personal data, secrets, or internal project details if prompts or context windows are not carefully controlled.
- File-Based Indirect Prompt Injection: External files, such as documents or spreadsheets created in Claude, can embed instructions that manipulate the model when later processed.
- Missed or False-Positive Detections: AI-driven analysis can either fail to flag genuine security vulnerabilities or overwhelm developers with false positives that reduce trust in reviews.
Claude Security Review Process Steps
A complete review process makes Claude Code an asset instead of a liability. Each step adds a distinct protection, moving from AI output to human oversight and compliance controls.
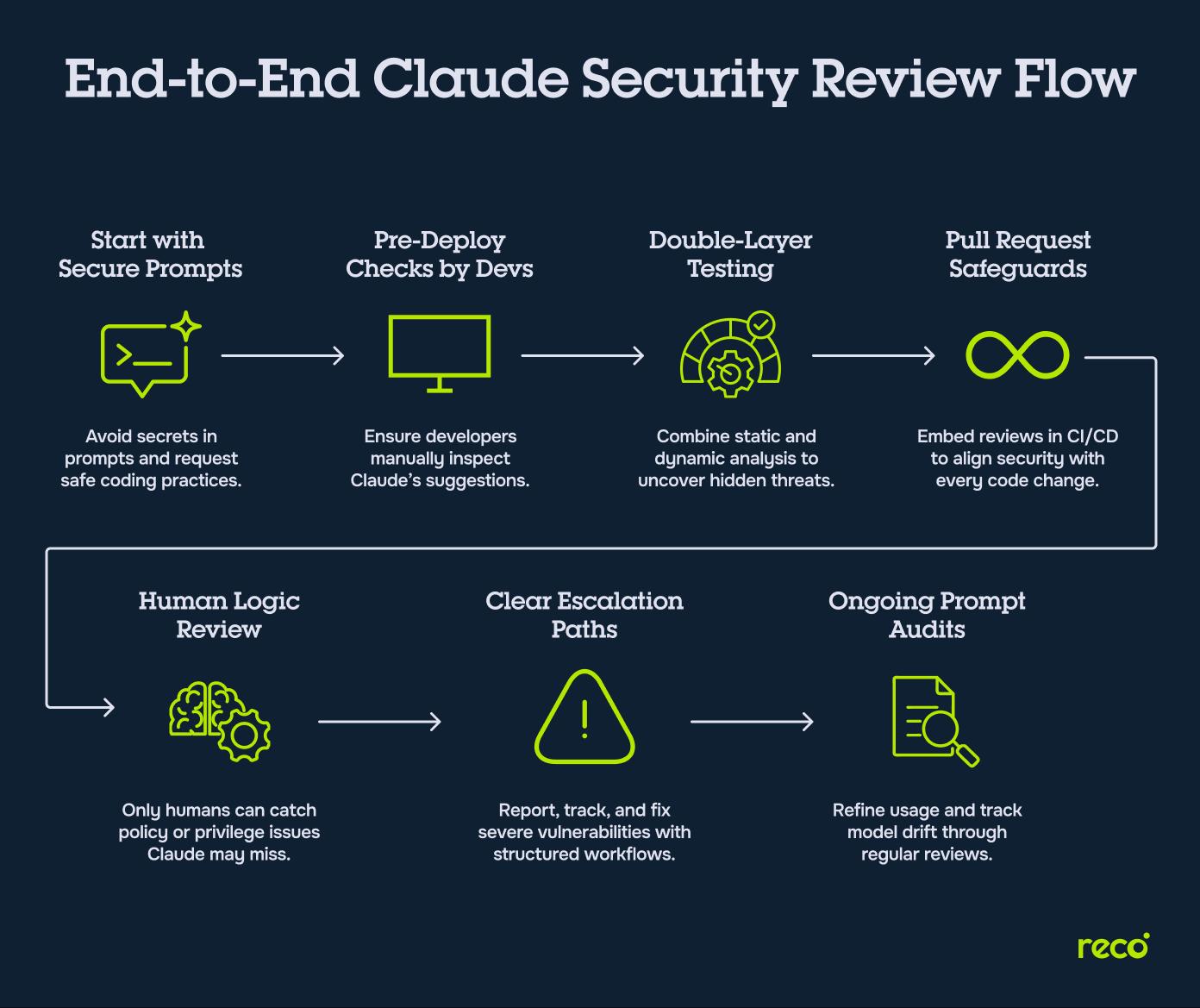
Step 1: Code Generation or Suggestion via Claude
Treat Claude Code’s output as unverified. Keep prompts precise, exclude sensitive data such as API keys, and request secure defaults like input validation. Early clarity reduces insecure code patterns that can complicate later reviews.
Step 2: Initial Developer Review of Claude Output
Developers should inspect Claude’s suggestions before automation begins. Look for high-risk flaws such as unsanitized inputs, weak cryptography, or unsafe default settings. This early pass prevents flawed code from entering the pipeline.
Step 3: Static and Dynamic Scanning with External Security Tools
Pair Claude with SAST and DAST tools. Static analysis highlights insecure constructs, while dynamic scans test runtime threats, such as SQL injection. For example, a team might combine Claude Code with Semgrep for static checks and OWASP ZAP for dynamic testing. Using both compensates for false positives and gaps in Claude’s detection.
Step 4: Integration into Pull Request Workflows
Run Claude’s security review inside pull requests. Findings align with code changes, streamlining fixes while maintaining development speed. Integration with CI/CD ensures every change undergoes a consistent baseline review.
Step 5: Manual Review for Business Logic and Edge Cases
Human oversight remains critical for rules and scenarios that Claude cannot infer. Reviewers check business logic, permissions, and regulatory alignment. For instance, only a human reviewer may notice that a function allows role escalation without proper authorization checks, an issue that automated tools would miss.
Step 6: Escalation and Reporting Process for Detected Issues
High-risk findings need a defined escalation path. Formal reporting security issues protocols assign responsibility, track remediation, and prevent repeat exposures. Without this, critical vulnerabilities can be lost among routine tasks.
Step 7: Periodic Review of Prompting Patterns and AI Behavior
Ongoing audits measure prompt quality, model drift, and the frequency of false positives. Regular reviews enhance prompting strategies and ensure Claude Code users consistently apply secure practices. These evaluations also connect to broader Agentic AI security concerns, since autonomous model decisions can introduce risks that require ongoing human oversight.
Benefits and Limitations of Claude Security
Claude Code offers clear advantages in development workflows, but these strengths must be balanced against practical constraints. The table below compares the two sides in a structured way.
Challenges in Securing LLMs Like Claude
Even with structured review processes, large language models such as Claude present challenges that go beyond traditional code security. These issues arise from the nature of the models themselves and their integration into enterprise workflows.
- Lack of Model Transparency and Reproducibility: Security teams cannot fully audit how Claude generates its responses, making it difficult to trace decisions or reproduce outputs for investigation. This limits accountability when reviewing security vulnerabilities discovered in AI-generated code.
- Difficulty in Fine-Grained Access Control: Claude does not inherently understand organizational permissions or separation of duties. Without external enforcement, there is a risk that Claude Code users may unintentionally gain access to operations or data beyond their role.
- Model Drift and Response Variability: Over time, Claude’s outputs can shift as models are updated or as prompts evolve. This variability introduces uncertainty, leading to inconsistent security review results and the possibility of missing issues in future scans.
Best Practices for Using Claude Securely
Organizations can strengthen their use of Claude Code by combining AI-driven reviews with established security measures. The table below outlines key practices and explains how they reduce risk in development workflows:
Compliance and Regulatory Considerations in Claude Security
Enterprises adopting Claude Code must balance technical controls with legal and regulatory obligations. Key considerations include data protection, auditability, and storage requirements.
Alignment with GDPR, HIPAA, and SOC 2
Claude Code carries certifications such as SOC 2 Type 2 and ISO 27001, but these do not cover all regulations. Under the GDPR, organizations must control how personal data appears in prompts or outputs. In healthcare, HIPAA requires strict oversight of patient data, making human review mandatory. For SOC 2 audits, enterprises must show that Claude’s security review process is tied to access management and monitoring. Compliance remains the responsibility of the organization, not Anthropic.
AI-Driven Audit Challenges
Claude’s outputs can vary with prompts or model updates, making reproducibility difficult. This complicates audits since regulators expect clear evidence of how security vulnerabilities were found and addressed. Logging all review code interactions, including rejected suggestions, is essential to maintain accountability and provide audit trails.
Cloud Storage and Data Residency Concerns
Claude’s file-creation and sandbox features raise questions about where data is stored and processed. For GDPR and sector-specific residency rules, teams must ensure restricted access to sensitive data and prevent API keys or secrets from being included in prompts. Anthropic’s allowlist helps, but independent audits and policy enforcement are needed before Claude is approved for regulated workloads.
How Reco Strengthens Security Across Claude-Driven Workflows
While Claude Code can assist with automated analysis, organizations still need continuous monitoring and governance. Reco extends protection across AI-driven workflows by adding visibility and control at the enterprise level.
- Detecting Sensitive Data Flows Across Prompts, APIs, and Outputs: Reco identifies when confidential information such as credentials, customer records, or source code fragments is exposed in Claude interactions, helping security teams prevent data leakage in real-time.
- Preventing AI-Based Leakage Through Prompt Misuse: By monitoring the content of prompts and responses, Reco can flag attempts to manipulate Claude into disclosing restricted information or executing unsafe instructions.
- Monitoring Cross-App Access Involving Claude: Reco tracks when Claude interacts with SaaS applications or external services, ensuring Claude Code users do not gain unauthorized access to critical systems.
- Reinforcing Governance with Activity Logging and Policy Controls: Detailed logs of all Claude-related activity are paired with policy enforcement. This supports audit readiness, reduces compliance risks, and creates accountability across the full security review lifecycle. For organizations exploring protocol-level integrations, this governance approach extends naturally to areas like MCP security, where third-party servers must be evaluated with the same rigor.
Conclusion
Claude security is less about replacing traditional defenses and more about strengthening them through AI-driven review. When used with structured processes, security review steps, and clear escalation paths, Claude Code can reduce repetitive workload and accelerate detection of security vulnerabilities. The responsibility, however, remains with organizations to enforce restricted access, monitor usage, and align with compliance frameworks like GDPR, HIPAA, and SOC 2.
Looking ahead, organizations that blend automation with governance will be best positioned to benefit from Claude without introducing hidden risks. The balance between scale and accountability will define how effectively Claude Code supports secure, compliant development.
How can organizations ensure that Claude doesn’t expose sensitive or regulated data?
The most reliable method is to restrict what is shared with Claude in the first place. Sensitive data such as API keys, credentials, or regulated personal information should never be included in prompts. Enterprises should also configure restricted access controls around Claude Code, monitor outputs for accidental disclosures, and enforce human validation of flagged issues.
Does Claude integrate with existing AppSec tools like DAST or SAST?
Yes. Claude Code can complement existing security pipelines by working alongside static and dynamic testing tools. For example, pairing Claude with SAST platforms like Semgrep or dynamic scanners such as OWASP ZAP strengthens coverage by detecting issues such as SQL injection that may not appear in Claude’s own findings.
How does Reco detect unauthorized or risky use of Claude across teams?
Reco provides visibility into how Claude is used across workflows by monitoring cross-application access, flagging unusual data flows, and logging activity for review. This allows security teams to identify patterns that suggest misuse, such as attempts to extract restricted data or bypass organizational policy.
Can Reco help monitor prompt-level activity or anomalies in LLM usage?
Yes. Reco extends governance to the prompt level by tracking interactions with Claude Code, correlating them with policy rules, and flagging anomalies that could indicate misuse or false positives being overlooked. This capability ensures enterprises can maintain accountability and align AI use with compliance requirements.

Dvir Sasson
ABOUT THE AUTHOR
Dvir is the Director of Security Research Director, where he contributes a vast array of cybersecurity expertise gained over a decade in both offensive and defensive capacities. His areas of specialization include red team operations, incident response, security operations, governance, security research, threat intelligence, and safeguarding cloud environments. With certifications in CISSP and OSCP, Dvir is passionate about problem-solving, developing automation scripts in PowerShell and Python, and delving into the mechanics of breaking things.






%201.svg)















.svg)