MCP Security: Key Risks, Controls & Best Practices Explained

After spending over a decade in offensive security and protocol analysis, I can say with confidence that we are repeating old mistakes in new environments. The rise of Model Context Protocol (MCP) has created one of the most misunderstood exposure surfaces in modern AI architecture.
Behind the promise of seamless tool integration and agentic workflows, we have uncovered real gaps across dozens of MCP servers, from command injection to unauthenticated access. This guide draws from firsthand research, red team assessments, and practical evaluation of MCP deployments across enterprises to explain how MCP security breaks down and how to rebuild it with the right security controls in place.
Key Takeaways
The Model Context Protocol is becoming foundational to how AI systems interact with tools and services. But without rigorous security measures in place, MCP quickly turns from a productivity layer into an exposure surface. These are the core risks and lessons explored in this guide:
- Most MCP servers are deployed without basic authentication or input validation
- Prompt injection, tool poisoning, and token theft are already affecting production environments
- Malicious MCP servers are easy to spoof and often slip past trust mechanisms
- Overexposed scopes in tool descriptions enable cross-connector access and sensitive data exposure
- The lack of enforced integrity checks weakens supply chain security across MCP packages
- Poor visibility into MCP client behavior leaves organizations blind to internal misuse
- Reco mitigates MCP risk through real-time monitoring of tool usage, alerting on prompt injection and misuse, and enforcing policy-as-code to control exposed scopes and detect unauthorized paths.
What is MCP (Model Context Protocol)?
Model Context Protocol (MCP) is a message-based protocol that connects AI systems with tools, servers, and external services. It defines how structured requests and responses are exchanged to enable controlled tool execution within automated workflows. The protocol is used to pass context between components, allowing MCP clients to send instructions and receive results from MCP servers. Each MCP implementation may differ in structure, authentication, and behavior, depending on the use case and deployment environment.
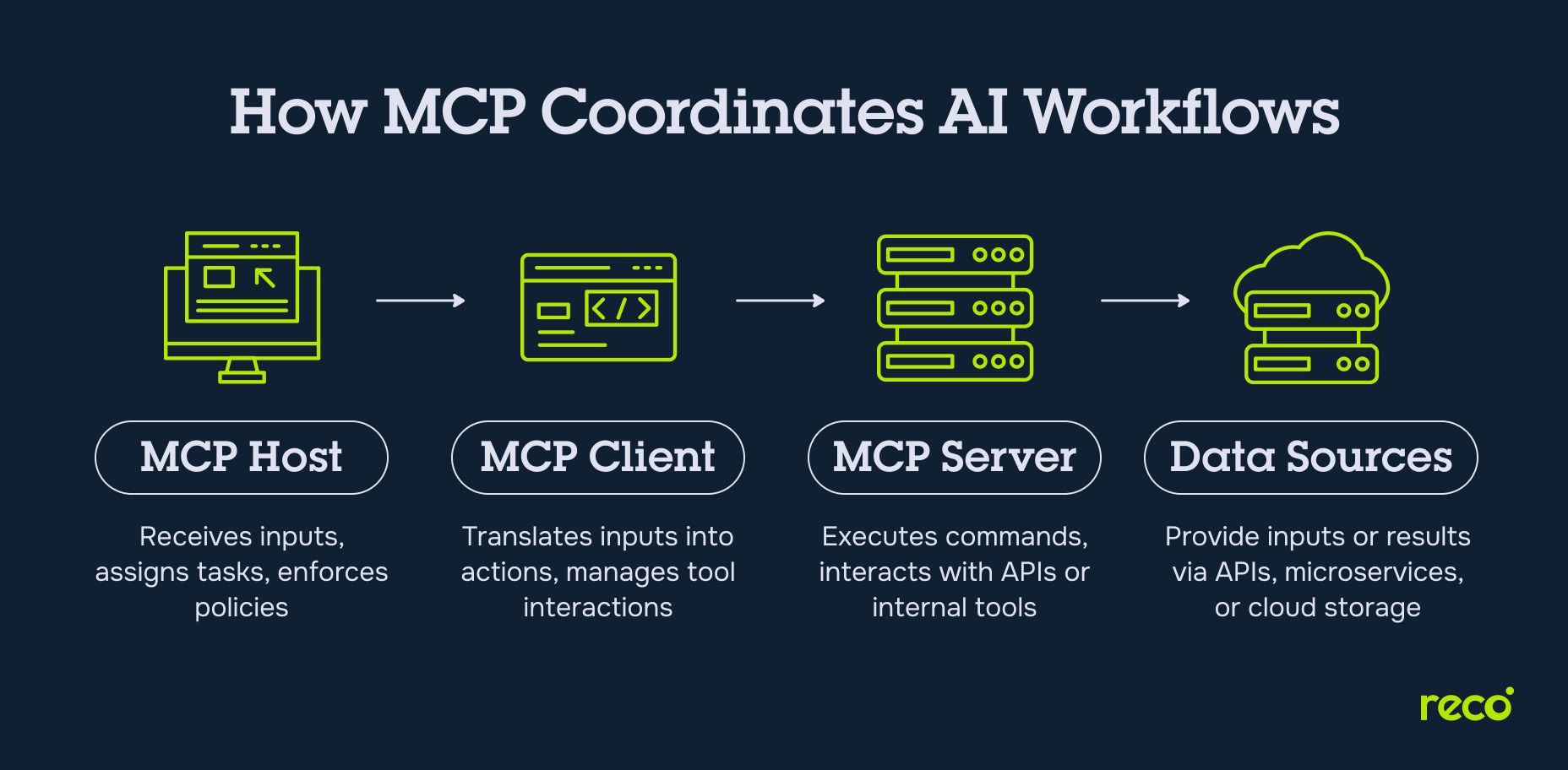
How MCP Works
MCP defines how messages are exchanged between hosts, clients, servers, and data sources within a distributed AI architecture. Each component plays a distinct role in routing tasks, executing tools, and returning results in a format that models can interpret.
MCP Hosts
An MCP host oversees the overall execution environment. It receives inputs from the model or user interface and delegates tasks to the appropriate MCP client. The host manages prompt handling, tracks tool usage across sessions, and often serves as the entry point for request validation and policy enforcement.
MCP Clients
The MCP client converts a request into a structured action and communicates directly with the MCP servers. It interprets tool instructions, manages state across calls, and handles retries or fallback logic when tool execution fails. Each MCP client is tightly linked to the host but operates independently in managing specific tool interactions.
MCP Servers
MCP servers are responsible for executing the requested actions. They expose tools, services, or connectors that the MCP client invokes. Each server runs within its own environment and may interact with external tools or internal APIs. Inconsistent authentication or permission models across MCP implementations can introduce significant security risks, especially when tool metadata is incomplete or misconfigured.
Data Sources
MCP servers frequently retrieve data or initiate workflows from connected data sources. These may include third-party APIs, internal microservices, or cloud-based storage. Without strong isolation, external systems connected in this manner may introduce attack paths or contribute to the exposure of sensitive data.
Why MCP Security Matters
MCP connects models to tools that perform real-world tasks, making it a critical layer in modern AI workflows. As adoption grows, the security model must evolve to address the risks introduced by tool interoperability, automated execution, and inconsistent implementation practices.
Shift Toward Agentic AI and Tool Interoperability
The rise of agent-driven systems has brought Agentic AI security to the forefront. These AI agents depend on MCP clients and servers to perform real-time tasks by calling external tools across SaaS, cloud, and API layers. This evolution shifts AI from passive generation to active execution. As workflows grow more autonomous, tool access becomes frequent and less predictable. Without strict controls on registration, context sharing, and execution rights, agentic systems introduce unmanaged risk. Securing the model context protocol is now foundational to operating AI safely at scale.
Expanded Attack Surface in Autonomous Workflows
In modern MCP implementations, workflows span multiple MCP servers, tools, and connected systems. Each server exposes interfaces that may accept input from autonomous agents. Without strong boundaries and authentication layers, a single exploited tool or misrouted prompt can lead to privilege escalation, lateral movement, or unauthorized data access. Significant security risks emerge when tool chains operate without proper traceability or endpoint validation.
Lack of Standardization in Early MCP Implementations
Early adopters of MCP often built custom client-server architectures tailored to internal workflows. These implementations vary in how they handle sessions, authorization, and error handling. Inconsistent design has made it difficult to evaluate risk uniformly across deployments. Without shared baselines or verification frameworks, many teams operate local MCP servers with incomplete logging, weak session handling, and poorly enforced tool boundaries, all of which create blind spots for security teams.
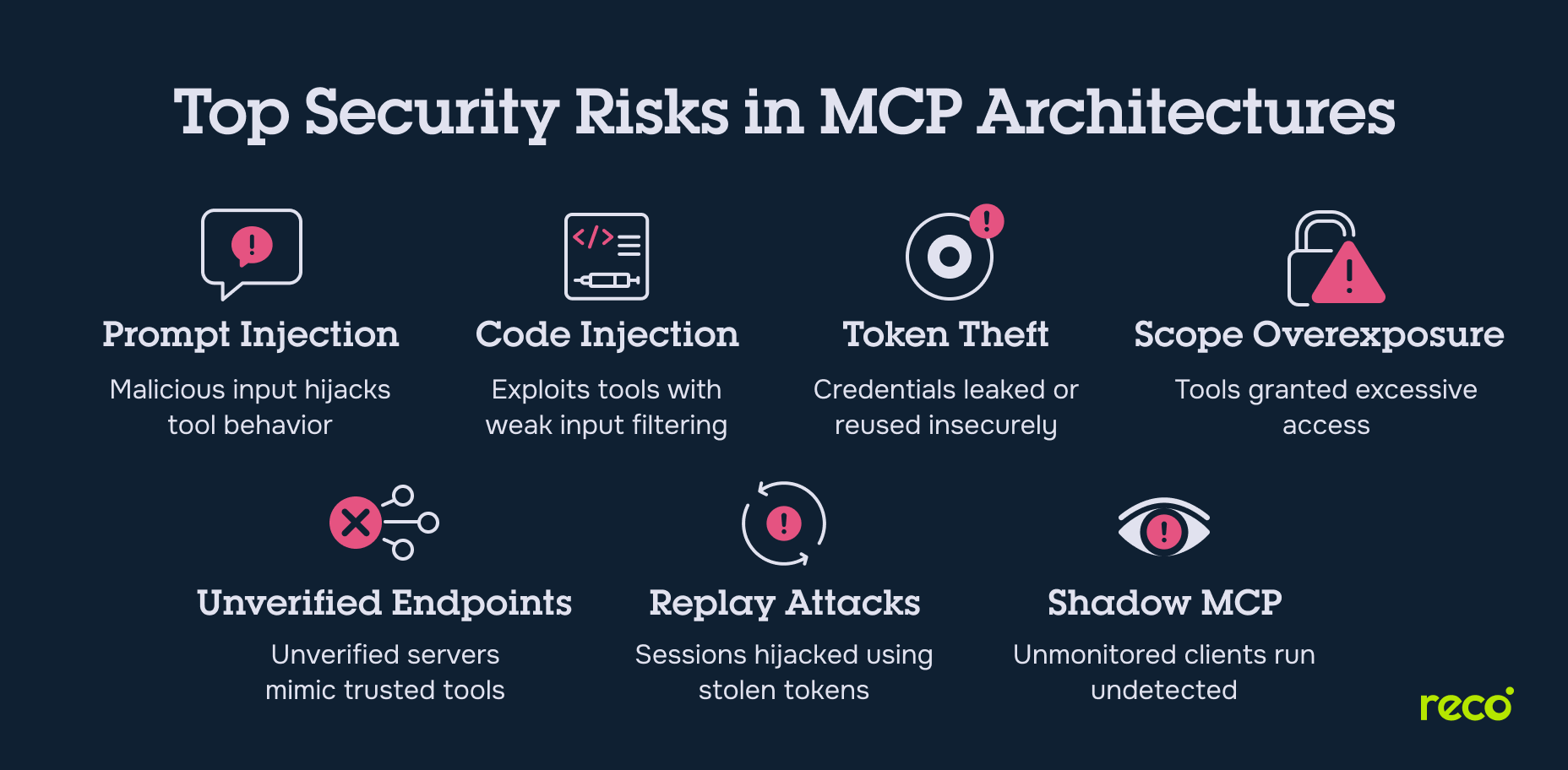
7 Core Security Risks of MCP
As MCP becomes a common layer in AI systems and SaaS workflows, attackers are increasingly targeting the unique pathways it exposes. These risks are specific to the structure of MCP and the way MCP servers, clients, and tools interact.
1. Prompt Injection and Tool Poisoning
In MCP-based architectures, prompts often carry embedded instructions for tool invocation. Malicious input can manipulate an agent's reasoning path or force unintended actions, especially when prompts are forwarded to tools without strict validation. Tool poisoning occurs when an attacker manipulates tool metadata or execution logic, injecting hidden instructions or malicious code paths that may be misinterpreted by MCP clients.
2. Command Execution and Code Injection
When MCP servers expose tools with execution capabilities, attackers can exploit unescaped input or poorly filtered parameters to inject code. This is particularly dangerous in setups where tools accept direct user input through prompts and forward it into shells, interpreters, or system commands. Without strict input sanitization, significant security risks arise from even a single endpoint.
3. Token Theft and Credential Leakage
Many MCP implementations use access tokens to interact with connected tools, cloud APIs, or external systems. If token handling is not isolated or logged improperly, these secrets may be exposed via logs, browser storage, or replayed through forged requests. Local MCP servers are especially at risk if they reuse credentials across tools or fail to scope them to specific sessions.
4. Excessive Permissions and Overexposure
Tool registration within an MCP server may include default scopes far beyond what is necessary. This creates exposure when clients invoke tools that can read, write, or delete across multiple data sources or accounts. Without security controls limiting access per task or session, users and models may gain unintended capabilities, leading to sensitive data exposure or lateral movement.
5. Unverified Third-Party MCP Endpoints
Integrating third-party tools through MCP often involves connecting to malicious MCP servers posing as legitimate services. In the absence of signature verification, these endpoints may serve malicious code, leak context to outside domains, or misreport task completion. The threat is compounded in ecosystems where tool discovery is dynamic or peer-shared.
6. Replay Attacks and Session Hijacking
Sessions between MCP clients and MCP servers often use tokens or identifiers to track interactions. When session integrity is not enforced, attackers can replay previous requests or hijack an active session by intercepting tokens, especially if session IDs are included in URLs or exposed via logs. This allows them to execute commands as the model or user without triggering behavioral anomalies.
7. Shadow MCP and Invisible Agent Activity
A Shadow MCP refers to an unmonitored or unauthorized MCP instance running within the environment. These may include MCP servers or clients operating outside official infrastructure but still interacting with tools or data. Because these components often mimic legitimate behavior, they can execute tasks, extract information, or modify logs without being detected by conventional audit tools or access policies.
Common Attack Scenarios in MCP Security
MCP-based workflows create an interconnected network of tools, servers, and agents. These connections open multiple pathways for abuse, particularly when authentication, trust boundaries, or naming conventions are not tightly enforced. Attackers exploit misconfigured components, impersonate tool providers, or manipulate registry behavior to achieve persistence or gain elevated access. The table below outlines the most prevalent attack vectors observed in live environments.
Real-World Examples of MCP Security Breaches
Understanding attack scenarios is more impactful when grounded in real-world incidents. The following examples showcase how insecure MCP implementations have been exploited in practice.
1. Anthropic’s Research into Tool Misuse via Prompt Injection
Earlier this year, Anthropic documented how prompt injection attacks could bypass internal tool restrictions by crafting embedded instructions. Their Claude model executed unauthorized commands despite policy layers. This demonstrated how insufficient control over tool invocation exposed significant security risks in early MCP implementations.
2. SuperAGI’s Open MCP Server Targeted in Package Registry Attack
An attacker uploaded a malicious MCP tool with the same name as an existing safe module in SuperAGI’s open package ecosystem. Due to a lack of namespace isolation, users who pulled the newer package executed obfuscated scripts that exfiltrated sensitive data to external domains.
3. Supply Chain Tampering in AI Workflow Agents
A research team at KU Leuven exposed a critical case where malicious MCP servers were distributed via open tool hubs. These servers altered task logs and response formatting to avoid triggering audit tools, embedding C2 instructions within generated outputs.
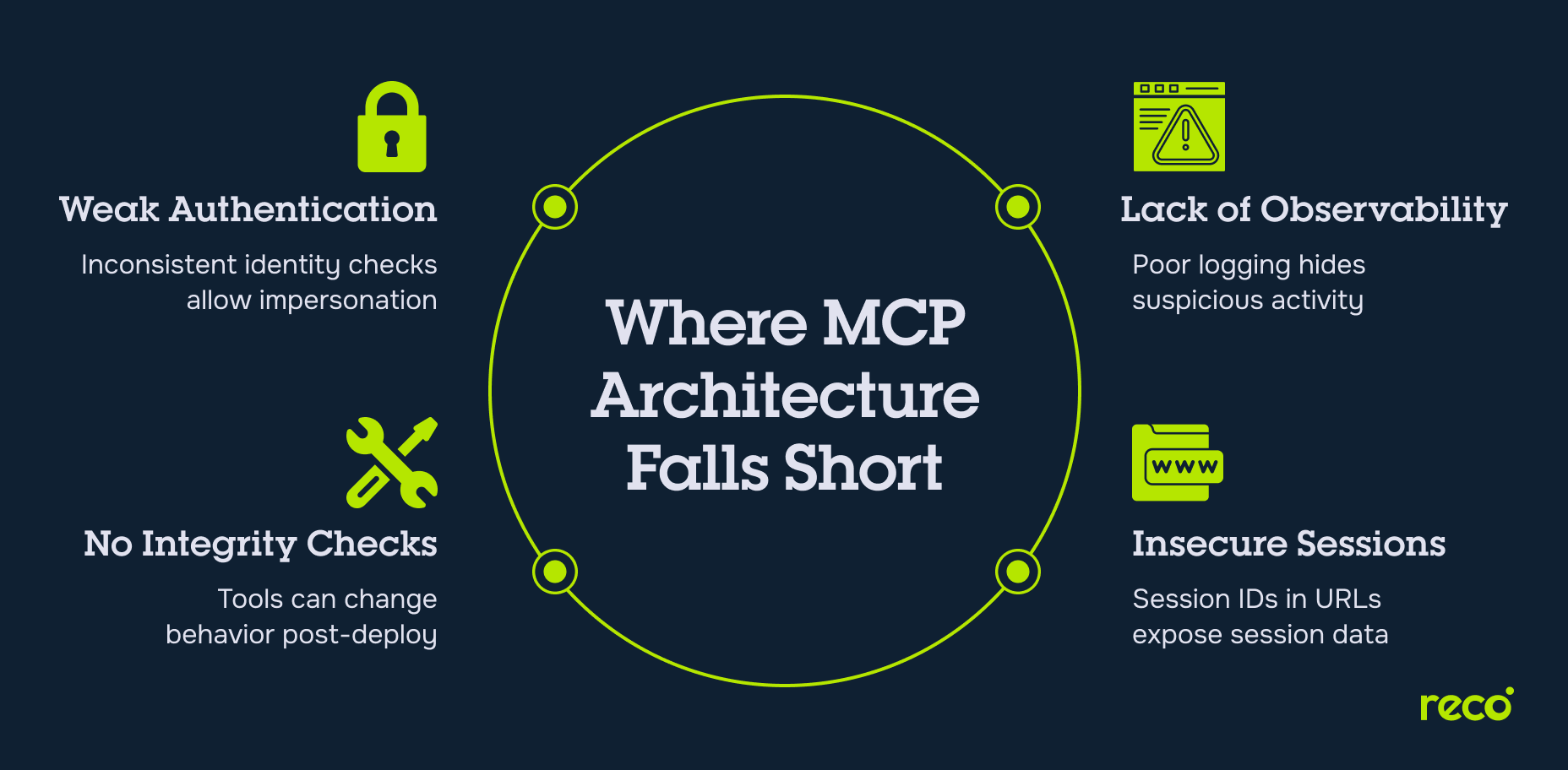
Security Weaknesses in the MCP Architecture
MCP security is only as strong as the architectural choices behind it. Early-stage MCP implementations often fail to address fundamental authentication, integrity, and observability requirements. These architectural gaps expose systems to persistent attack paths and reduce the effectiveness of detection and response.
- Lack of Enforced Authentication Standards: Many MCP servers rely on default, inconsistent, or optional authentication mechanisms. Without strict identity verification between MCP clients and MCP servers, attackers can impersonate legitimate agents or inject unauthorized tool calls into active workflows.
- Absence of Integrity and Approval Controls: The model context protocol does not enforce standardized validation or approval of tool behaviors. This makes it possible for external tools to modify their behavior post-deployment or for malicious MCP clients to exploit loosely defined scopes and action parameters.
- Poor Observability and Runtime Tracing Gaps: MCP servers often lack built-in observability features. Runtime interactions between clients, tools, and external systems are not logged with sufficient detail, reducing an organization’s ability to detect anomalies or reconstruct incident timelines.
- Use of Session IDs in URLs: Several local MCP server deployments expose session IDs within URL query parameters. This practice allows session hijacking through log scraping or passive network capture, particularly in shared or cloud environments.
6 MCP Security Best Practices to Keep Your Server Exploit-Free
Securing your MCP servers requires a layered defense strategy focused on identity enforcement, permission hygiene, activity tracing, and package integrity. The table below outlines six essential best practices that should be enforced consistently across all MCP implementations:
How Reco Closes the Gaps in MCP Server Protection
As MCP adoption scales, traditional visibility and access tools fall short in managing the dynamic, interdependent layers introduced by agentic AI systems. Reco addresses these MCP security challenges through a combination of real-time observability, policy enforcement, and automated control over permissions and tool behavior.
- Real-Time Visibility into Tool Access, Identity, and Usage: Reco continuously maps how tools, prompts, and users interact with each other inside your SaaS and cloud environments. It correlates identities to access actions across MCP clients and MCP servers, exposing hidden relationships and permission overreach.
- Alerting on Prompt Injections or Tool Misuse: Prompt injection attempts and abnormal command behaviors are detected and flagged by Reco. By observing both prompt metadata and tool response patterns, Reco helps contain high-risk instruction flows before they cause sensitive data exposure or compromise local MCP servers.
- Context-Aware SSPM for Managing Exposed Scopes and Permissions: Reco’s SaaS Security Posture Management engine provides granular control over scope assignments and exposed tool interfaces. It detects excessive or misaligned scopes in real-time and alerts teams when permissions exceed safe baselines defined by your policy models.
- Detecting Risky App Behaviors Across Interconnected SaaS and Cloud Tools: Reco analyzes behavioral drift and anomaly signals across MCP clients, third-party external tools, and integrated platforms. This lets teams detect command chains and tool actions that could lead to supply chain security failures or cross-environment escalation.
- Enforcing Policy-as-Code for Tools Connected via MCP: Reco enables the application of identity-based, environment-aware policies to all tool interactions. Teams can define which MCP clients are allowed to run specific actions, restrict tool access by environment, and enforce time-bound or role-specific limits, all as code.
- Auditing Session and Access History to Flag Abuse or Drift: By logging every access request, command, and tool execution, Reco offers a complete audit trail of MCP activity. This allows teams to trace session behavior, detect unauthorized reuse of tokens, and identify MCP servers behaving outside expected parameters.
- Blocking Orphaned, Overprivileged, or Shadowed MCP Paths: Reco automatically detects unused or abandoned MCP connections and flags them for removal. It identifies orphaned tools still registered in MCP configurations, shadow MCP clients acting outside normal workflows, and overprivileged endpoints lacking clear business justification.
Future of MCP Security
As the adoption of the model context protocol accelerates across AI systems, its security model must evolve to address more complex agentic workflows, regulatory requirements, and threats emerging from interconnected SaaS and cloud environments. The future of MCP security will demand stricter policy enforcement, cryptographic improvements, and architectural innovation.
Human-in-the-Loop Requirements for Sensitive Tasks
For workflows involving access to sensitive data or systems, AI agents operating through MCP clients will need embedded checkpoints that require human approval before proceeding. This could include biometric confirmation, physical presence validation, or multi-person review flows. These guardrails are essential to prevent autonomous agents from executing high-risk actions without oversight.
Runtime Policy Enforcement and Session Validation
Static permission models are insufficient for dynamic, tool-based interactions. Next-generation MCP servers will need runtime enforcement mechanisms that evaluate the current state, identity, and risk level before executing commands. This includes validating session context continuously and enforcing zero standing privileges.
Post-Quantum Cryptography for Context and Session Data
As MCP becomes foundational in agent-based orchestration, the cryptographic integrity of session tokens, tool metadata, and inter-agent messages becomes critical. Post-quantum cryptography will play a key role in protecting the long-term confidentiality and integrity of data flowing through model context protocol implementations.
Federated Approval Frameworks for Cross-Tool Workflows
Multi-agent toolchains often involve multiple organizations, identity domains, or data control zones. Federated approval frameworks, where permissions and execution rights are distributed and conditionally granted across participating MCP servers, will help enforce shared security controls and maintain accountability across distributed systems.
Conclusion
MCP security requires immediate action. As the model context protocol becomes foundational in AI systems and SaaS architectures, its expanding surface introduces significant security risks. Mismanaged MCP servers, permissive clients, and unchecked tool paths create exposure that traditional methods cannot contain. Organizations that succeed will treat MCP as a dynamic security domain, adopting runtime enforcement, federated approvals, and context-aware monitoring to track every tool, session, and request. The attack surface is active, and it must be secured accordingly.
What’s a “Shadow MCP” and why is it dangerous?
A Shadow MCP is an unauthorized MCP instance operating outside governance, capable of executing tools or exfiltrating data without audit trails or oversight. This lack of observability poses significant security risks, especially when connected to external tools or unmanaged workflows.
How do I know if my MCP setup is overexposed?
Signs of overexposure include overly permissive tool scopes, unverified third-party endpoints, unused or orphaned tool paths, and MCP servers accepting commands without authentication. Frequent unexplained sessions, absence of prompt-level logging, and lack of approval controls are also indicators that your implementation may be too open.
What are the biggest risks with early-stage MCP setups?
Early MCP implementations often lack enforced authentication, structured permissions, and runtime policy validation. These gaps create openings for prompt injection, token theft, session hijacking, and unauthorized command execution. Without signed MCP packages or scoped access, systems become prone to misuse and silent compromise.
Do I need to secure both the MCP servers and clients?
Yes. Securing only the MCP server is not sufficient. MCP clients can request tools, send data, or initiate tasks. If a compromised or misconfigured MCP client connects, it may exploit server-side logic or trigger unintended workflows. Strong authentication and logging are essential on both sides of the client-server architecture.
How does MCP differ from traditional API security?
Traditional API security focuses on fixed endpoints with predefined inputs. MCP introduces dynamic execution across tools and agents using contextual prompts and scoped permissions. This model context protocol requires real-time validation, session awareness, and full visibility into every tool invocation and response, which goes beyond the static controls of conventional APIs.

Tal Shapira
ABOUT THE AUTHOR
Tal is the Cofounder & CTO of Reco. Tal has a Ph.D. from the school of Electrical Engineering at Tel Aviv University, where his research focused on deep learning, computer networks, and cybersecurity. Tal is a graduate of the Talpiot Excellence Program, and a former head of a cybersecurity R&D group within the Israeli Prime Minister's Office. In addition to serving as the CTO, Tal is a member of the AI Controls Security Working Group with the Cloud Security Alliance.






%201.svg)















.svg)