SSO Implementation: Key Steps, Benefits & Best Practices
Key Takeaways
- SSO Reduces Password Fatigue and Centralizes Authentication: Single sign-on enables users to access multiple applications with one login, simplifying user experience and consolidating authentication control through a central identity provider.
- Seven Key Steps Guide Successful SSO Implementation: These include defining business goals, selecting an identity provider, choosing appropriate protocols, configuring metadata, integrating service providers, setting up error handling, and rolling out with continuous monitoring.
- Misconfigurations Pose Critical Security Risks: Common issues like clock sync mismatches, weak session timeouts, insecure redirect URIs, and overly broad permissions can undermine SSO security and disrupt access.
- SSO Introduces Risks like Single Points of Failure and Credential Compromise: Centralized access heightens the impact of service downtime or stolen credentials, making redundancy, MFA, and active monitoring essential.
- Reco Enhances Visibility and Control Over SSO Environments: It detects shadow access, flags misconfigurations, monitors for takeover attempts, automates policy enforcement, and enables risk-based access reviews across SaaS applications.
What is Single Sign-On
Single sign-on (SSO) is an authentication method that enables users to access multiple applications using a single set of credentials. Instead of entering credentials separately for each service, users authenticate once through a central identity provider (IdP). The IdP confirms their identity and issues a secure token that connected applications, called service providers (SPs), accept for access. This reduces password fatigue, streamlines access, and centralizes authentication control.
How Single Sign-On Works
SSO works by establishing a trust framework between the identity provider and the applications a user needs. When a login request occurs, the process typically follows these steps:
- Access Request: The user tries to open an application (SP).
- Redirection: The application routes the request to the identity provider.
- Authentication: The IdP verifies the user’s identity, often using credentials and multi-factor authentication.
- Token Issuance: A secure token (such as a SAML assertion or OIDC ID token) is generated.
- Validation: The application checks the token’s authenticity and source.
- Access Granted: Once confirmed, the user can enter the application without re-entering their credentials.
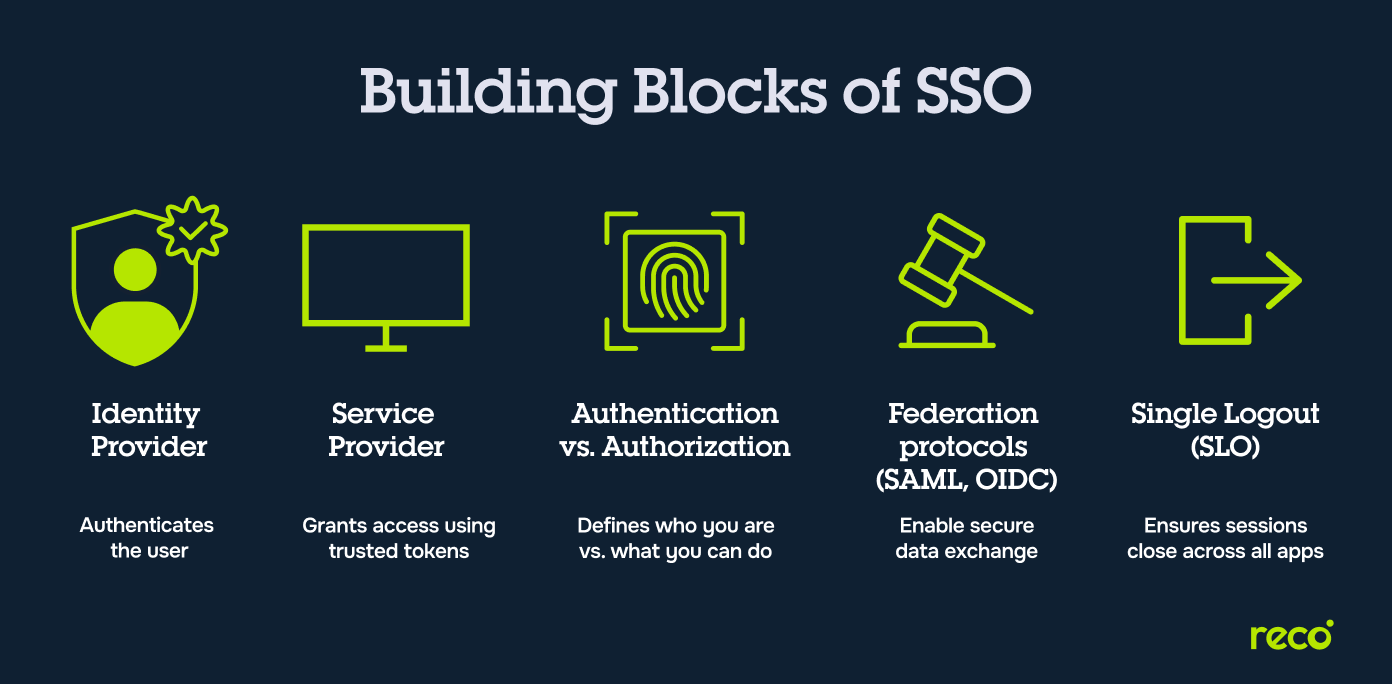
Core Concepts in Single Sign-On
To understand SSO in practice, it helps to know the main building blocks that support it. These concepts define how identities, applications, and trust are managed.
- Identity Provider (IdP): The system that authenticates a user’s identity and issues tokens or assertions to confirm that authentication.
- Service Provider (SP): The application or service that relies on the IdP for authentication instead of storing user credentials itself.
- Authentication vs. Authorization: Authentication verifies who a user is, while authorization determines what that user can do once logged in.
- Federation and Trust Relationships: Agreements and standards (such as SAML or OpenID Connect) that allow IdPs and SPs to securely exchange authentication data.
- Single Logout (SLO): A mechanism that ensures logging out from one service also ends the session across all connected applications.
7 Key Steps in SSO Implementation
Implementing Single Sign-On is a structured process that connects security goals with business needs. The following seven steps outline how organizations should move from planning to full adoption:
- Define Business Goals and Use Cases: Start by clarifying why SSO is needed. Goals may include improving employee productivity, reducing password fatigue, or strengthening user authentication across SaaS applications. Document concrete use cases, such as HR platforms, collaboration tools, or customer-facing portals, to guide the entire rollout.
- Select Your Identity Provider: An identity provider (IdP) is the backbone of an SSO system. Choosing the right IdP involves evaluating support for standards, compatibility with existing infrastructure, scalability, and security features such as multi-factor authentication.
- Choose Protocols and Standards: SSO solutions rely on established standards like SAML, OAuth 2.0, or OpenID Connect. The choice depends on the ecosystem of applications and security requirements. For example, SAML is widely used in enterprise SaaS environments, while OAuth and OpenID Connect are common in modern web and mobile apps.
- Configure the IdP and Metadata: Once the IdP is selected, it must be configured with organizational policies, user attributes, and metadata exchange. Metadata files establish trust between the IdP and each service provider, ensuring authentication requests are validated properly.
- Integrate and Test Service Providers: Each application that participates in SSO must be integrated with the IdP. Testing at this stage is critical to confirm that login flows, user attributes, and authorization data work as expected across different services.
- Set Up Error Handling and Logging: Failures in authentication can frustrate users and create security gaps. A proper SSO implementation includes centralized logging, audit trails, and error handling mechanisms that provide clear feedback to both users and administrators.
- Launch Rollout and Monitor Continuously: A phased rollout minimizes disruption. Start with a pilot group, gather feedback, then expand to the wider organization. After launch, continuous monitoring ensures uptime, detects anomalies, and validates that the system aligns with evolving access management needs.
Common SSO Protocols
Single Sign-On relies on widely adopted protocols that define how identity, authentication, and authorization are exchanged between systems. Each protocol serves a different purpose, and selecting the right one depends on the organization’s application landscape and security requirements.
SAML (Security Assertion Markup Language)
SAML is the most established enterprise standard for SSO, particularly in SaaS and corporate environments. It enables identity providers to issue XML-based assertions that authenticate users and pass attributes to service providers. Its strength lies in mature support across enterprise applications and its ability to integrate with legacy systems. However, it can be heavy and less developer-friendly compared to newer frameworks, making it better suited for enterprise IT rather than modern consumer-facing apps.
OAuth 2.0
OAuth 2.0 is an authorization framework that focuses on delegated access rather than direct authentication. It allows applications to obtain limited access to user resources hosted on another service without requiring users to share credentials. Widely used in consumer ecosystems such as Google, Facebook, and Microsoft logins, OAuth is highly flexible but leaves authentication to additional layers, which can introduce complexity if not implemented with best practices.
OpenID Connect (OIDC)
OIDC builds on OAuth 2.0 by adding an identity layer through standardized ID tokens, typically in JSON Web Token (JWT) format. This makes it suitable for modern applications that require both authentication and authorization in a single flow. Its lightweight, JSON-based design makes it developer-friendly, cloud-native, and adaptable to mobile and web apps. OIDC has effectively become the go-to choice for modern SaaS environments, often replacing SAML for new deployments.
SCIM (System for Cross-domain Identity Management)
Although not an authentication protocol, SCIM complements SSO by standardizing how user identities are provisioned, updated, and de-provisioned across services. It ensures that when a user joins, leaves, or changes roles, those updates propagate automatically to connected applications. In practice, SCIM is critical for maintaining security hygiene in SSO implementations by preventing orphaned accounts and reducing the risk of unauthorized access. Many organizations pair SCIM with modern IAM tools to automate provisioning and ensure that identity updates flow consistently across all connected applications.
Benefits of Implementing SSO
Single Sign-On offers more than just convenience. It improves both the end-user experience and the way organizations handle identity and access across applications. The table below highlights the key benefits and why they matter.
Good to Remember
SSO audit logs often omit context like role changes or third-party access. Cross-link with app-level logs to avoid blind spots.
SSO Challenges and Risks
While Single Sign-On streamlines authentication, it also introduces challenges that organizations must address to maintain security and reliability. Below are the most common risks associated with SSO:
- Single Point of Failure Concerns: Centralizing authentication creates efficiency but also risk. If the SSO service fails or experiences downtime, users can be locked out of every connected application, halting workflows across the organization. High availability and backup strategies become critical to mitigate this issue.
- Security Risks If Credentials are Compromised: SSO magnifies the damage of credential theft. A single set of stolen or phished credentials can provide attackers with access to multiple applications at once, increasing the scale of a potential breach. This makes strong authentication and proactive monitoring essential.
- Compatibility and Integration Issues: Many modern SaaS platforms support SSO, but legacy applications and some niche tools may not. Inconsistent integration leads to fragmented user experiences and added administrative overhead. IT teams often need to balance full coverage with practical workarounds.
- User Resistance and Change Management: Even when technically sound, SSO rollouts can face pushback from employees. Users accustomed to managing separate logins may distrust or misunderstand centralized access, slowing adoption. Clear communication, training, and phased implementation help address these challenges.

Best Practices for Secure SSO Implementation
Implementing Single Sign-On effectively requires more than just centralizing logins. To ensure security and resilience, organizations should adopt SSO best practices that strengthen authentication and reduce risk.
- Enforce Multi-Factor Authentication (MFA): Pairing SSO with MFA significantly reduces the risk of credential-based attacks. Even if a password is compromised, requiring a second factor, such as a hardware token, mobile prompt, or biometric, adds an essential security layer.
- Use Strong Session Management Policies: Poorly managed sessions can leave accounts exposed. Define strict timeout rules, limit persistent sessions, and enforce re-authentication for sensitive actions to minimize the chance of unauthorized access.
- Regularly Audit Access and Permissions: Over time, users may accumulate unnecessary access rights. Routine audits help ensure that permissions follow the principle of least privilege, closing gaps that attackers could exploit.
- Monitor for Unusual Login Patterns: Real-time monitoring of login activity can flag suspicious behavior. Alerts for anomalies such as logins from unfamiliar locations or multiple failed attempts help security teams respond quickly.
- Regularly Update Protocols and Certificates: Outdated SSO protocols or expired certificates can weaken defenses. Regularly patching, updating, and rotating certificates ensures that authentication remains secure and compliant with evolving standards.
Common SSO Misconfigurations to Watch Out For
Misconfigurations often create hidden entry points for attackers or disrupt seamless authentication. The table below highlights some of the most common issues administrators should monitor closely.
How Reco Enhances SSO Security and Visibility
While SSO streamlines access, it also introduces blind spots if not continuously monitored. Reco strengthens security by addressing the unique challenges of SSO in SaaS, providing enhanced visibility, proactive detection, and automated controls across cloud applications.
- Real-Time Visibility into All Connected Applications: Reco gives admins a live view of every SaaS app linked to the identity provider, ensuring no integration goes unnoticed and reducing the risk of hidden access points.
- Detection of Unauthorized or Shadow Access: It identifies apps and users bypassing sanctioned SSO flows, highlighting shadow access that could expose sensitive data outside approved security controls. Reco also helps identify misconfigured authentication settings across connected SaaS apps, reducing exposure to accidental security gaps.
- Continuous Monitoring for Account Takeover Attempts: Reco flags unusual login activity, MFA bypass attempts, and location anomalies to detect potential account takeover before damage occurs.
- Automated Policy Enforcement Across SaaS Apps: Security teams can define rules once and apply them consistently across all connected apps, reducing the risk of configuration drift or inconsistent enforcement.
- Risk-Based Access Reviews and Remediation: Reco helps prioritize access risks based on user roles, app sensitivity, and activity patterns, allowing teams to remove unnecessary access quickly and improve compliance.
Conclusion
Single sign-on has become an essential foundation for modern identity management. By reducing password fatigue, strengthening authentication, and centralizing access, it not only improves user experience but also enhances security and compliance. At the same time, organizations must address challenges such as integration complexity, credential risks, and user adoption to ensure that their SSO implementation delivers its full value. With the right protocols, best practices, and continuous monitoring in place, SSO evolves from a convenience feature into a strategic security layer that supports both productivity and protection.
Which protocols should I choose for my SSO environment?
Your protocol should align with your application architecture:
- SAML: Best for traditional enterprise SaaS apps.
- OIDC: Lightweight, modern, and ideal for mobile/web apps.
- OAuth 2.0: Good for delegated access but needs care for secure auth.
- SCIM: Not for auth, but essential for identity provisioning and hygiene.
Can SSO be made resilient to IdP outages?
Yes, but it takes deliberate architectural planning:
- Deploy redundant IdP nodes across availability zones.
- Use cloud-native IdPs with built-in high availability and failover.
- Cache valid tokens and implement token grace periods where supported.
- Consider limited offline access mechanisms for critical apps.
How should SSO integrate with Zero Trust architecture?
SSO is a foundational element, but not the full solution:
- Pair SSO with continuous authentication and context-based access decisions.
- Evaluate device posture, location, risk signals, and session behavior post-login.
- Use conditional access policies and integrate with identity threat detection tools.
How does SSO impact incident response workflows?
SSO centralizes identity but also compresses the blast radius:
- A single compromised credential can impact dozens of apps.
- IR teams must prioritize scope containment by quickly identifying affected sessions.
- Token revocation, forced logout, and rapid credential rotation should be automated.
- Reco can accelerate this with real-time access tracing across SaaS platforms.

Tal Shapira
ABOUT THE AUTHOR
Tal is the Cofounder & CTO of Reco. Tal has a Ph.D. from the school of Electrical Engineering at Tel Aviv University, where his research focused on deep learning, computer networks, and cybersecurity. Tal is a graduate of the Talpiot Excellence Program, and a former head of a cybersecurity R&D group within the Israeli Prime Minister's Office. In addition to serving as the CTO, Tal is a member of the AI Controls Security Working Group with the Cloud Security Alliance.






%201.svg)















.svg)