Cloud Security Configuration: Types, Tools & Best Practices

What is Cloud Security Configuration?
Cloud security configuration is the practice of setting and managing security controls, policies, and parameters across cloud resources to ensure they meet defined security standards and compliance requirements. It covers elements such as identity and access management, network rules, encryption settings, and application permissions, creating a secure baseline for operating in cloud environments.
Why Cloud Security Configuration Matters
Cloud security configuration is essential because misconfigured resources remain one of the leading causes of security breaches in cloud environments. Incorrect settings in identity and access controls, network permissions, or encryption policies can expose sensitive data and critical systems to unauthorized access. By maintaining consistent, secure configurations, organizations reduce the attack surface and ensure compliance with industry regulations. This approach also sustains a strong security posture across diverse cloud platforms and providers while staying aligned with emerging cloud security trends.
Types of Cloud Security Configuration
Cloud security configuration spans multiple control layers, each targeting a specific aspect of risk reduction and operational integrity. Addressing all of these layers consistently is essential for minimizing misconfigurations and ensuring that security measures are enforced across different cloud environments.
Identity and Access Controls
Identity and access controls define who can interact with cloud resources and what actions they can perform. Effective configurations implement identity and access management policies that enforce the principle of least privilege, require multi-factor authentication, and regularly review role assignments. Overly broad permissions increase the risk of privilege escalation and unauthorized access, making continuous policy verification essential.
Network and Firewall Rule Configuration
Network and firewall settings regulate how traffic flows into and out of cloud environments. Secure configurations restrict inbound and outbound connections to only what is necessary, block unused ports, and segment workloads using virtual networks or subnets. Misconfigured firewall rules can unintentionally expose services to the public internet, creating exploitable entry points.
Data Storage and Encryption Settings
Data storage security depends on correctly configured access permissions and encryption protocols. Cloud storage buckets, databases, and file shares should enforce encryption at rest and in transit, with key management integrated into cloud providers’ native services or third-party tools. Publicly accessible or unencrypted storage remains one of the most common sources of cloud data exposure.
Monitoring and Logging Configuration
Monitoring and logging settings determine the visibility an organization has into its cloud infrastructure. Proper configurations ensure that all critical events are logged, logs are stored securely, and alerting mechanisms are in place for suspicious activity. Disabling or misconfiguring logging can blind security teams to malicious actions or policy violations.
SaaS Application Permission Settings
Many security gaps originate from excessive permissions granted to third-party integrations in SaaS platforms. Secure configurations review and limit OAuth scopes, API tokens, and app permissions to only what is operationally necessary. Continuous monitoring of these settings prevents unauthorized access to sensitive data. It also reduces risk in hybrid and multi-cloud workflows, which is a key consideration in hybrid cloud security strategies where SaaS integrations bridge both public and private resources.
Components of Cloud Security Configuration
Cloud security configuration relies on several core components that work together to maintain consistent, compliant, and secure settings across all cloud resources. Each component addresses a specific security requirement while supporting integration with broader security operations:
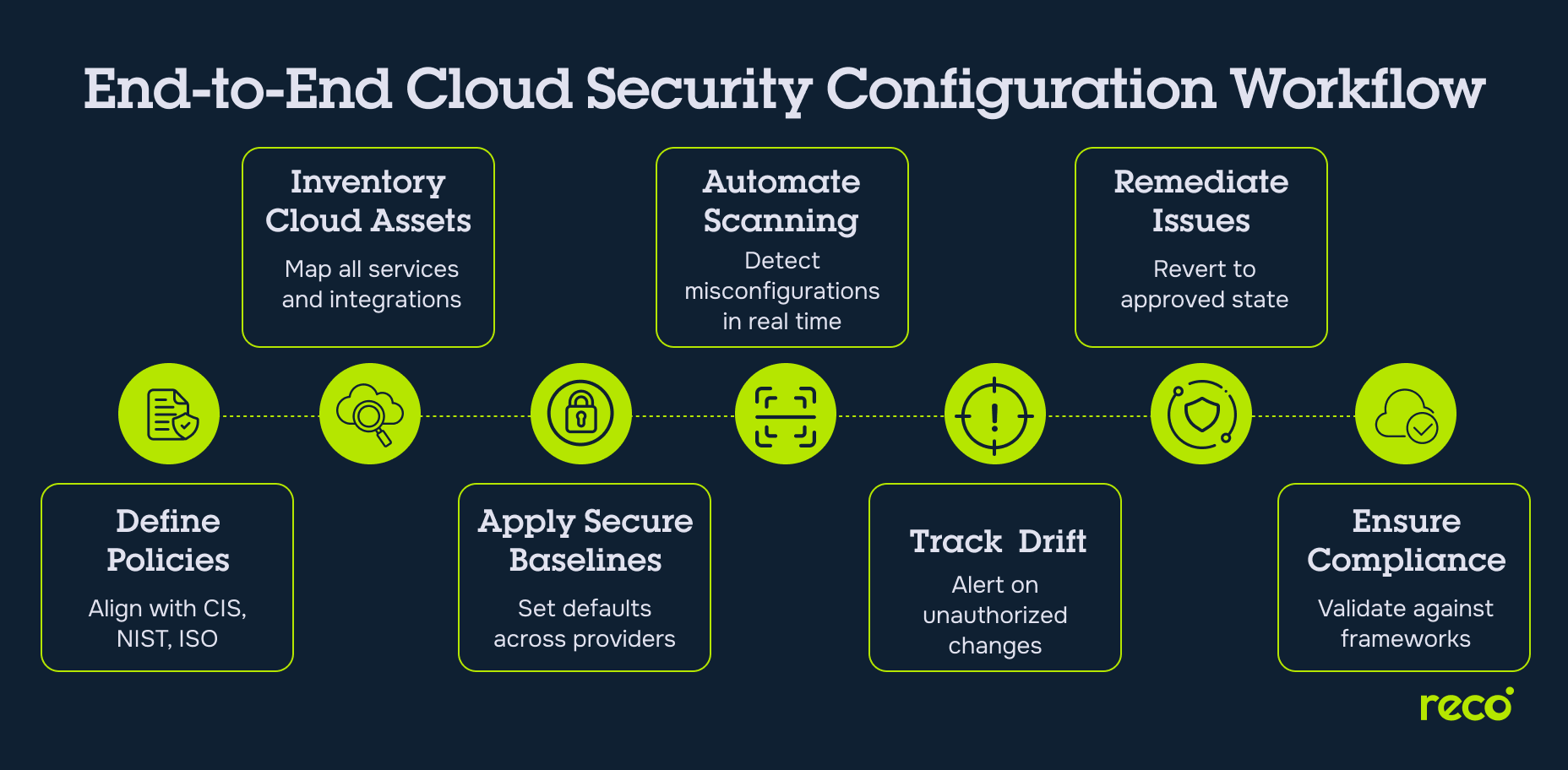
Cloud Security Configuration Process
An effective cloud security configuration process follows a structured sequence that ensures consistency, reduces the risk of misconfigurations, and maintains compliance across diverse cloud environments. Each step builds on the previous one to create a repeatable and scalable approach to securing cloud resources.
- Define Security and Configuration Policies
Establish clear, enforceable policies aligned with industry frameworks such as CIS, NIST, or ISO. These policies set the baseline for all security controls and guide configuration decisions across cloud providers. - Discover and Inventory All Cloud Assets
Map every workload, service, and SaaS integration within your cloud infrastructure. A complete inventory ensures no unmanaged or shadow assets bypass security measures. - Apply Secure Baseline Configurations
Configure resources according to the defined policies, ensuring secure defaults for IAM settings, network rules, encryption, and logging. Baselines provide a consistent starting point across all cloud platforms. - Automate Scanning and Misconfiguration Detection
Use automated tools to continuously assess configurations against approved baselines. Automation reduces manual effort and helps detect risks faster, especially in dynamic cloud environments. - Track Configuration Drift
Monitor for unauthorized or unplanned changes that deviate from baselines. Drift tracking ensures that policy violations are identified early before they impact data security or compliance. - Enforce Policy-Based Remediation
Implement automated or guided remediation workflows that revert configurations to the approved state. This maintains security posture without delaying operational needs. - Ensure Continuous Compliance
Continuously validate configurations against regulatory and organizational standards. This step helps maintain readiness for audits and aligns with a proactive cloud security checklist, ensuring that all critical configuration requirements remain in place over time.
Best Practices for Cloud Security Configuration
Applying proven best practices ensures that cloud security configuration remains effective across evolving threats, regulatory demands, and complex multi-cloud or hybrid cloud security environments:
Benefits of Effective Cloud Security Configuration
A well-implemented cloud security configuration program strengthens security operations, improves resilience, and ensures compliance across diverse cloud deployments. Its benefits extend beyond preventing misconfigurations to enabling long-term operational and business efficiency.
- Improves Security Posture and Visibility: Centralizing configuration management across cloud platforms ensures consistent enforcement of security controls, reduces attack surface exposure, and enhances visibility into every change made within the environment. Integrated monitoring and reporting allow security teams to quickly detect anomalies and respond before they escalate.
- Enhances Regulatory Compliance: Properly configured cloud environments align with established security frameworks such as CIS, NIST, and ISO, while also supporting industry-specific mandates like HIPAA or PCI DSS. Automated compliance checks reduce audit preparation time and ensure that policy enforcement is continuous rather than reactive.
- Reduces Operational Risk: Misconfigurations in identity and access management, network rules, or encryption policies are among the most common root causes of cloud breaches. Proactive configuration management eliminates these high-impact weaknesses, preventing data exposure, downtime, and costly incident response activities.
- Enables Scalable and Repeatable Processes: Standardized policies and automation enable the rapid, secure deployment of workloads across multiple cloud providers without sacrificing control. By embedding secure configuration templates into Infrastructure as Code (IaC) workflows, teams can replicate trusted setups in new projects or regions with minimal effort.
Cloud Security Configuration Challenges
Managing cloud security configuration at scale introduces operational and technical obstacles that can undermine even the most mature security programs. Addressing these challenges requires tools, processes, and skills that adapt to diverse architectures and evolving threat landscapes:
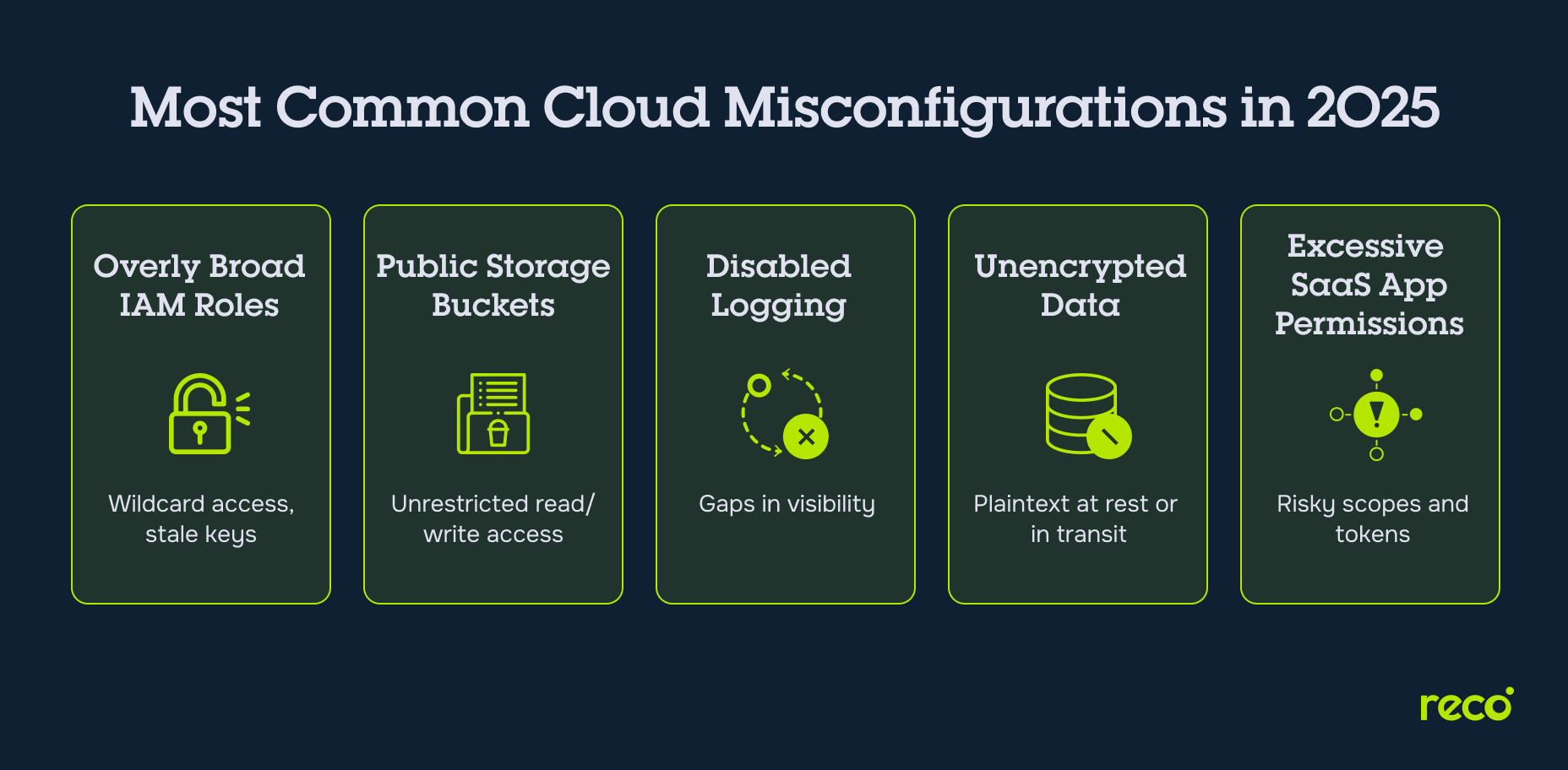
Common Cloud Security Misconfigurations to Watch For
Misconfigurations are a primary source of risk in cloud security. The patterns below recur across cloud providers and SaaS platforms, and each one has clear indicators, business impact, and straightforward controls when addressed early.
Overly Permissive IAM Roles and Groups
Broad permissions increase the blast radius of any compromised identity and enable privilege escalation. Warning signs include wildcard actions, resource scopes set to star, stale service accounts, long-lived access keys, and missing MFA on sensitive roles.
Mitigation Strategy: Tighten access management with least privilege roles, just-in-time elevation, time-bound credentials, and periodic access reviews. Enforce approval workflows for new permissions and alert on policy changes and unusual role assumptions.
Publicly Accessible Storage Buckets
Public read or write access exposes data to the internet and invites deletion, overwrite, or ransomware scenarios. Indicators include anonymous or all users' principals, bucket ACLs that allow public listing, or presigned URLs with excessive lifetimes.
Mitigation Strategy: Block public access at the account or organization level, require private defaults, and restrict bucket policies to specific identities and networks. Continuously scan for public exposure and trigger immediate remediation on ACL or policy changes.
Disabled Logging or Monitoring
Gaps in logging create blind spots that delay detection and complicate investigations. Common issues include disabled control plane logs, missing network flow logs, short retention, and logs stored in the same account that generated them.
Mitigation Strategy: Mandate organization-wide logging, ship audit logs to a hardened destination with write-once controls, and set retention that matches regulatory needs. Create coverage maps for critical services and alert if any required log source goes silent.
Unencrypted Databases or Storage Volumes
Unencrypted data at rest or in transit increases exposure risk and can break compliance commitments. Look for databases, block volumes, snapshots, and backups without encryption or with unmanaged keys, as well as services that accept plaintext connections.
Mitigation Strategy: Enforce encryption by default with managed key services, require TLS for all client connections, rotate keys on a defined schedule, and block creation of unencrypted resources. Include snapshot and backup workflows so copies inherit encryption automatically.
Excessive Third-Party App Permissions in SaaS
OAuth apps and API tokens can grant broad access to mailboxes, files, repos, or chat histories beyond operational need. Signals include high-risk scopes like full read of files or email, unused apps that retain access, and tokens without expiration.
Mitigation Strategy: Implement an app approval process, limit scopes to the minimum needed, require owner justification, and recertify app access on a schedule. Monitor token usage, revoke dormant integrations, and correlate SaaS permissions with identity and access management reviews to keep exposure low.
How Reco Delivers Identity-Aware Cloud Security Configuration
Effective configuration management requires more than just technical controls. Reco enhances this process by embedding identity context into every stage, ensuring that cloud and SaaS environments remain secure, compliant, and operationally efficient.
- Maps Identity-to-Asset Relationships Across Cloud and SaaS: Reco creates a unified view of how user, service, and machine identities interact with cloud resources and SaaS applications, enabling precise access control decisions.
- Detects Risky Configurations in Real Time: Continuously monitors for policy violations and misconfigurations, instantly flagging changes that could expose sensitive data or weaken security posture.
- Automates Policy-Based Remediation: Reco uses predefined rules to correct misconfigurations without manual intervention, ensuring consistent adherence to organizational and regulatory standards.
- Reduces Alert Noise with Business Context: Prioritizes alerts based on risk level, affected assets, and business impact, helping security teams focus on critical issues rather than low-priority findings.
- Integrates Seamlessly with Existing Security and SaaS Tools: Connects with SIEM, SOAR, IAM, and SaaS management platforms to extend security coverage and reduce operational silos.
- Supports Continuous Compliance Across Frameworks: Reco aligns configuration checks and remediation workflows with CIS Benchmarks, NIST, ISO 27001, and other compliance requirements.
Conclusion
Effective cloud security configuration strengthens defenses, limits exposure, and keeps systems aligned with compliance requirements. By combining precise identity-aware controls with automated monitoring and remediation, organizations can address risks before they become incidents. The result is a cloud environment that remains secure, compliant, and ready to support ongoing business growth, even as infrastructure and SaaS usage expand. Looking ahead, advancements in AI-driven analysis and unified security platforms will make configuration management faster, more adaptive, and better aligned with emerging cloud security trends.

Dvir Sasson
ABOUT THE AUTHOR
Dvir is the Director of Security Research Director, where he contributes a vast array of cybersecurity expertise gained over a decade in both offensive and defensive capacities. His areas of specialization include red team operations, incident response, security operations, governance, security research, threat intelligence, and safeguarding cloud environments. With certifications in CISSP and OSCP, Dvir is passionate about problem-solving, developing automation scripts in PowerShell and Python, and delving into the mechanics of breaking things.






%201.svg)















.svg)