The Salesloft-Drift Breach: Analyzing the Biggest SaaS Breach of 2025



Supply chain attacks that exploit unmonitored SaaS-to-SaaS integrations affect ten times more companies than traditional credential-based breaches. Organizations using Salesloft–Drift integrations should immediately review their SaaS environment for potential compromise and implement comprehensive SaaS security controls.
Reco's security researchers are analyzing the largest SaaS breach campaign of the year, impacting over 700 companies and counting. The team has discovered that both Salesforce and Gmail instances were compromised through the UNC6395 attack on Salesloft-Drift integrations. This represents a fundamental shift in how attackers are exploiting the SaaS Security Gap—the growing gap between what organizations can protect and what's outpacing their security.
Most victims are technology and software firms themselves, meaning any one of them could trigger a cascading supply-chain breach. This represents unprecedented risk for any company using SaaS integrations that bypass traditional security controls by default.
Reco uncovers critical security gaps that enabled the attack
On August 26th, 2025, Mandiant reported Salesforce breaches via the Salesloft–Drift integration, attributing the activity to UNC6395. Reco's research reveals that this attack succeeded because of fundamental gaps in how organizations secure their SaaS ecosystems—gaps that Dynamic SaaS Security is specifically designed to close.
There is additional evidence that this campaign was carried out by the combined forces of ShinyHunters and Scattered Spider, demonstrating the sophistication of threat actors now targeting SaaS supply chains.
Attack timeline and techniques
Attackers initially compromised the third-party sales tools Salesloft Drift, then leveraged OAuth tokens and SaaS-to-SaaS integrations to pivot into Salesforce and Google Workspace instances of numerous downstream companies. The breach demonstrates five critical attack vectors that traditional security cannot address:
- OAuth Token Exploitation: Attackers bypassed traditional authentication by abusing OAuth tokens, which provided persistent access without user interaction or MFA prompts.
- SaaS-to-SaaS Lateral Movement: Once inside Salesloft Drift, attackers exploited SaaS integrations to move laterally into connected applications across hundreds of organizations.
- Supply Chain Amplification: Instead of targeting individual organizations, attackers compromised one vendor to instantly access hundreds of customer environments—a 10x force multiplier compared to traditional attacks.
- Secrets Harvesting: Attackers specifically hunted for credentials, API keys, and secrets embedded in SaaS environments, using these to unlock additional systems.
- Integration Blind Spots: Most security tools lack visibility into SaaS-to-SaaS connections, making this attack vector invisible to traditional security measures.
Why traditional SaaS security failed
This attack succeeded because current security measures are static and cannot keep up with SaaS sprawl. They were designed for the early days of SaaS when organizations had Salesforce and a handful of other apps. The result is the SaaS Security Gap—the growing gap between what organizations can protect and what's outpacing their security.
Traditional security approaches failed to:
- Provide visibility into SaaS-to-SaaS connections
- Monitor OAuth token usage patterns across applications
- Detect cross-application threat patterns
- Identify secrets and credentials embedded in SaaS environments
- Respond to threats spanning multiple SaaS applications
How Reco's Dynamic SaaS Security Would Have Stopped Each Attack Vector
Discovery: Instant SaaS-to-SaaS Visibility
The Gap: Most organizations lack visibility into their complete SaaS ecosystem, especially third-party integrations and OAuth tokens.
How Reco Stops It: Our Discovery module instantly tracks all SaaS-to-SaaS connections, including Shadow SaaS, AI Agents, and third-party integrations. We would have immediately identified the Salesloft-Drift connection to Salesforce and Gmail, providing complete visibility into the potential attack surface.
With Reco's comprehensive app discovery covering 200+ applications, security teams would have had full context about which systems were at risk through the compromised integration.
Identity & Access Governance: OAuth Token Monitoring
The Gap: Traditional IAM solutions trust OAuth tokens by design, missing anomalous behavior from compromised tokens.
How Reco Stops It: Our Identity & Access Governance module continuously monitors OAuth token usage patterns across your entire SaaS ecosystem. We would have detected the unusual access patterns from the compromised Salesloft OAuth tokens, triggering immediate alerts about suspicious cross-application activity.
Our AI-powered Identity Agents provide 360-degree context that connects all user accounts across applications, enabling us to spot when OAuth tokens are being used in ways that don't match normal user behavior patterns.
SSPM+: Configuration Drift Detection
The Gap: Organizations struggle to maintain secure configurations across hundreds of integrated applications.
How Reco Stops It: Our SSPM+ module keeps security postures airtight within business context. We would have continuously monitored the Salesloft-Drift integration configurations, detecting any unauthorized changes or excessive permissions that could indicate compromise.
With support for 20+ compliance frameworks and automated remediation workflows, security teams would have been alerted to configuration drifts that made the attack possible.
Identity Threat Detection & Response: Cross-SaaS Policy Violations
The Gap: Most security tools can't detect threats that span multiple SaaS applications.
How Reco Stops It: Our ITDR module uses unique cross-SaaS policies to detect anomalies across all connected applications. The unusual data access patterns and secrets harvesting activities would have triggered our behavioral detection rules, providing instant alerts with full context about the attack chain.
Our 400+ out-of-the-box detection controls include specific rules for OAuth token abuse and unusual integration behavior that would have caught this attack in its early stages.
Staying Safe in the Future: Reco Recommended Actions
1. Check whether your organization has instances of Salesloft and Drift. If you identify this as so during discovery, verify whether they are connected to Salesforce, Google, or other core apps.
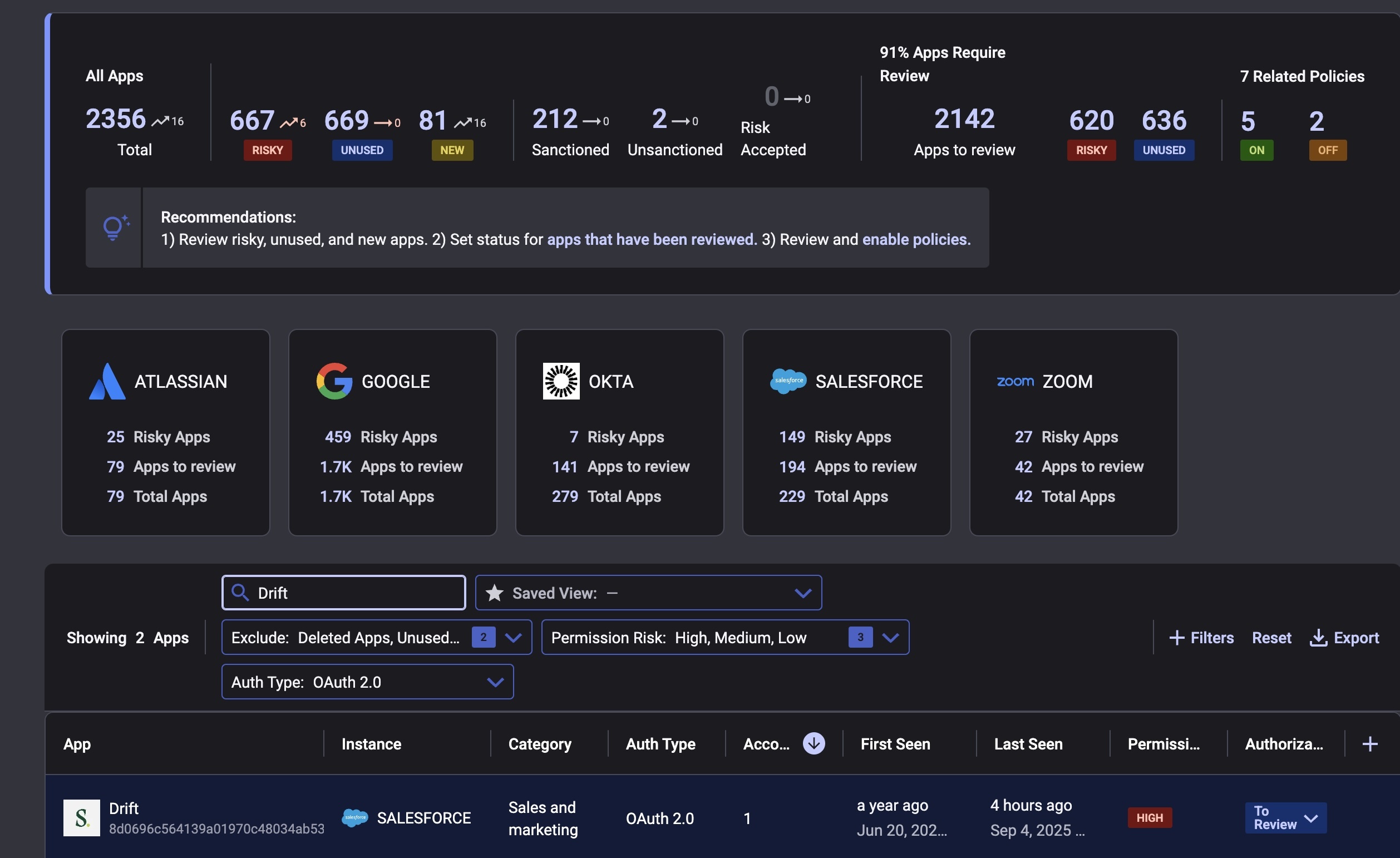
2. Verify whether your organization has been breached. Revoke tokens to these applications immediately.
3. Consult your event log for indicators of compromise activity from Salesloft or Drift. Understand impacted users and their permission level.
.png)
4. Implement continuous monitoring of OAuth tokens and third-party integrations. Regular auditing isn't enough when tokens can be compromised at any time.
.png)
5. Deploy detection rules that can spot threats spanning multiple SaaS applications. Traditional security tools that operate in silos will miss these supply chain attacks.
.png)
6. Actively scan for and remove secrets, API keys, and credentials from SaaS environments. These embedded secrets become stepping stones for attackers.
The Bottom Line
The Salesloft-Drift breach wasn't just a single vendor compromise, it was a demonstration of how interconnected SaaS ecosystems can amplify attacks beyond anything we've seen before. Supply chain attacks that exploit unmonitored SaaS-to-SaaS integrations affect ten times more companies than traditional credential-based breaches.
That's where Dynamic SaaS Security comes in.
Reco's Dynamic SaaS Security Platform would have provided the visibility, governance, and real-time threat detection needed to stop this attack at multiple points:
- Discovery of the risky SaaS-to-SaaS connection
- Identity governance monitoring OAuth token usage
- Posture management detecting configuration weaknesses
- Threat detection spotting unusual access patterns
The SaaS Security Gap is real, and it's growing every day. But with the right approach—one that evolves with your SaaS environment rather than falling behind it—attacks like this become preventable. Register for our upcoming product demo on September 30 at 9AM PST/12PM EST, we'll analyze the recent Salesloft breach and provide guidance on how to use Reco to prevent and detect similar breaches.

Gal Nakash
ABOUT THE AUTHOR
Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.

Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.



%201.svg)
.png)

















.svg)