ShinyHunters Data Breach vs. SaaS: Why Dynamic Security Matters



ShinyHunters is a notorious cybercrime group that has resurfaced with a new playbook of SaaS-focused attacks. Known for monetizing stolen data on underground forums since 2020, ShinyHunters historically breached companies by stealing credentials and databases.
Recently, however, they’ve shifted tactics to aggressive social engineering, mirroring methodology of the Scattered Spider group. Instead of exploiting software vulnerabilities, ShinyHunters now exploits human trust, targeting the underbelly of third-party SaaS platforms through impersonation and phishing.
In mid-2025, a wave of breaches struck companies like Google, Workday, Pandora, Cisco, Chanel, and others, all tied together by one common thread: the attackers leveraged access to these firms’ Salesforce CRM or similar cloud systems.
Below, we look at what happened in the Google and Workday breaches, examine techniques ShinyHunters used, and demonstrate how a dynamic SaaS security approach (like Reco’s) could have prevented each technique from succeeding.
What Happened in the Google & Workday Breaches?
In June 2025, Google revealed that attackers accessed one of its Salesforce cloud databases, compromising contact information for Google’s customers. Around the same time, other global brands, from airlines to luxury retailers, quietly disclosed similar incidents involving unauthorized access to data stored in their Salesforce instances.
Then in August, Workday (a leading HR and finance SaaS provider) confirmed that it too fell victim to a social engineering attack on a third-party CRM platform. Workday discovered on August 6th that cybercriminals had accessed a customer support database containing business contact information (names, email addresses, phone numbers). Thankfully, no sensitive customer HR data or internal systems were touched.
Workday's investigation revealed the intrusion stemmed from deception: attackers posed as internal HR personnel over the phone and convinced an employee to grant them access. This matches the pattern Google’s security team had identified: the culprits, traced to ShinyHunters, relied on voice phishing (vishing) and fraudulent OAuth access to infiltrate Salesforce environments.
ShinyHunters didn’t hack Salesforce’s infrastructure directly; they tricked people into letting them in, a strategy that led to multiple high-profile data breaches across industries.
Technique 1 - Voice Phishing & Impersonation
ShinyHunters’ primary weapon is voice phishing, or vishing. By calling employees and pretending to be IT support, they exploit human trust to obtain credentials or persuade users into carrying out risky actions.
In Google’s case, attackers talked an IT service desk into resetting a Salesforce password, bypassing normal security checks. In other cases, they’ve cold-called staff at various companies, using charm or urgency to get one person to lower the drawbridge.
ShinyHunters has even boasted about using AI generated voices to mask their identity, making it harder for authorities to trace them. This approach preys on the weakest link, people, and it’s effective. No malware needed, no zero-day exploits, just convincing lies, persistence, and perhaps a bit of background research on who to target.
How Identity Threat Detection and Response Helps
While no technology can eliminate human gullibility, an identity-first security platform like Reco adds layers of defense even when an employee is tricked. Reco’s identity threat detection and response (ITDR) capabilities monitor for anomalous identity activities – for example, an unexpected password reset, a sudden role change, or a new device logging into Salesforce after a suspicious phone call.
This context-aware monitoring means that even if an attacker tricks someone into a credential reset, Reco would catch the out-of-policy action or login almost immediately, flagging it as high-risk. Security teams would get instant alerts on potential account compromise, enabling them to intervene before the attacker can proceed.
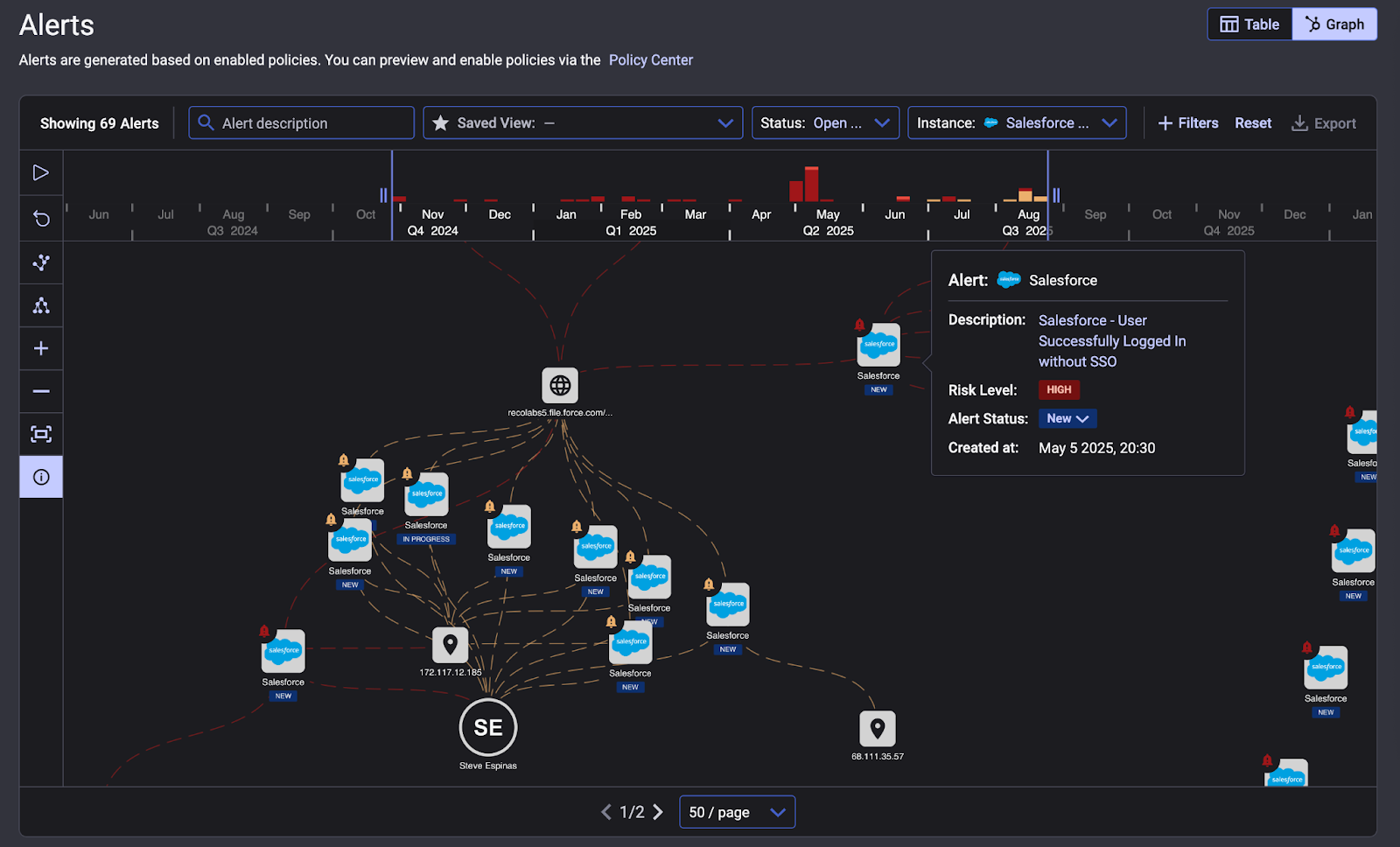
Technique 2 - Malicious OAuth App Installation
After tricking an employee, ShinyHunters move to the second phase of their attack, quietly inserting a malicious OAuth application into the target’s Salesforce environment.
The cybercriminals often distributed a trojanized version of Salesforce’s data loader tool, essentially a fake app that an employee installs or authorizes, thinking it’s legitimate. Once the employee grants it access, the app is treated as a connected application with API permissions inside the company’s Salesforce org.
This is a clever method: rather than stealing the user’s credentials outright, the attackers obtain an OAuth token (or connected app session) that gives them direct, ongoing access to Salesforce data without raising immediate alarms.
The victim might download what they believe is an official Salesforce integration or support tool (the fake data loader), log into it, and unknowingly authorize the attackers’ app to read data. With that foothold, the criminals can use Salesforce’s APIs to query and download vast amounts of data, which is exactly what they did.
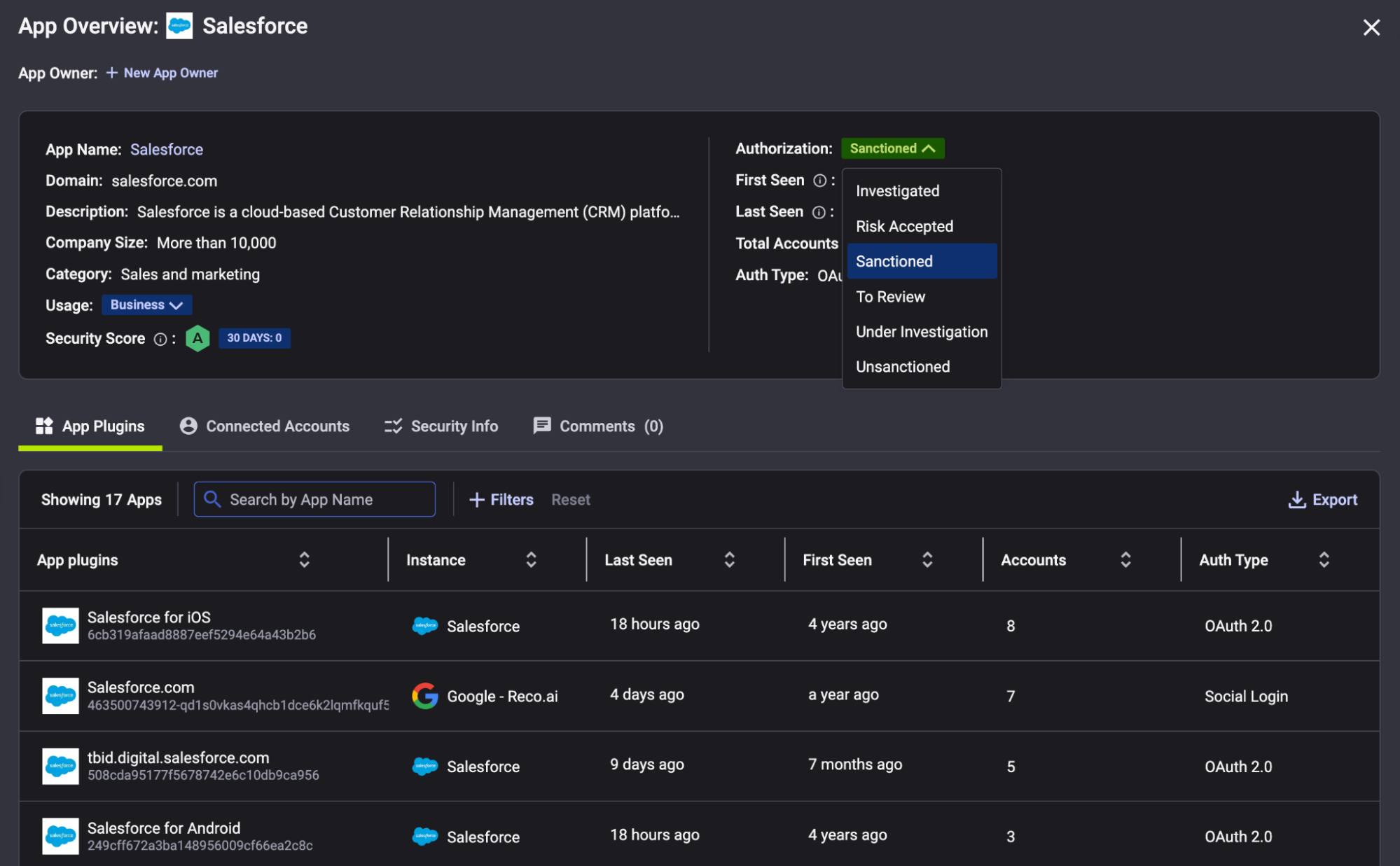
How SaaS-to-SaaS App Discovery Helps
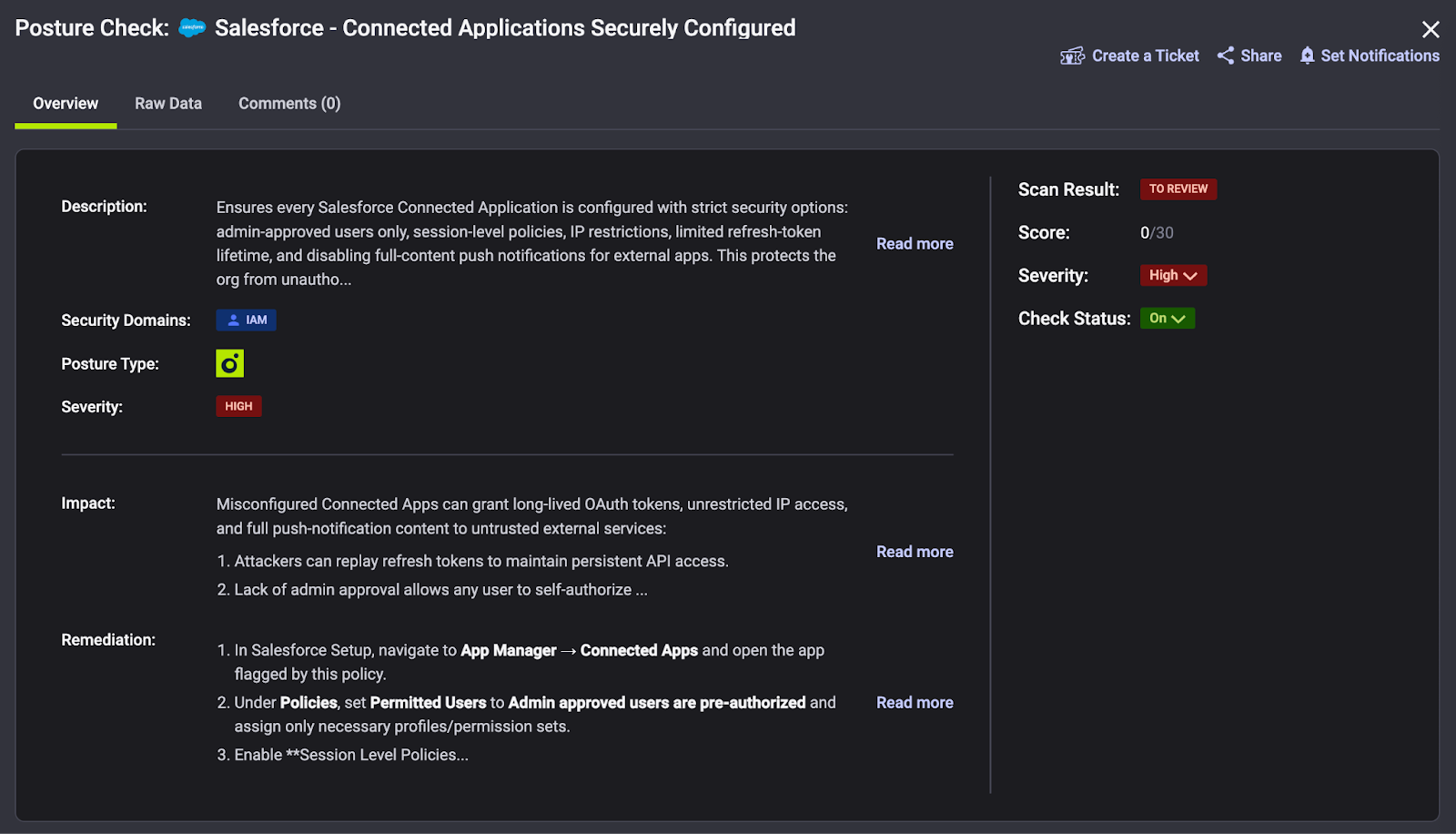
The key to stopping this phase is tight control of third-party app access. Reco’s platform is built to give security teams a complete view of your Salesforce environment, including which integrations and connected apps are present, who authorized them, and what data they can access.
Reco identifies external apps or partners with access and flags those that are suspicious or not approved. This means the moment an employee attempts to authorize a new connected app, Reco’s governance controls could require admin approval or at least alert the security team.
This kind of SaaS app governance would likely have stopped ShinyHunters in their tracks, the fake app would never have been allowed to connect in the first place, or it would have been caught before any data was pulled.
Even if the malicious app somehow got a foothold, Reco’s ITDR would quickly catch the abnormal data activity. Remember, a Salesforce data loader (real or fake) bulk-downloading thousands of contact records is not an everyday occurrence for most users. Reco’s analytics watch for exactly those anomalies: large exports, unusual query patterns, or data access at odd hours, and would trigger immediate alerts on detecting a potential data exfiltration attempt.
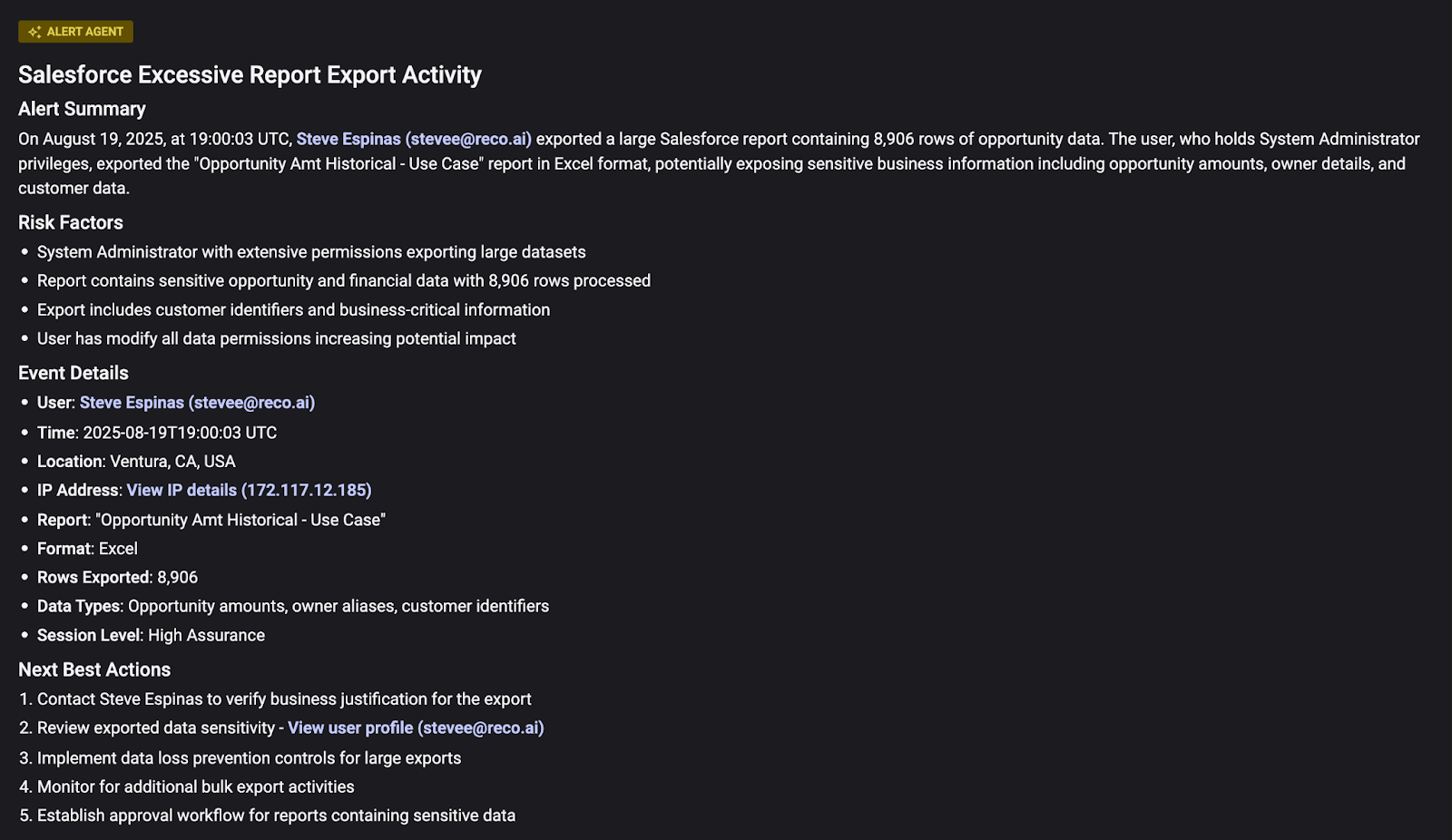
With such an alert, defenders could revoke the rogue app’s access token and lock down the account, cutting off the data theft mid-stream. This quick response is important. ShinyHunters managed to stay inside Google’s Salesforce data for only a small amount of time before access was cut off, illustrating how fast detection can limit the damage.
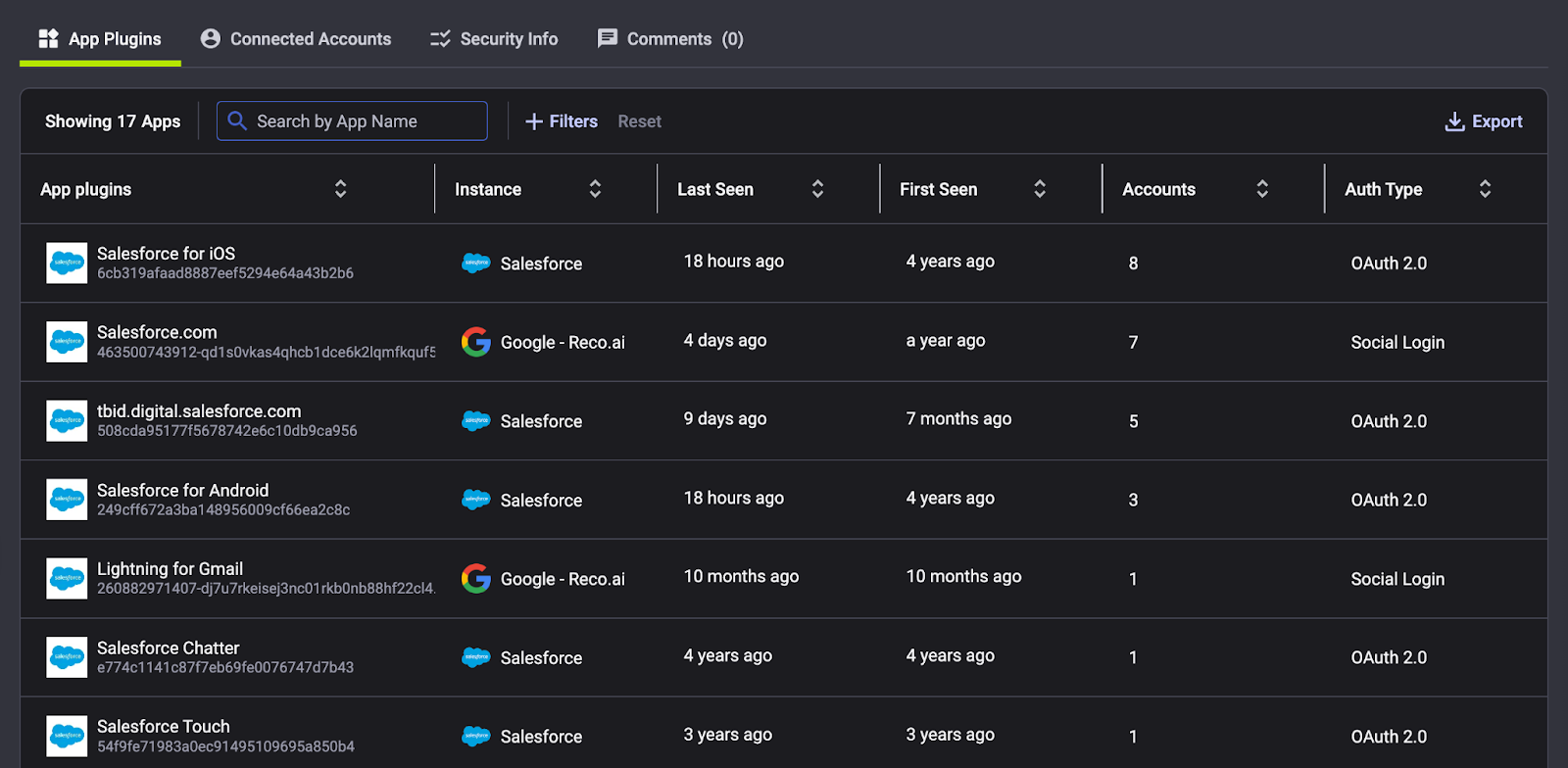
Reco’s posture management would have also shown the misconfigurations that ShinyHunters exploited. One reason these attacks succeeded is that many Salesforce orgs allowed end-users to authorize new connected apps by default. A platform like Reco helps enforce least-privilege and good configuration hygiene, for example, ensuring that only admins can add integrations, and that OAuth tokens only have the minimum scopes needed.
Take Your Next Steps With Reco
The ShinyHunters campaign against Salesforce customers gives security teams a harsh truth: your organization’s SaaS data is only as secure as the people and integrations that can access it.
When threat actors exploit human trust, via convincing vishing calls, phishing websites, and fraudulent app integrations, even the best primary security controls can be bypassed. This is where a dynamic, context-aware SaaS security solution becomes indispensable.
Reco's platform is specifically designed to close these gaps with its AI driven knowledge graph and multifaceted approach (discovery, posture management, identity governance, and threat detection).
It constantly shows SaaS-to-SaaS connections and shadow apps that cybercriminals could misuse. To ensure that users only have access to what they actually require, it also enforces identity and access management as well.
To help organizations navigate social engineering attempts targeting SaaS apps such as Salesforce, Google and Workday, the Reco Threat Research team has put together this helpful guide.
Book a demo or start a free trial at reco.ai today.

Gal Nakash
ABOUT THE AUTHOR
Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.

Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.



%201.svg)
.png)


















.svg)