As organizations increasingly rely on Zoom for collaboration, IT administrators must ensure that every virtual meeting remains secure and compliant. Zoom has evolved rapidly in response to growing cybersecurity concerns. With features ranging from end-to-end encryption to admin-controlled permissions, it's powerful but only if configured correctly. IT admins must understand how Zoom handles identity, data, access, and third-party integrations to build a secure foundation.
This guide walks IT teams through securing Zoom step-by-step using best practices and configurations.
Despite significant improvements in Zoom’s security architecture over the past few years, certain vulnerabilities and misconfigurations still pose risks, especially in enterprise environments. Understanding these vulnerabilities is critical for IT administrators who are responsible for safeguarding user sessions, organizational data, and maintaining compliance.
Below are the most prevalent Zoom security vulnerabilities IT admins should be aware of:
Zoom bombing occurs when uninvited individuals gain access to a meeting and disrupt it, often with offensive or inappropriate behavior. This typically results from meetings being publicly shared without sufficient protection, like passwords or waiting rooms.
Root Causes:
Mitigation Steps:

Zoom meeting security settings panel with options to enable meeting passcodes, waiting rooms, and authentication requirements for participants.
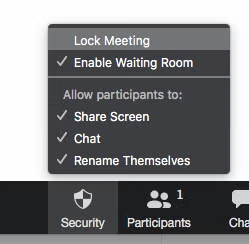
Zoom's in-meeting security menu with options to lock the meeting, enable waiting room, and manage participant permissions.
Users often set weak or reused passwords for their Zoom accounts. Without policies in place, attackers can use credential stuffing techniques (using leaked passwords from other services) to gain unauthorized access.
Root Causes:
Mitigation Steps:
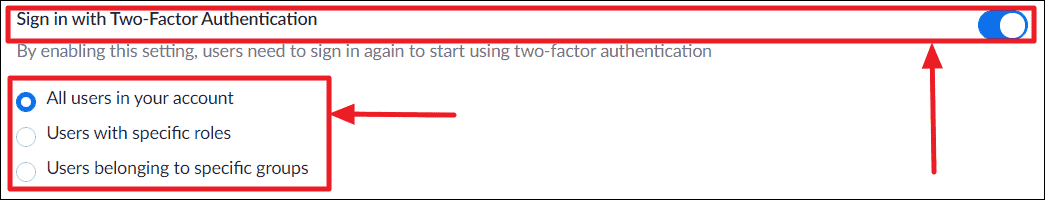
Admin console in Zoom, where two-factor authentication can be enforced across all user accounts for enhanced login security.
Zoom provides flexible settings, but default or misconfigured options (like enabling screen sharing for all participants or allowing file transfers) can expose organizations to risk.
Examples of High-Risk Configurations:
Mitigation Steps:

Screen sharing settings in Zoom, which let you control who can share their screen and disable desktop sharing to reduce risks during meetings.
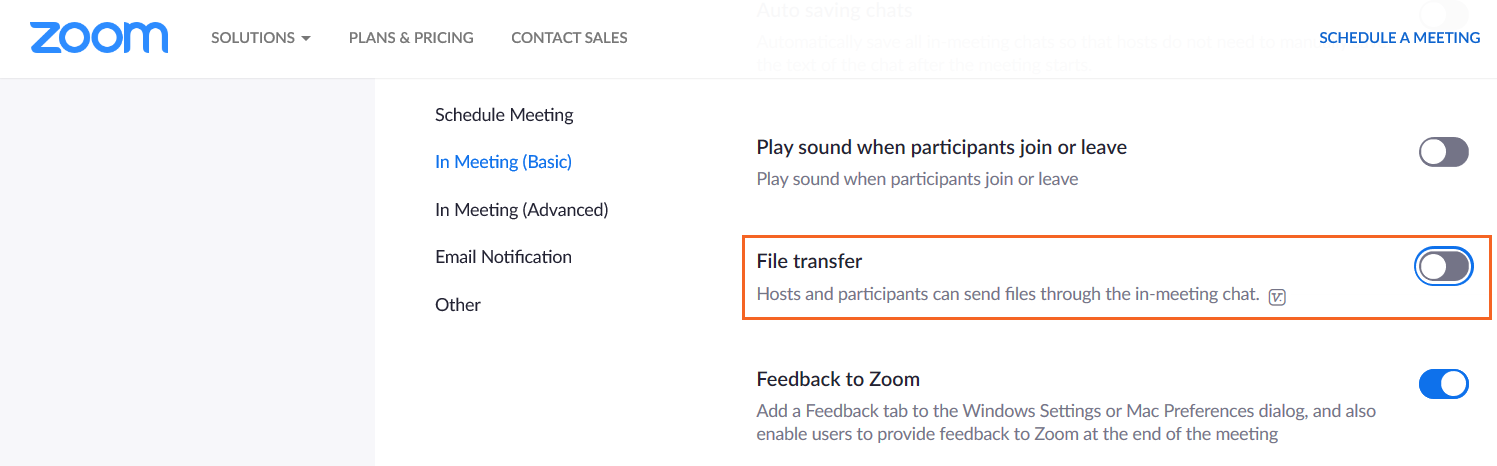
The Zoom chat settings panel allows administrators to enable or disable file transfers during meetings to help prevent malware or data leaks.
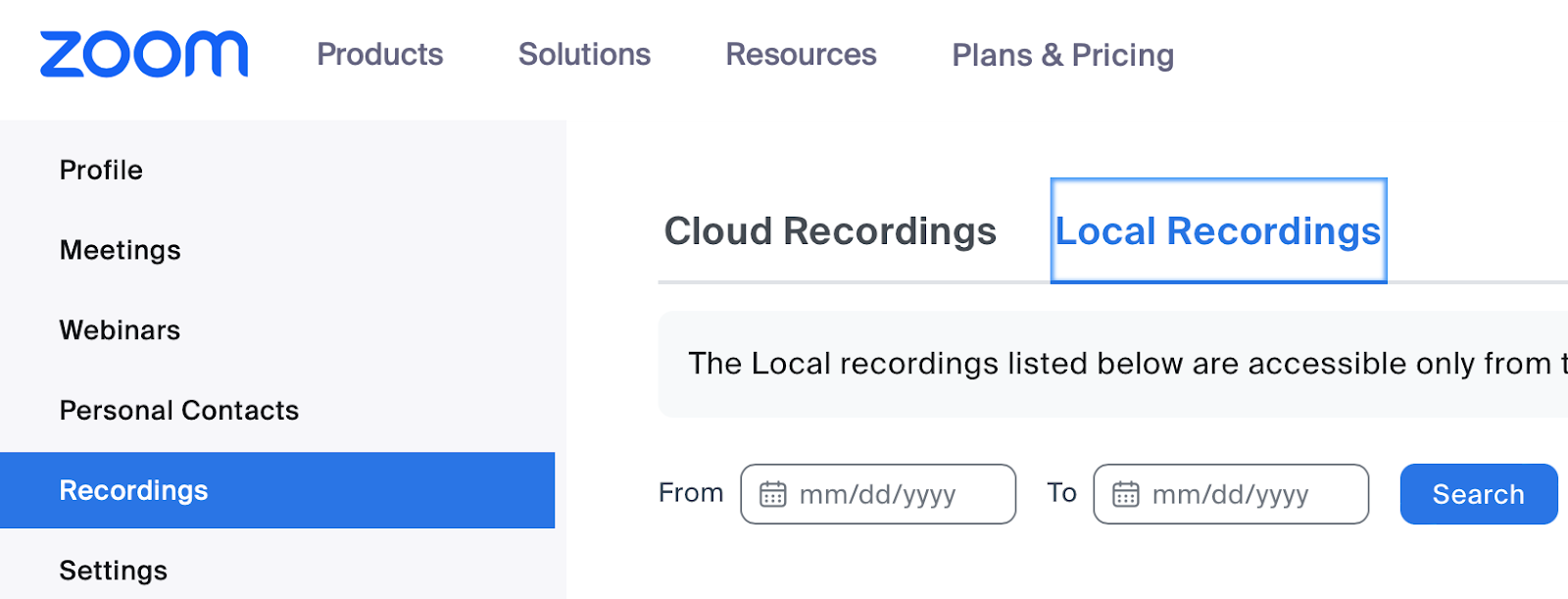
The Settings tab in Zoom, where admins can manage local recording permissions, storage paths, and security measures for recorded meeting data.
Zoom supports numerous third-party apps (e.g., whiteboards, productivity tools), which can access meeting data, participant lists, or recordings. If not carefully vetted, these apps may become vectors for data leakage or compliance violations.
Mitigation Steps:
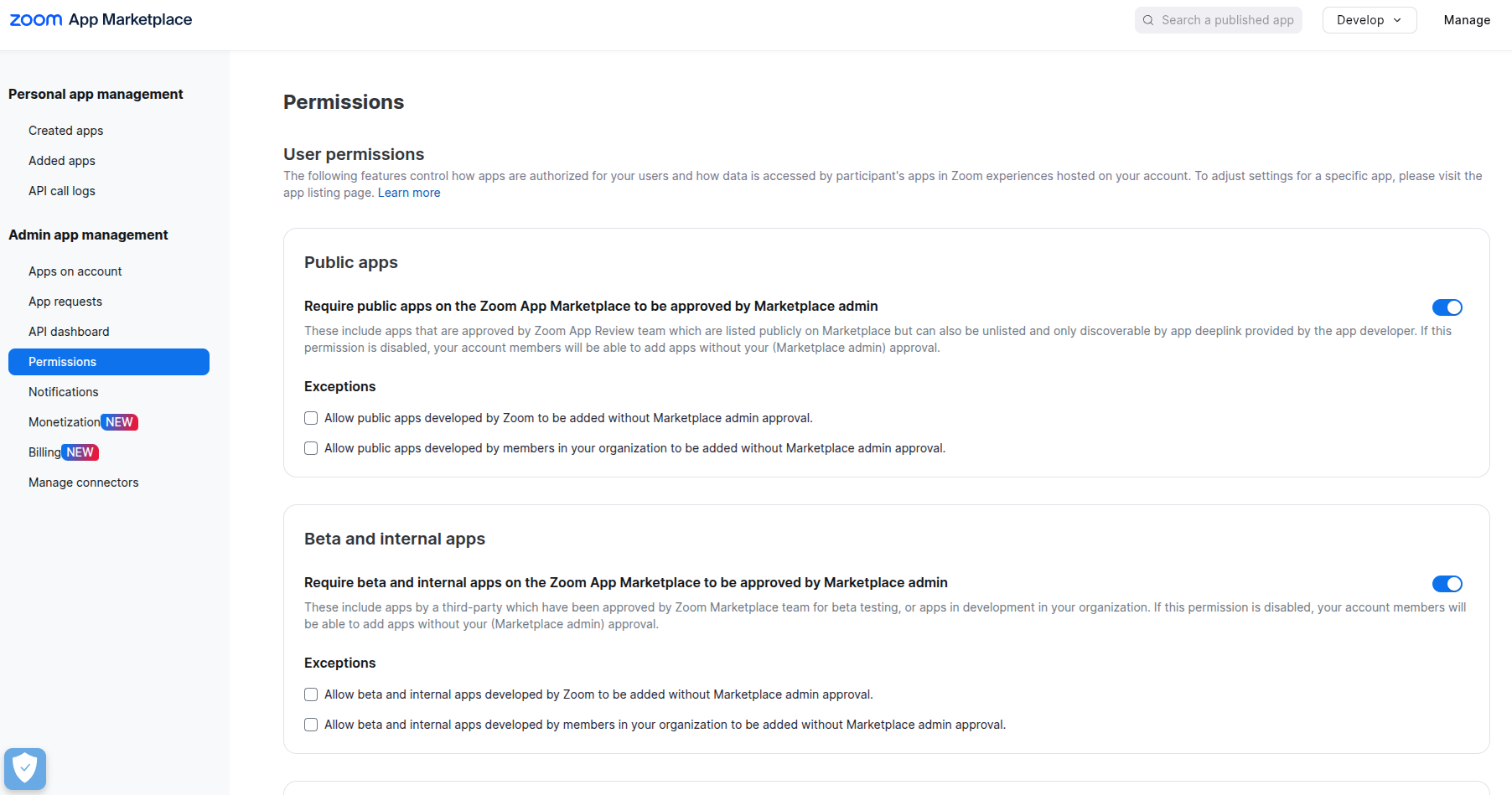
Admin settings in Zoom’s App Marketplace that allow you to manage permissions for public and beta/internal apps, including options to require approval before apps can access meeting data or tools.
Running older versions of the Zoom client may leave users vulnerable to known exploits and bugs. Many security patches and feature improvements rely on the latest versions being installed.
Impact:
Exploitation through known vulnerabilities, bypassed security settings, and degraded meeting performance or security.
Mitigation Steps:
Zoom provides reporting and audit tools, but if these are not actively monitored, security incidents may go undetected or unresolved.
Root Causes:
Mitigation Steps:
Zoom has become a core tool for business communication used for everything from team stand-ups to confidential board meetings. With this growing reliance, IT support teams are now responsible not just for technical setup, but for protecting company-wide collaboration. A misstep in Zoom configuration can lead to security incidents like unauthorized meeting access, data leaks, or even reputational damage. In fact, during the height of the pandemic, reports of “Zoom bombing” rose by over 400%, often due to unprotected meeting links and weak settings.
Cybercriminals often exploit reused passwords or poorly managed integrations to gain access to Zoom accounts. Once inside, they can view sensitive discussions, download recordings, or impersonate participants. This makes Zoom a potential entry point into broader organizational systems, especially when connected to email, calendars, file-sharing tools, or SSO platforms.
For IT support teams, ensuring Zoom security means enabling secure access, enforcing policy compliance, and training users to avoid risks like phishing or unsafe screen sharing. In regulated industries like healthcare or finance, an unprotected Zoom call can also lead to legal issues under laws like HIPAA or GDPR.
Beyond technology, IT plays a key role in promoting a secure work culture. Setting strong defaults (like passwords, waiting rooms, or 2FA), limiting risky features, and monitoring activity logs help minimize threats. A well-secured Zoom environment not only protects data but also builds trust across teams, clients, and stakeholders by making IT a critical player in business continuity.
The best practices checklist outlines the most critical Zoom security settings and controls every IT administrator should implement to strengthen their organization’s security posture. Each item includes actionable steps and guidance to help teams enforce consistent protection across users, meetings, and integrations.
Restricting login to your company domain (e.g., @company.com) prevents unauthorized users from creating or accessing accounts on your organization’s Zoom instance.
How to enable:
To implement this security feature when scheduling a new meeting, follow these steps.
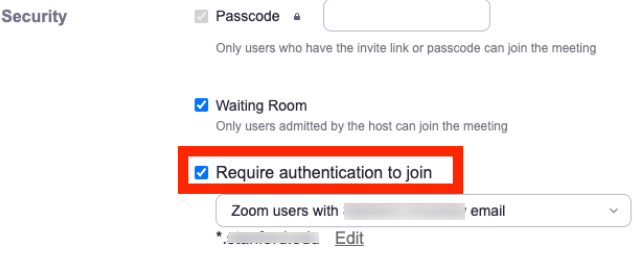
Zoom meeting security settings that allow admins to restrict access by requiring participants to authenticate with specific Zoom accounts before joining.
Note: After checking the box, a pull-down menu will appear with three authentication profile options.
You need to select “Zoom users with @company email”.
This will limit attendees to those signed into Zoom with a Company email or an email from another specified domain that you've listed.
Waiting Rooms allow hosts to screen participants before they enter. Registration adds an authentication layer by collecting names, emails, and approval options.
How to enable Waiting Rooms:
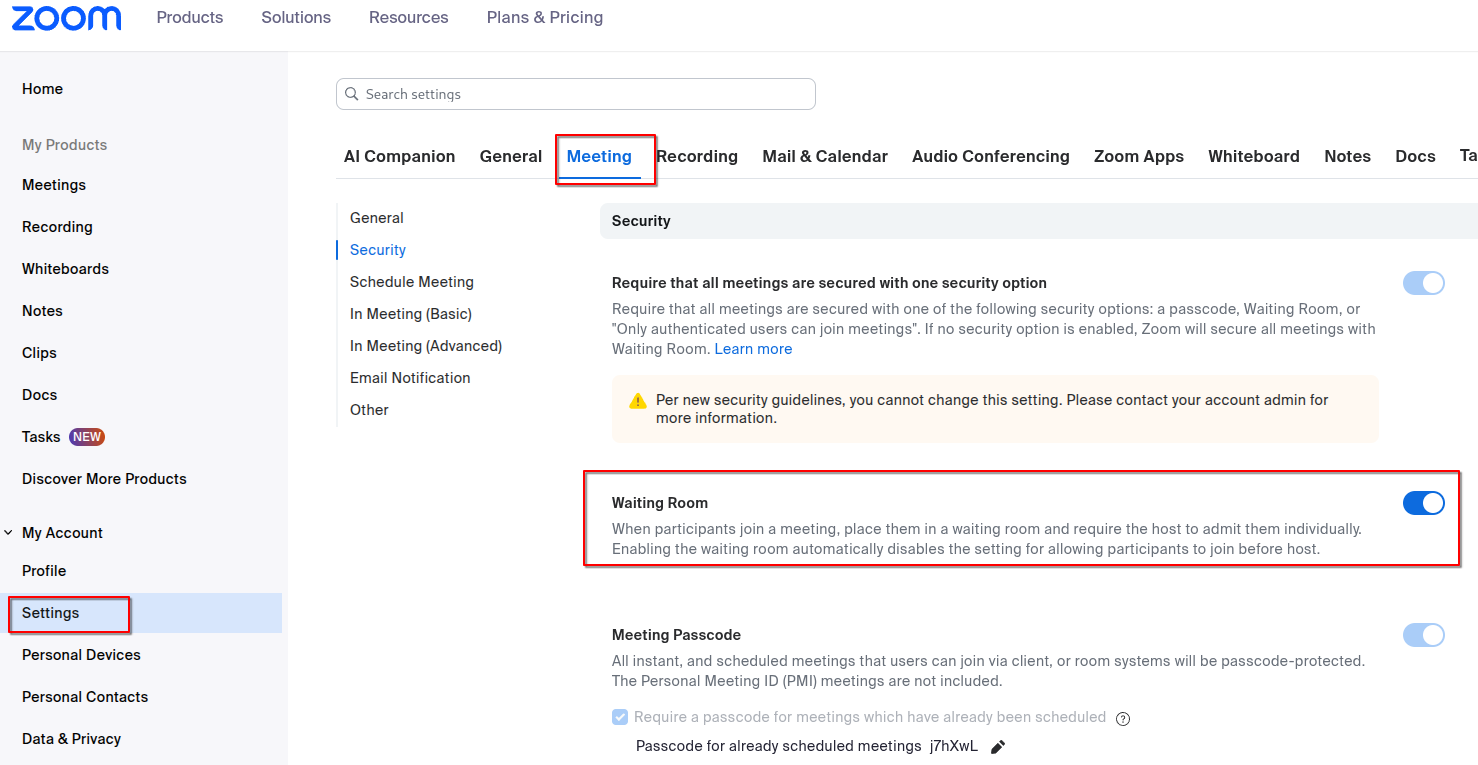
Zoom account settings used to enable the Waiting Room feature, which gives hosts control over participant entry into meetings.
How to enable Registration:
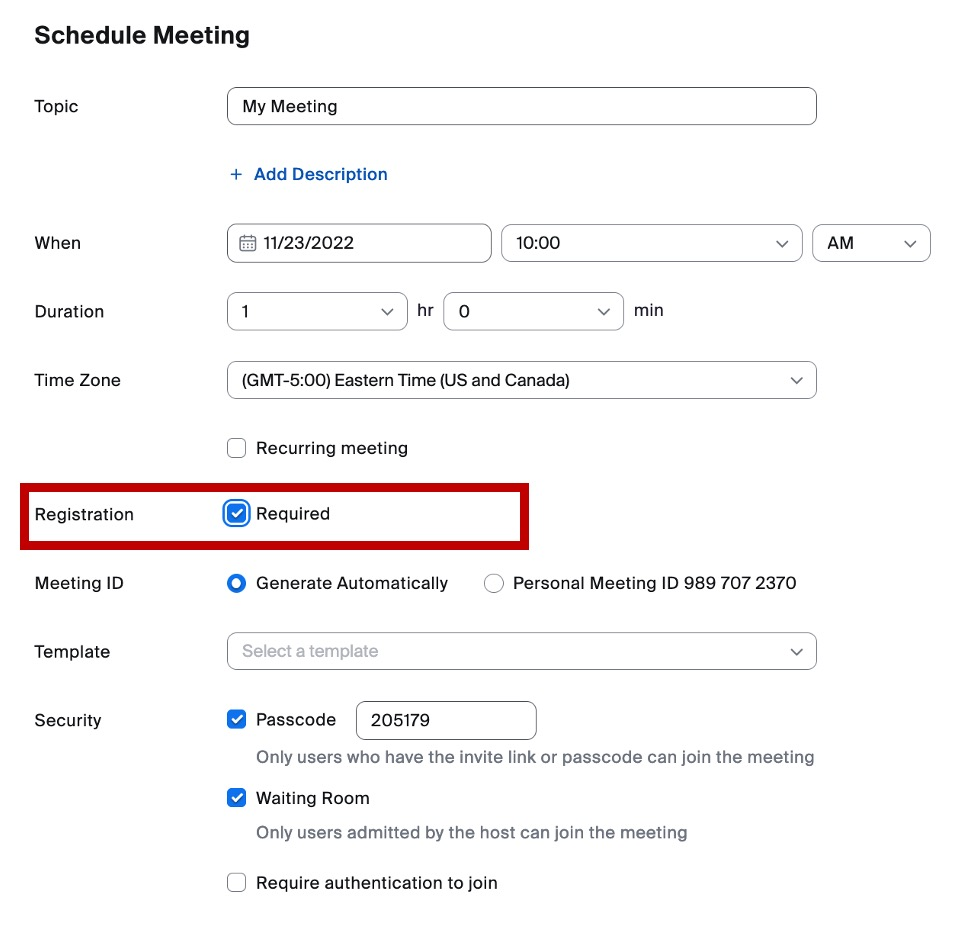
Zoom meeting scheduling settings, where you can enable participant registration to collect emails and names before granting access to a meeting.
The registration link is the link you want to send to anyone that you want to register for the meeting. After checking the registration required check box, save your meeting. The registration link will appear below the meeting ID.
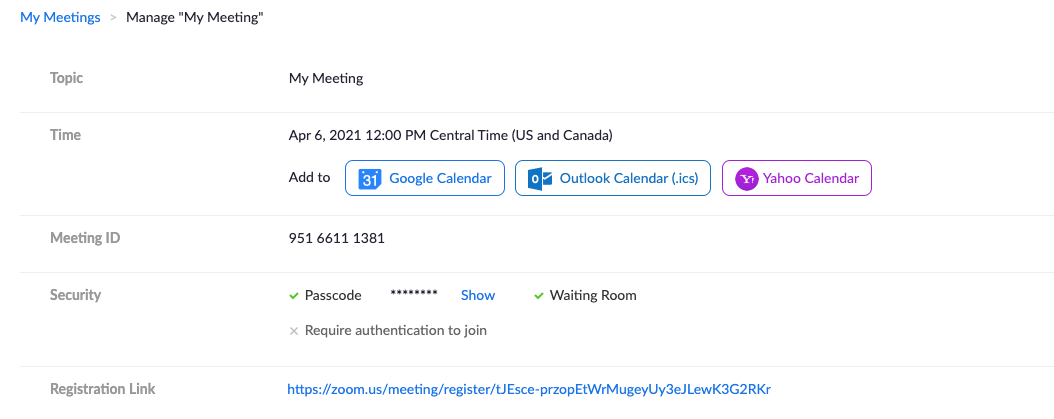
A Zoom meeting summary panel that provides the registration link, which you can copy and share after turning on registration for a session.
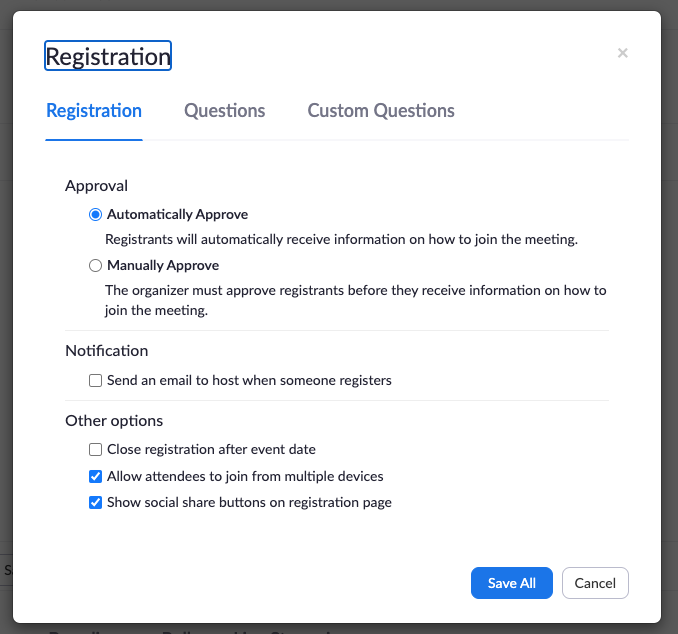
Registration approval options in Zoom allow hosts to automatically approve registrants or manually review participant details before granting access to a meeting.
Screen sharing and saving meeting chat can be used to share inappropriate content or leak sensitive information. Restricting them improves meeting control and reduces risk.
How to limit:

Basic meeting settings in Zoom allow you to restrict screen sharing to just the host, preventing unauthorized content from being shown.

Zoom chat controls that let admins decide whether users can save chat messages during meetings to reduce the risks of leaking sensitive information.
E2EE ensures that only meeting participants can access the content. Not even Zoom can decrypt the audio/video data.
How to enable:
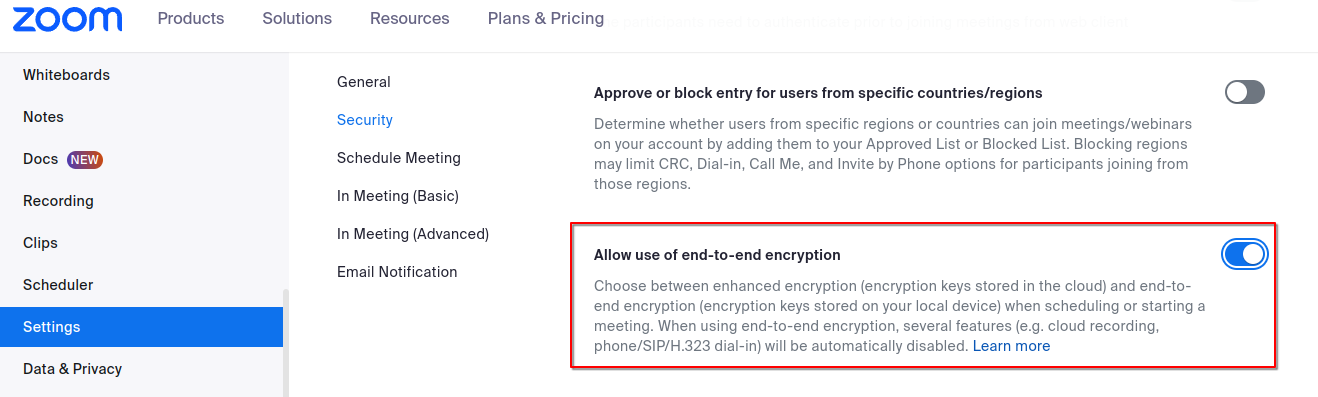
Zoom admin console settings to enable end-to-end encryption, ensuring meeting content remains private and protected from unauthorized access or spying.
⚠️ Note: Some features (like breakout rooms or cloud recording) may be unavailable in E2EE mode.
Outdated Zoom clients leave your organization exposed to known vulnerabilities and may lack essential security features. Relying on users to update manually introduces inconsistency and risk. Centralized update management ensures all endpoints are running the latest secure versions across the enterprise.
Use Endpoint Management Platforms like Microsoft Intune, JAMF, or SCCM to:
Even the best-configured Zoom environment can be compromised by one careless click. That’s why user training is as important as any technical control. IT admins must actively cultivate awareness across the organization to ensure users understand how to use Zoom securely, recognize threats, and avoid common pitfalls.
Here’s how to build a high-impact user training and awareness program:
Develop and distribute a concise internal guide outlining:
Distribute this during onboarding and refresh it quarterly.
Conduct short training sessions every 3–6 months covering:
Offer on-demand replays for remote teams and late joiners.
Make certain training modules mandatory before users can:
This creates accountability and reinforces the importance of security hygiene.
For IT admins, securing Zoom means going beyond default settings and implementing a structured, policy-driven approach that aligns with your company’s broader security architecture.
By enforcing strong authentication, controlling access, managing updates, monitoring activity, and training users, IT teams can significantly reduce the risk of data breaches, compliance violations, and operational disruptions. The vulnerabilities are real, but so are the tools to fix them.
Zoom security isn’t a one-time setup. It’s an ongoing discipline. The best organizations treat it like any other critical IT system: reviewed, audited, logged, and locked down with intention.