Microsoft Entra ID Application Proxy securely extends access for people to internal web applications without exposing the rest of your network to the Internet. It acts as a reverse proxy service and is especially useful for organizations with both on-premises and cloud-based systems or for organizations still on their cloud journey. The proxy service can extend access to web applications, as well as some client-server applications, supporting Microsoft’s identity and access capabilities. This article walks through how to set up Microsoft Entra ID Application Proxy, optimize its configuration, and apply real-world best practices for secure and reliable operation.
Microsoft Entra ID Application Proxy has two main components:
User authentication is performed by Microsoft Entra ID before any internal application access is granted. If authentication is successful, the request is routed through the connector to the internal application. This setup allows you to leverage all Microsoft AD capabilities like Conditional Access, Single Sign-On, and Multi-Factor Authentication.
Microsoft Entra ID Application Proxy strengthens your security posture by enforcing strict access controls and minimizing the attack surface. Key benefits include:
Setting up the proxy involves four main steps: enabling the service, installing the connector, publishing the application, and configuring DNS and certificates. Below, we walk through each step.
This enables the cloud service component in your tenant.
For SSO, configure Kerberos Constrained Delegation (KCD) or use the Header-based Authentication Connector if your internal app requires specific HTTP headers for authentication.
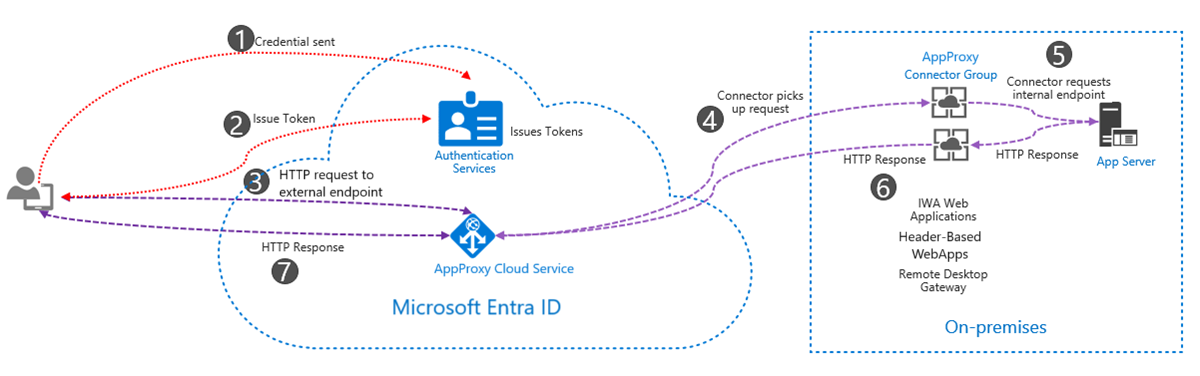
Secure external access to on-premises applications using Microsoft Entra ID Application Proxy with authentication, token issuance, and connector routing.
Microsoft issues a default external URL ending in msappproxy.net. For a better user experience and branding, you can use a custom domain that is verified in your Microsoft Entra tenant, along with a valid SSL certificate.
Also, update your public DNS records to point the custom domain to the Application Proxy service.
Microsoft Entra Application Proxy requires a Microsoft Entra ID P1 or P2 license. Ensure your tenant includes the necessary license tier before proceeding with connector registration or application publishing.
Use PowerShell or Microsoft Graph to check connector health and availability. If any connector shows as inactive, you should investigate immediately.
In addition, Application Proxy connectors are self-updating. Updates are automatically downloaded and applied to ensure stability, compatibility, and security—no manual intervention is needed.
To monitor connector health and version status:
Regularly checking connector health ensures that outdated or inactive instances do not introduce reliability gaps.
Once the setup is complete, you should apply hardening and monitoring best practices to ensure security, performance, and maintainability.
Microsoft Entra ID pre-authentication validates users before allowing them to access internal applications. Avoid Passthrough unless there's a strong reason, such as apps requiring anonymous access.
Microsoft Entra ID Application Proxy fully supports Conditional Access, allowing you to apply identity-based policies before access is granted to internal apps. Use Conditional Access to apply rules based on user, device, location, and risk. Examples include:
Enable diagnostic settings to send logs to Log Analytics, Event Hubs, or Storage Accounts. Monitor authentication requests, traffic patterns, and failures.
This helps you detect repeated failures, which could indicate misconfigurations or brute force attempts.
Deploy at least two connectors in different network segments or physical servers. Azure automatically uses healthy connectors in a group to distribute requests. Use connector groups to map specific applications to specific connectors if segmentation is needed.
For production environments, deploy connector groups across multiple regions or network segments to improve resilience. Application Proxy automatically uses session affinity to maintain user sessions through the same connector. Distributing connectors geographically can reduce latency and avoid single points of failure.
Ensure legacy protocols like NTLM are disabled on the internal application. Application Proxy will forward the request as-is, so protocol hardening must occur on the backend.
Use RBAC (Role-Based Access Control) to limit who can register connectors, publish apps, or modify settings. Avoid giving Global Admin rights to routine app managers.
You can also extend the proxy setup with advanced configurations:
These advanced capabilities allow you to align Application Proxy with more complex identity strategies.
Microsoft Entra ID Application Proxy provides a safe and efficient method of publishing internal web applications for external users. Remote access is easily simplified through existing identity infrastructure while keeping the internal network safe with no inbound connections.
By following best practices such as enabling pre-authentication, deploying multiple connectors, and integrating Conditional Access, organizations can provide a reliable and secure remote-user experience. Mature scenarios would welcome telemetry and fine-grained access controls to control risk and ensure compliance.