If you have been fielding tickets or complaints about users being locked out of third-party tools they are trying to connect with their Google Workspace accounts, there is a good chance that you have come across the "Error 400: admin_policy_enforced" message.
In this article, we will break down what this error really means, why it happens, and what can be done to address it. This is especially important for businesses that rely on Google Workspace not only for its productivity tools but also as a central identity provider for multiple cloud-based tools.
Before we dive into the error itself, it's worth taking a step back to understand how Google Workspace operates in a modern organization.
While most people think of Gmail, Docs, Drive, and Calendar when they hear "Google Workspace," that’s just the beginning. Besides that, it also functions as a full-fledged identity and access management platform. It’s commonly used to authenticate into third-party software as a service (SaaS) applications. This means employees might be using their Workspace credentials to log into tools like Slack, Asana, Zoom, or CRM platforms.
Workspace admins have control over what apps users can connect to their Google accounts and what permissions those apps can access. And that brings us to the heart of the issue.
This error typically appears when a user tries to sign into a third-party app using their Google Workspace account, and the organization’s admin has set policies that block that app or the scopes (permissions) it’s requesting.
Some of the most common causes include:
The error is often frustrating because users assume something is broken on the app’s end. But in reality, the app is working just fine - it’s Google Workspace that’s enforcing a policy set by an administrator.
For IT administrators, these policies are a way to keep organizational data from being exposed to unauthorized or unnecessary services. The goal is to maintain oversight over where sensitive data is going and who has access to it. But these restrictions can lead to errors like the one we're discussing, especially when there's a misalignment between what users expect and what you, as admin, have allowed.
When you get a support request related to this error, you need to identify the problematic SaaS app. Ask the user to send the exact name of the app or the link they were using when the error appeared. This helps determine whether it’s a recognized or unrecognized app within your environment.
Next, you need to decide whether blocked access is a problem. In many cases, Google Workspace is doing exactly what it should: apps that request sensitive scopes (like full Gmail access) but aren’t approved by your organization should be blocked. This reduces your attack surface and lowers the risk of data leakage.
If the restriction wasn’t intentional, you need to identify the root cause and resolve the issue.
To check whether the application is blocked, do the following:
1. Log into the Google Admin Console and navigate to Security > Access and data control > API Controls.

Google Admin Console interface displays the navigation path to API Controls under Security and Access and Data Control, where admins control app access and permissions.
2. On the API Controls page, in the App Access control section, select Manage Third-part App Access.

App Access control section of the API Controls page in the Google Admin Console, where admins can manage access settings for third-party apps.
3. A list of the configured third-party apps is shown. Click on the one you want to check the permissions for.

A list of third-party apps configured in the Google Admin Console, which allows administrators to select and review app permissions.
4. On the app details page, select Access to Google data.

App details page in the Google Admin Console with the option to manage access to Google data for the selected third-party app.
5. On the Access to Google data page, select the option that meets your needs and press the Save button.
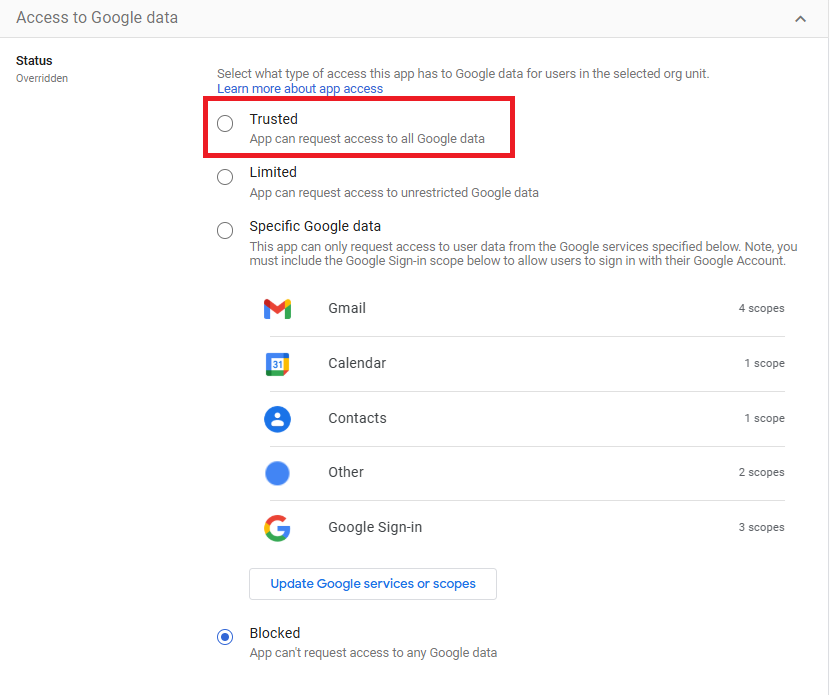
Access to the Google data page in the Google Admin Console, where administrators choose the appropriate access level for third-party apps to Google Workspace data.
Each app requests a set of permissions (scopes) when initiating OAuth. These might include access to email metadata, calendar events, contacts, Drive files, etc.
To review and edit the OAuth scopes available for the application, go to the Manage Third-Party App Access page (step 3 in the previous section) and do the following:

The Google Admin Console allows admins to choose a third-party app and change what data it can access. This helps keep your account safe by controlling app permissions.
2. Change access wizard shows; on the first page, review the organization unit (OU) selection and select Next.

The initial screen of the Change Access wizard in the Google Admin Console displaying the organizational unit selection for app access policy review.
3. On the second page, click Update Google services or scopes button.

The second page of the Change Access wizard in Google Admin Console with options to update Google services or OAuth scopes for the selected app.
4. Specify the Google OAuth Scopes menu shows. Use checkboxes to customize the access allowed for the app, then select Save.

Specify Google OAuth Scopes Menu in Google Admin Console with a list of Google permissions, where admins can select or deselect checkboxes to control app access.
5. Back on the wizard, select Next > Change Access.
Policy settings can be applied at the domain level or specific to an Organizational Unit. Sometimes, the issue isn’t the app but the user’s place in the org tree.
For example, marketing may have broader app access than finance. If a user gets moved to a more restrictive OU, they might suddenly lose access to apps that previously worked.
If the block results from OU-level restrictions and the app is essential for a specific department, consider moving the user to an OU with more permissive access or creating a sub-OU with its own policy set.
This approach works well if you want to maintain tight control across most of the organization while allowing flexibility for teams that need external integrations.
The "Error 400: admin_policy_enforced" message is not a glitch or bug - it’s a clear signal from Google Workspace that an organization’s security policies are doing their job. But that doesn’t mean it has to be a blocker.
As more companies rely on Google Workspace's identity provider functionality to connect to various external tools, it's natural that policy-based barriers like these become common. The answer isn’t to loosen all controls but to build a process where security and usability can co-exist. By making admins and users part of the same conversation, it becomes easier to resolve these issues without compromising data protection or productivity.