11 Salesforce Security Best Practices & Features [2026]

Salesforce Security: Quick Overview
In 2026, as businesses continue to rely heavily on Salesforce for their Customer Relationship Management (CRM) needs, the importance of securing this platform cannot be overstated. Salesforce security involves protecting information from unauthorized access, data breaches, and other cyber threats. With its comprehensive set of security features and best practices, Salesforce helps organizations protect their data effectively.
Salesforce Security Features
Before diving into the specific features Salesforce offers for security, it's important to understand the framework and tools at your disposal. Salesforce provides a wide range of security functionalities designed to keep your data safe from various threats. These features work together to create a robust defense system for your Salesforce environment.
11 Salesforce Security Best Practices
After exploring Salesforce's built-in security features, it's crucial to focus on how you can enhance these protections. Implementing SasS security best practices is key to ensuring your Salesforce environment is as secure as possible. Below, we outline 11 essential steps you should take to boost your Salesforce security. These practices will help you maximize the benefits of Salesforce's security features and protect your data effectively.
1. Run Health Check Regularly
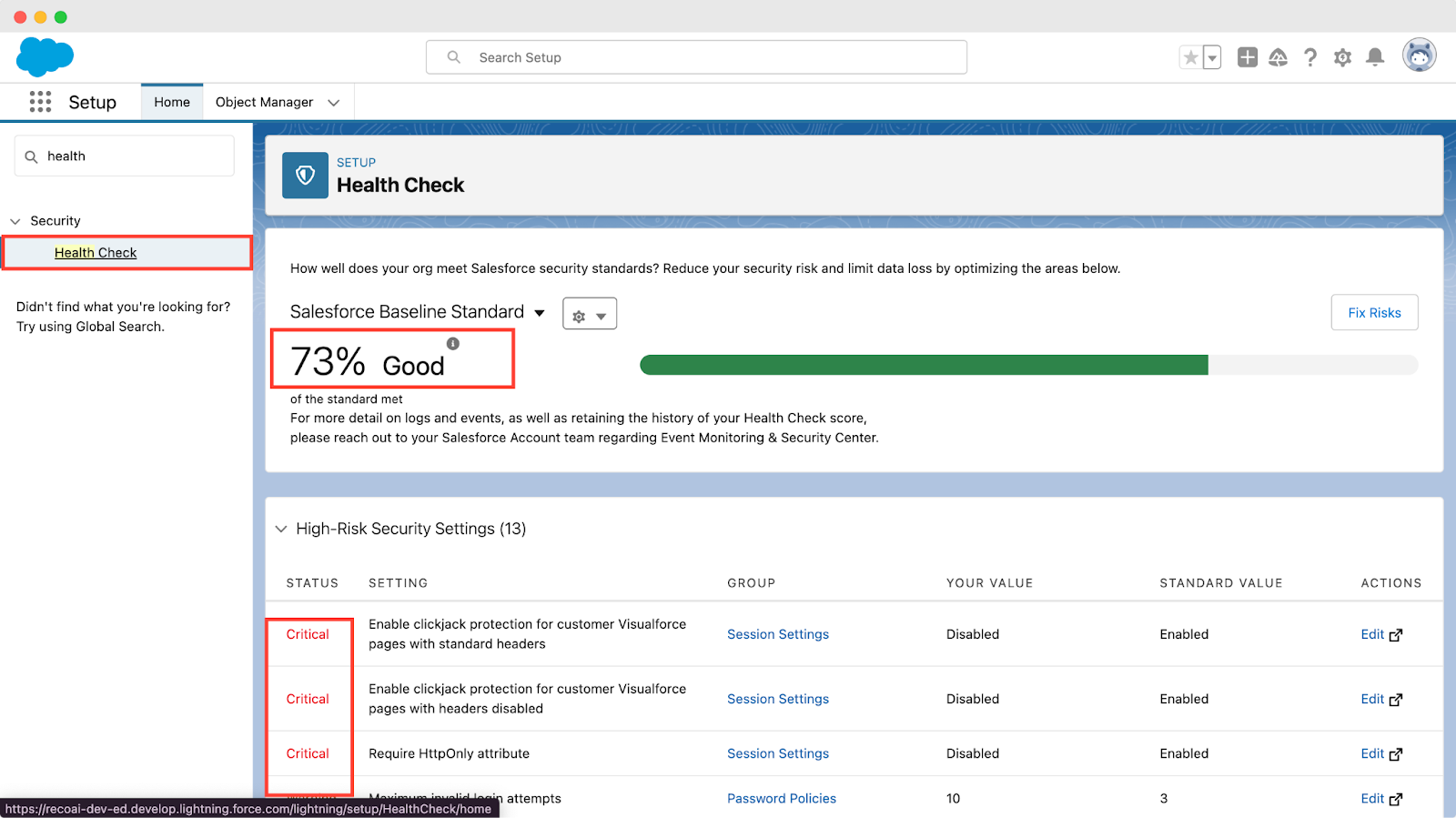
Use Salesforce’s Security Health Check feature to continuously monitor your system’s security settings. This tool compares your configurations against Salesforce’s recommended best practices, providing a security score. Aim to maintain a high score by following the tool’s recommendations to adjust any settings that fall short of these standards. Here’s a step-by-step guide to using the Health Check:
- Access the Health Check: Navigate to the setup menu in Salesforce, search for “Health Check,” and select it.
- Review Your Score: You’ll see an overall score and a list of settings that are not aligned with best practices. Each setting is categorized by its potential risk level—High, Medium, or Low.
- Prioritize Fixes: Start with adjustments in the High Risk category to improve your score quickly and reduce potential vulnerabilities.
- Implement Recommendations: For each setting that’s not in compliance, Health Check provides specific recommendations. Apply these suggestions to improve your score.
2. Use a SaaS Security Tool
Adding a SaaS security tool that works well with Salesforce can boost your security. These tools help by watching over your Salesforce setup all the time, spotting and dealing with security issues as they come up. They're good at finding unusual behavior or signs of a security problem right when they start. This way, you can catch and stop threats quickly.
These specialized tools do more than just watch; they react automatically. If they see something odd, they can let the right people know, stop the suspicious action, or even kick off security steps to block the threat.
3. Enable Multi-Factor Authentication

Implement Multi-Factor Authentication (MFA) to add an additional verification step during the login process. MFA requires users to prove their identity in two or more ways, drastically reducing the risk of unauthorized access due to compromised credentials. Salesforce supports several MFA methods to accommodate different user needs and security requirements:
- Authenticator Apps: These apps generate time-based, one-time passcodes (TOTPs) on a user’s mobile device. Salesforce recommends using authenticator apps because they are more secure than SMS codes. Encourage the use of authenticator apps over SMS or voice calls for enhanced security.
- SMS or Voice Call: A code is sent to the user’s mobile phone via SMS or voice call. This method is easier to implement but less secure than authenticator apps.
- Security Keys: A physical security key that the user plugs into their computer or connects to wirelessly. This is considered highly secure and is convenient for users who regularly access Salesforce from the same device.
4. Evaluate User Privileges Carefully
Conduct regular audits of user accounts and their access levels. Make sure each user has access only to the data and functions that are necessary for their role. Unnecessary privileges can lead to security risks, such as data breaches originating from within the organization. Here’s how to approach it:
- Understand User Roles and Permissions: Salesforce uses roles, profiles, and permission sets to set access - roles for seeing records, profiles for user actions on data, and permission sets to add more access without altering profiles.
- Conduct Regular Audits: Schedule periodic reviews of user roles, profiles, and permission sets to ensure they are still appropriate for each user's current role within the organization. Use reports and dashboards within Salesforce to streamline this process.
- Implement a Process for Access Requests: Establish a formal procedure for users to request additional access. This process should include a review by a supervisor or security specialist to approve or deny the request based on the principle of least privilege.
5. Use The Principle of Least Privilege
Apply the principle of least privilege by default when assigning user permissions. This means giving users the minimum level of access required to perform their duties. Regularly review user roles and permissions to adjust them as necessary, especially when users change roles or leave the organization. Here's a breakdown of how to apply this principle effectively:
- Start with Basic Access: When creating new user accounts, start with the most basic level of access that allows them to perform their job. This might mean assigning them a standard user profile with no additional permissions or access rights.
- Use Custom Profiles and Permission Sets: Create custom profiles for each role to define specific access in Salesforce. Use permission sets to give users extra access as needed, without changing their main profile, for more detailed control.
- Review Access Regularly: Schedule periodic reviews of user access rights to ensure they align with current job requirements. This is especially important after role changes, project completions, or any significant organizational shifts that might alter a user's access needs.
6. Allow Access to Trusted Login IPs
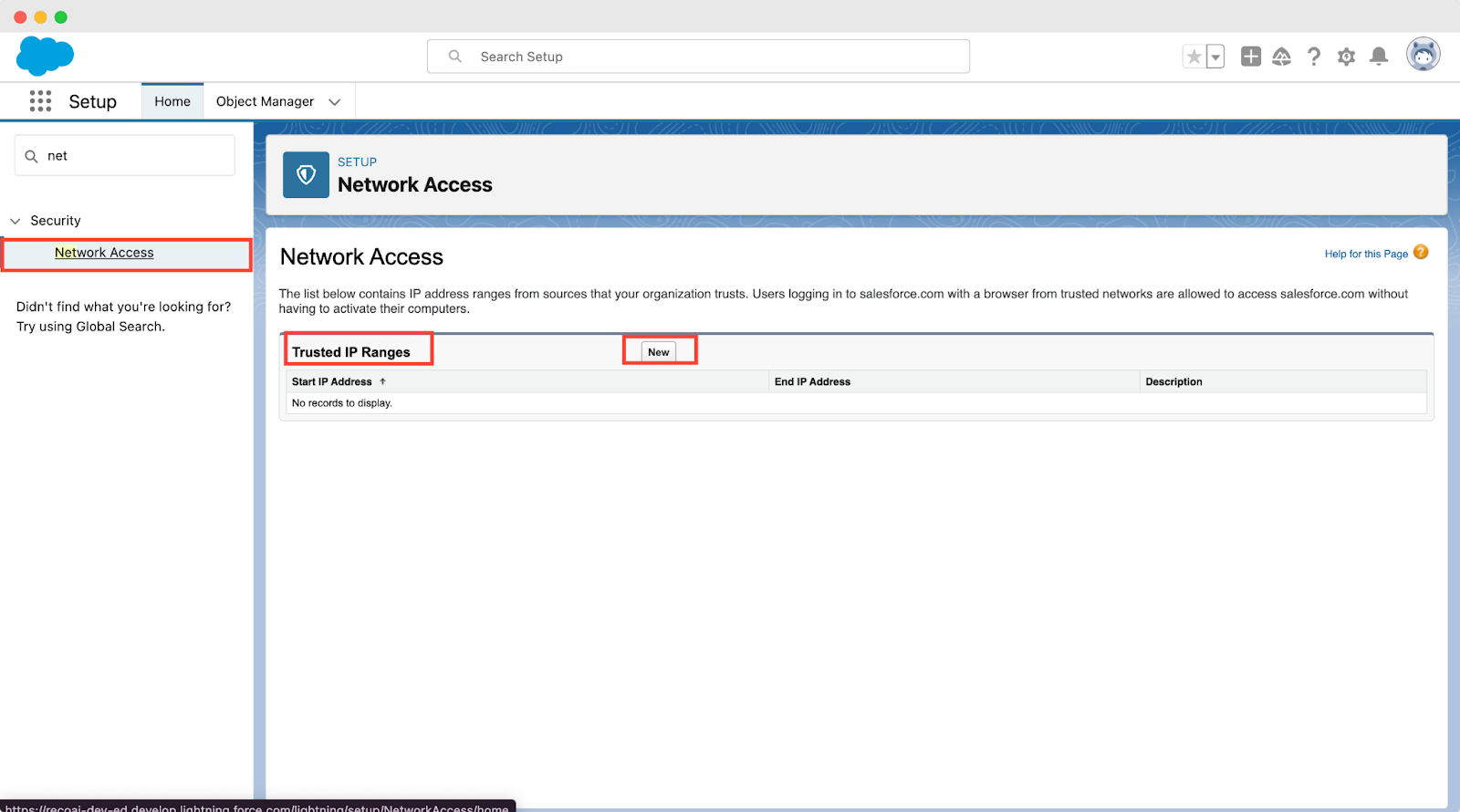
This step is crucial for keeping unwanted visitors out of your system. In the setup, you'll have the option to enter the specific IP addresses or ranges considered safe. This usually includes the IPs for your company's offices and the VPN used by team members working remotely. If someone tries to access Salesforce from an IP address that is not on this list, Salesforce will stop them.
7. Account History Tracking
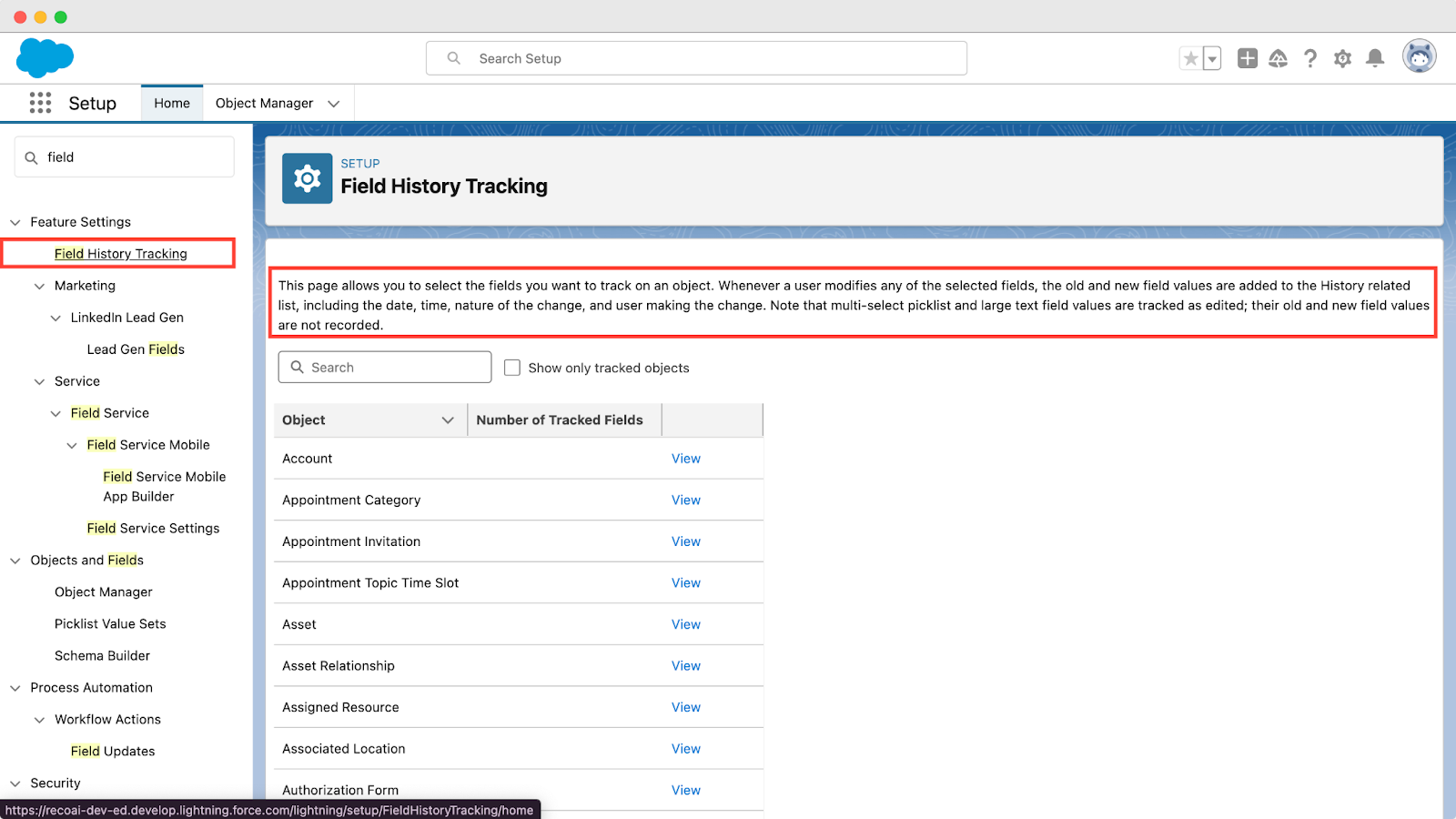
Keeping track of changes made to account information is important for both the security and auditability of crucial information. If we don't track these changes, it's difficult to know if someone made unauthorized edits or if something isn't right. By turning on Account History Tracking, we can see exactly what changes were made, by whom, and when. This helps keep things secure and in compliance with regulatory requirements.
8. Enforce SAML/SSO Connection
Enforcing SAML (Security Assertion Markup Language) and SSO (Single Sign-On) helps keep things safe by letting users access multiple systems with just one login. With this connection being enforced, you make it harder for unauthorized access to occur. SAML/SSO connection ensures that users have to go through the proper channels to access systems, reducing the risk of breaches.
9. Apply Password Security

In Salesforce, you can set password rules through security settings. Here, you can decide how long passwords should be and say they must have different kinds of characters. You can also make it a rule that passwords need to be changed every so often, like every 90 days, and stop users from using their old passwords again. These steps help keep passwords tough for outsiders to guess or break.
10. Use Shield Platform Encryption for Enhanced Data Security
Use Salesforce Shield’s Platform Encryption feature to encrypt critical data stored in Salesforce. This adds a layer of security by making data unreadable to unauthorized users, even if they gain access to the database.
11. Session Timeout
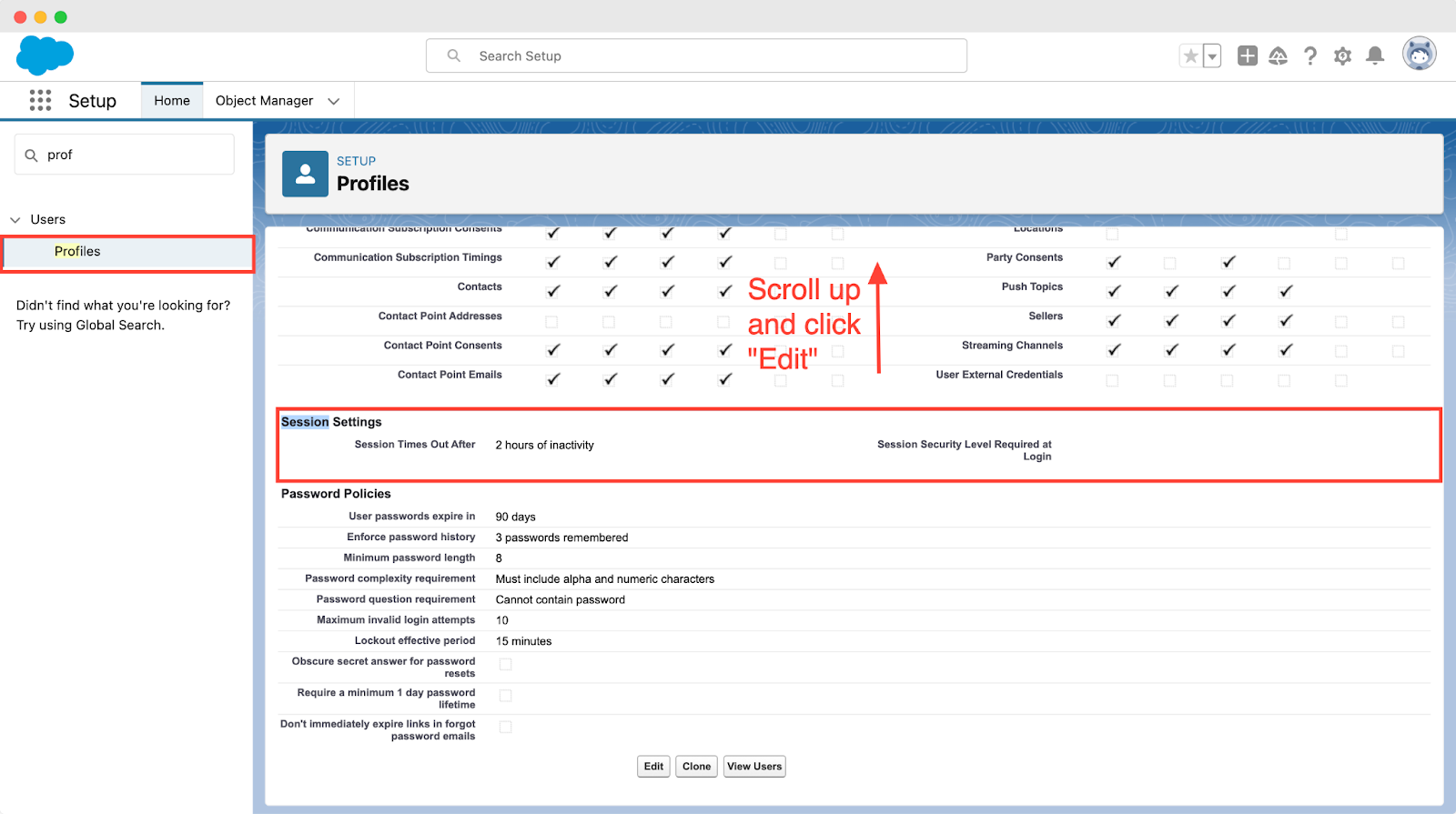
Session Timeout is essential for security. It's important to set the session timeout to "two hours" or less as it helps limit the time someone can access a user's session if it's left unattended. By doing this, you're making sure there's a short window for unauthorized access. It strikes a good balance, keeping things secure without making it difficult for users to do their tasks. This is especially important in places where users might need breaks but shouldn't leave sessions open for too long, as it could be risky.
Conclusion
By leveraging Salesforce's robust security features and adhering to these best practices, organizations can significantly enhance their security posture. Protecting your Salesforce environment is not just about technology; it's about fostering a culture of security awareness and vigilance across your organization. Remember, the goal is not only to protect your data but also to maintain the trust of your customers by ensuring their information is secure.
What are the most common Salesforce security mistakes new admins make?
Most issues come from over-permissioned users and blind trust in default settings.
- Leaving standard profiles unchanged with excessive object access.
- Treating Health Check as a one-time task, not a recurring control.
- Allowing API integrations without scoped permissions.
- Failing to audit inactive users and zombie accounts quarterly.
See related article on Salesforce Health Check.
How should enterprises manage Salesforce security at scale across multiple orgs?
Large organizations need continuous, cross-org visibility instead of manual reviews.
- Normalize configs across orgs using security baselines.
- Monitor identity behavior, API usage, and data access patterns centrally.
- Correlate Salesforce events with IAM and SOAR tools.
- Assign ownership across Security, IT, and Salesforce platform teams.
Explore SSPM at scale.
How does Salesforce fit into compliance frameworks like SOC 2, HIPAA, or SOX?
Salesforce provides controls, but compliance depends on how you configure and monitor them.
- Use Field History Tracking and Event Monitoring for audit evidence.
- Encrypt regulated data with Salesforce Shield Platform Encryption.
- Enforce least privilege and access reviews for compliance attestations.
- Continuously validate drift to avoid audit surprises.
How does Reco detect risky Salesforce behavior that native tools miss?
Reco correlates identity, access, and activity data to surface real risk, not just misconfigurations.
- Ingest Salesforce logs and metadata into the Reco Knowledge Graph.
- Analyze user, admin, and API behavior with AI Agents.
- Flag abnormal access to sensitive objects and reports.
- Trigger alerts or remediation workflows for SecOps.
See how Reco can help secure your SaaS environment.
How does Reco help enforce least privilege in Salesforce automatically?
Reco turns static permission models into continuous access governance workflows.
- Discover overexposed objects, fields, and permission sets.
- Map access paths across users, roles, and integrations.
- Recommend right-sized permissions based on actual usage.
- Automate remediation via ticketing or IAM tools.
Learn more about identity governance.







%201.svg)















.svg)