Behavioral Analytics Security: Types, Benefits and Challenges
What is Behavioral Analytics Security?
Behavioral analytics security is a cybersecurity approach that analyzes patterns of activity by users, devices, and applications to establish what is considered normal behavior and detect anomalies that could indicate potential threats. It relies on techniques such as machine learning and statistical modeling to continuously monitor interactions within systems, enabling earlier detection of attacks that traditional rule-based methods may miss.
Why Behavioral Analytics Security Matters: Key Benefits
Behavioral analytics security helps organizations stay ahead of increasingly sophisticated threats by identifying unusual patterns of activity in real time. These key benefits demonstrate why it has become a foundational element of modern cybersecurity strategies.
- Spotting Insider Threats Early: By continuously monitoring user and entity behavior against established baselines, security teams can detect unauthorized access attempts, privilege misuse, or data exfiltration originating from within the organization, threats that often bypass traditional controls.
- Identifying Advanced Persistent Threats (APTs): APTs are designed to evade signature-based detection by blending into normal operations. Behavioral analytics identifies subtle anomalies, such as lateral movement, staged data transfers, or unusual login sequences, that signal a long-term intrusion.
- Meeting Regulatory Compliance (e.g., HIPAA, GDPR, SOC 2): Regulations demand auditable evidence of data access and usage monitoring. Behavioral analytics tools generate detailed activity logs and alerts that help demonstrate proactive measures to protect sensitive data and maintain compliance.
- Reducing Financial and Reputational Risk: Undetected breaches can result in costly remediation, regulatory fines, and reputational damage. By shortening detection and response times, behavioral analytics limits the scope of attacks, minimizing operational disruption and preserving customer trust.
Core Components of Behavioral Analytics in Security Systems
Behavioral analytics security systems rely on several interdependent components that work together to collect, process, and interpret behavior data. Below, each core component is explained in detail to illustrate its role and technical significance in detecting and prioritizing threats.
Data Collection and Enrichment (Logs, SaaS activity, etc.)
This stage involves gathering raw activity data from multiple sources, such as authentication logs, endpoint telemetry, SaaS application events, and network traffic flows. High-quality data collection is critical because the accuracy of behavioral analysis depends on the completeness and granularity of the input. Enrichment adds context, such as geolocation, device fingerprinting, and user role metadata, to make the collected events more meaningful for subsequent modeling and analysis.
Behavioral Baseline Modeling
Behavioral baseline modeling establishes what constitutes “normal” activity for each user, device, or entity by analyzing historical behavior over a defined period. Advanced models may segment baselines by peer groups (e.g., finance team vs. engineering team) to improve precision. Techniques such as clustering algorithms or probabilistic models are often used here to distinguish legitimate variability from potential anomalies, providing the foundation for reliable anomaly detection.
Anomaly Detection Engines
At the core of behavioral analytics systems, anomaly detection engines compare real-time activity against established baselines to identify deviations that could indicate threats. These engines employ a mix of statistical thresholds, unsupervised machine learning algorithms (like k-means, DBSCAN, or autoencoders), and sometimes supervised models for known attack patterns. Effective engines are designed to adapt over time, reducing false positives by learning evolving patterns without losing sensitivity to true anomalies.
Risk Scoring and Prioritization
Not all anomalies pose equal risk. Risk scoring assigns numerical or categorical risk levels to detected anomalies by factoring in context such as asset sensitivity, user privilege level, and threat intelligence feeds. Prioritization frameworks ensure that security teams focus on the highest-impact incidents first, enabling more efficient incident response and resource allocation. Advanced systems may use weighted scoring models or Bayesian inference to improve risk predictions.
Automated vs. Manual Response Actions
Once a suspicious behavior is detected and scored, the system must determine how to respond. Automated response actions, such as account lockouts, session terminations, or network segmentation, can mitigate immediate risk without waiting for human intervention. However, some incidents require manual investigation and contextual decision-making. Sophisticated platforms allow organizations to configure playbooks and workflows that blend automation with human oversight, striking the right balance between speed and accuracy.
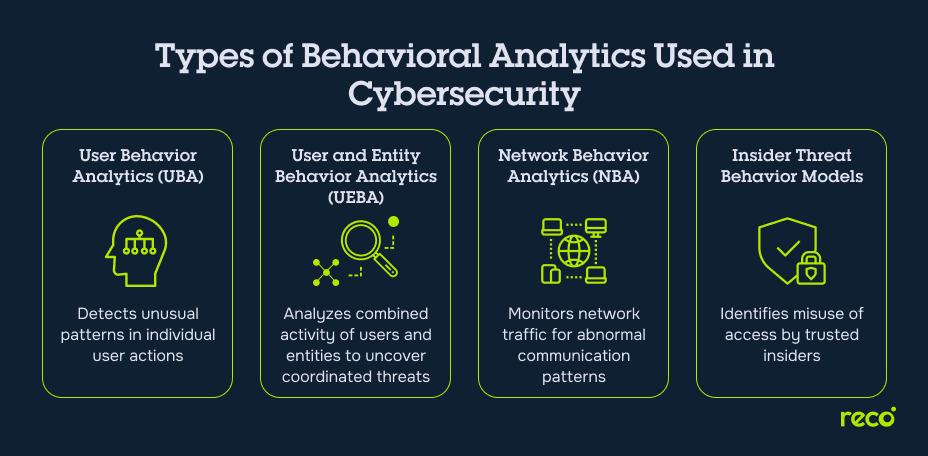
Types of Behavioral Analytics Used in Cybersecurity
Behavioral analytics in cybersecurity takes different forms, each designed to focus on specific aspects of an organization’s environment. Below are the main types, explained with technical clarity to highlight how each contributes to threat detection and response:
1. User Behavior Analytics (UBA)
User Behavior Analytics concentrates on analyzing the actions of individual users to establish their normal patterns of access, movement, and interaction with systems. UBA systems detect deviations such as unusual login times, accessing sensitive files without prior history, or changes in device usage. This approach is particularly effective against compromised credentials and privilege escalation attacks, as it focuses narrowly on user-level activity without accounting for devices or other entities.
2. User and Entity Behavior Analytics (UEBA)
User and Entity Behavior Analytics extends the principles of UBA to include not just human users but also devices, applications, and other non-human entities. UEBA is designed for modern environments where IoT devices, virtual machines, and service accounts generate significant activity. By correlating behaviors across both users and entities, UEBA can uncover multi-stage attacks, lateral movement, or coordinated anomalies that would evade detection by UBA alone. Techniques like peer-group analysis and cross-entity baselining are commonly employed to increase detection precision.
3. Network Behavior Analytics (NBA)
Network Behavior Analytics focuses on monitoring traffic flows and communication patterns within the network infrastructure. NBA systems build baselines of expected traffic volumes, protocol usage, and connection destinations, then flag anomalies like unauthorized port scans, unusual data exfiltration routes, or unexpected connections to known malicious domains. NBA is particularly valuable in detecting early signs of advanced persistent threats and insider activity that manifests through abnormal network behavior rather than user actions.
4. Insider Threat Behavior Models
Insider Threat Behavior Models are specialized implementations of behavioral analytics aimed at detecting misuse of legitimate access by trusted insiders. These models combine indicators such as abnormal file access, privilege misuse, unusual data transfers, and changes in behavior cadence (e.g., typing speed or login frequency) to identify potential malicious or negligent activity. Insider threat models often use a combination of behavioral signals and contextual data, such as role-based access rights and historical trends, to reduce false positives while maintaining sensitivity to genuine risks.
Common Challenges of Behavioral Analytics in Cybersecurity
While behavioral analytics security delivers significant benefits, it also presents operational and technical challenges that organizations must address to realize its full potential. The table below outlines the most common challenges:
Best Practices for Behavioral Analytics Security
Applying behavioral analytics effectively requires careful planning and ongoing maintenance. Below are best practices to help organizations maximize the value of their behavioral analytics security investments:
- Define Security Objectives and Threat Models: Clearly articulate what you aim to detect, such as insider threats, account takeovers, or data exfiltration, and map these goals to specific threat models that guide baseline definitions and anomaly criteria.
- Continuously Update and Train Behavioral Models: Behavioral baselines and detection models can become outdated as user behavior and business operations evolve. Regularly retrain models using recent data to maintain accuracy and reduce false positives.
- Integrate With Your Broader Detection Stack (SIEM, SOAR, EDR): Behavioral analytics work best when combined with other tools, feeding enriched context into SIEM dashboards, automating response through SOAR workflows, and complementing endpoint visibility provided by EDR systems. Including behavioral analytics in your cloud security checklist ensures it becomes a planned and integral part of your broader security posture.
- Monitor for Behavioral Drift Over Time: Users, devices, and networks naturally change their patterns over time. Regularly review baselines and adjust thresholds to account for gradual behavioral drift without missing genuine anomalies.
- Educate Security Analysts on Interpreting Behavior-Based Alerts: Train analysts to understand what behavioral alerts mean, how to investigate them effectively, and when to escalate or dismiss, improving response quality and avoiding alert fatigue.
Real-World Use Cases of Behavioral Analytics in Security
Behavioral analytics security excels in real-world scenarios where subtle deviations in activity signal serious threats. Below are examples of how organizations apply it to detect and prevent high-impact incidents with technical precision.
Detecting Anomalous Access to Sensitive SaaS Data
Behavioral analytics monitors how users interact with SaaS platforms to establish fine-grained baselines for normal access patterns, including typical data types, usage times, and locations. When a user suddenly downloads large volumes of sensitive records outside of their role, accesses confidential reports at odd hours, or uses previously unseen devices, anomaly detection engines flag these events in real time. By enriching activity with contextual data, and in advanced environments using AI agents for SaaS security, teams can distinguish more easily between legitimate changes and malicious exfiltration. This enables faster and more precise responses.
Preventing Credential Misuse or Account Takeover
Compromised credentials often lead to unauthorized access without tripping traditional controls. Behavioral analytics detects the misuse of stolen accounts by identifying patterns inconsistent with the legitimate user’s history. Examples include simultaneous logins from geographically distant locations, use of unfamiliar browsers or operating systems, and abrupt changes in resource usage levels. Advanced implementations combine behavioral baselines with peer-group comparisons to further isolate suspicious actions from normal user variability. This approach enables automated containment of sessions or step-up authentication challenges without unnecessarily disrupting legitimate access.
Correlating Access Patterns With Insider Threat Indicators
Insider threats are among the most damaging and difficult to detect, as insiders operate with valid credentials and deep knowledge of systems. Behavioral analytics correlates subtle indicators (such as elevated file access frequency, attempts to bypass standard workflows, and misuse of privileged accounts) to uncover hidden risks. By integrating contextual awareness, such as sudden role changes or employment status updates, the system enhances detection accuracy while reducing false positives. This capability allows security analysts to focus on genuine insider risks, supported by detailed forensic evidence for further investigation or disciplinary action.
What to Look for in Behavioral Analytics Tools?
Choosing the right behavioral analytics tool is essential to ensure it aligns with your security objectives and integrates effectively into your operations. The best tools combine advanced analytics with actionable insights, enabling teams to detect threats efficiently without overwhelming them with noise. Below are key capabilities to look for when evaluating behavioral analytics solutions:
- User Behavior Tracking: Monitors and records individual user actions across networks, endpoints, and SaaS platforms, creating detailed profiles of normal behavior to support accurate anomaly detection.
- Funnel Analysis: Visualizes user journeys through authentication, access, or workflow steps to identify deviations from expected sequences that may indicate malicious intent or misconfigurations.
- Heatmaps: Present graphical views of activity concentrations across systems or interfaces, helping analysts pinpoint areas of unusual behavior or heightened risk.
- Customer Behavior Insights: Links user activity patterns to business and compliance contexts, highlighting which anomalies could impact sensitive data, regulatory obligations, or customer trust.
- Anomaly Detection with Machine Learning Algorithms: Employs advanced ML models - both supervised and unsupervised - to continuously learn behavioral baselines and identify subtle deviations, reducing false positives over time.
- Risk Scoring and Prioritization Engine: Assigns risk levels to detected anomalies based on contextual factors like data sensitivity, user privilege level, and peer-group behavior, helping security teams focus on high-impact events.
- Integration with SIEM, SOAR, and EDR Platforms: Ensures seamless interoperability with existing detection and response infrastructure, enabling centralized monitoring and automated response workflows.
- Behavioral Drift Monitoring: Adapts to gradual changes in user and entity behavior over time, preventing outdated baselines from creating noise while still detecting meaningful anomalies.
- Privacy and Compliance Controls: Provides mechanisms to anonymize sensitive data, enforce data retention and access policies, and demonstrate compliance with privacy regulations such as GDPR or HIPAA.
How Reco Applies Behavioral Analytics to Secure SaaS Environments
Reco uses behavioral analytics to deliver precise and context-aware security tailored for SaaS applications. By mapping and analyzing human-to-SaaS interactions, Reco helps security teams detect and respond to risks without relying on static rules or excessive noise. Below are the key ways Reco applies behavioral analytics to enhance SaaS security:
- Maps Human-to-SaaS Behavior in Real Time: Reco continuously tracks how individual users interact with SaaS platforms. It correlates their actions with their roles, peer group norms, and typical access patterns. This real-time behavioral map enables proactive detection of unusual or unauthorized activities as they occur.
- Flags Risky Access Without Predefined Rules: While Reco includes preconfigured policies, its behavioral analytics engine adapts these rules with baseline-based detection, enhancing both precision and coverage.
- Integrates with Identity, SaaS, and Security Workflows: Reco connects to identity providers, SaaS apps, SIEM/SOAR, and orchestration platforms, enabling automated alerting and response. This integration ensures that behavioral insights are actionable within the broader security workflow and supports automated response as well as consistent policy enforcement.
- Supports Compliance with Audit Trails: Reco records contextual interaction logs that help demonstrate proactive protection at scale for standards like GDPR, HIPAA, and SOC 2.
- Reduces Investigation Time With Contextual Alerts: Reco enhances analyst efficiency by enriching alerts with the full behavioral context behind each event. This minimizes false positives, accelerates triage, and enables security teams to focus on critical incidents without unnecessary distraction.
Conclusion
Behavioral analytics security has emerged as an indispensable layer in modern cybersecurity strategies. By continuously monitoring and analyzing user, entity, and network behaviors, it enables organizations to detect threats that traditional rule-based approaches often overlook. Its ability to identify subtle anomalies, mitigate insider risks, and adapt to evolving attack techniques makes it vital for protecting sensitive data and maintaining compliance in complex environments.
As cyber threats become more sophisticated, embracing behavioral analytics and adopting a zero trust SaaS model won’t only strengthen your security posture but will also empower your team to respond faster and more intelligently to emerging challenges.

Tal Shapira
ABOUT THE AUTHOR
Tal is the Cofounder & CTO of Reco. Tal has a Ph.D. from the school of Electrical Engineering at Tel Aviv University, where his research focused on deep learning, computer networks, and cybersecurity. Tal is a graduate of the Talpiot Excellence Program, and a former head of a cybersecurity R&D group within the Israeli Prime Minister's Office. In addition to serving as the CTO, Tal is a member of the AI Controls Security Working Group with the Cloud Security Alliance.






%201.svg)















.svg)