Enterprises use Slack to simplify communication and collaboration and integrate systems via apps and bots. With more sensitive discussions and information migrating to Slack, it should be treated as a sensitive enterprise system requiring well-structured security controls and strict compliance enforcement. This article will discuss major technical measures that can be used to help defend Slack at scale and ensure regulatory and internal standards are met.
The first line of defense in securing Slack is tight identity controls. Slack can be integrated with identity providers using SAML-based SSO, SCIM to manage user lifecycle, and granular role-based access control. Use Slack Enterprise Grid to centrally manage identity and security policies across multiple interconnected workspaces. Enable SAML SSO to allow users to authenticate via a corporate identity provider such as Azure AD or Okta. That way, Conditional Access, MFA, and other identity protections can be used consistently.
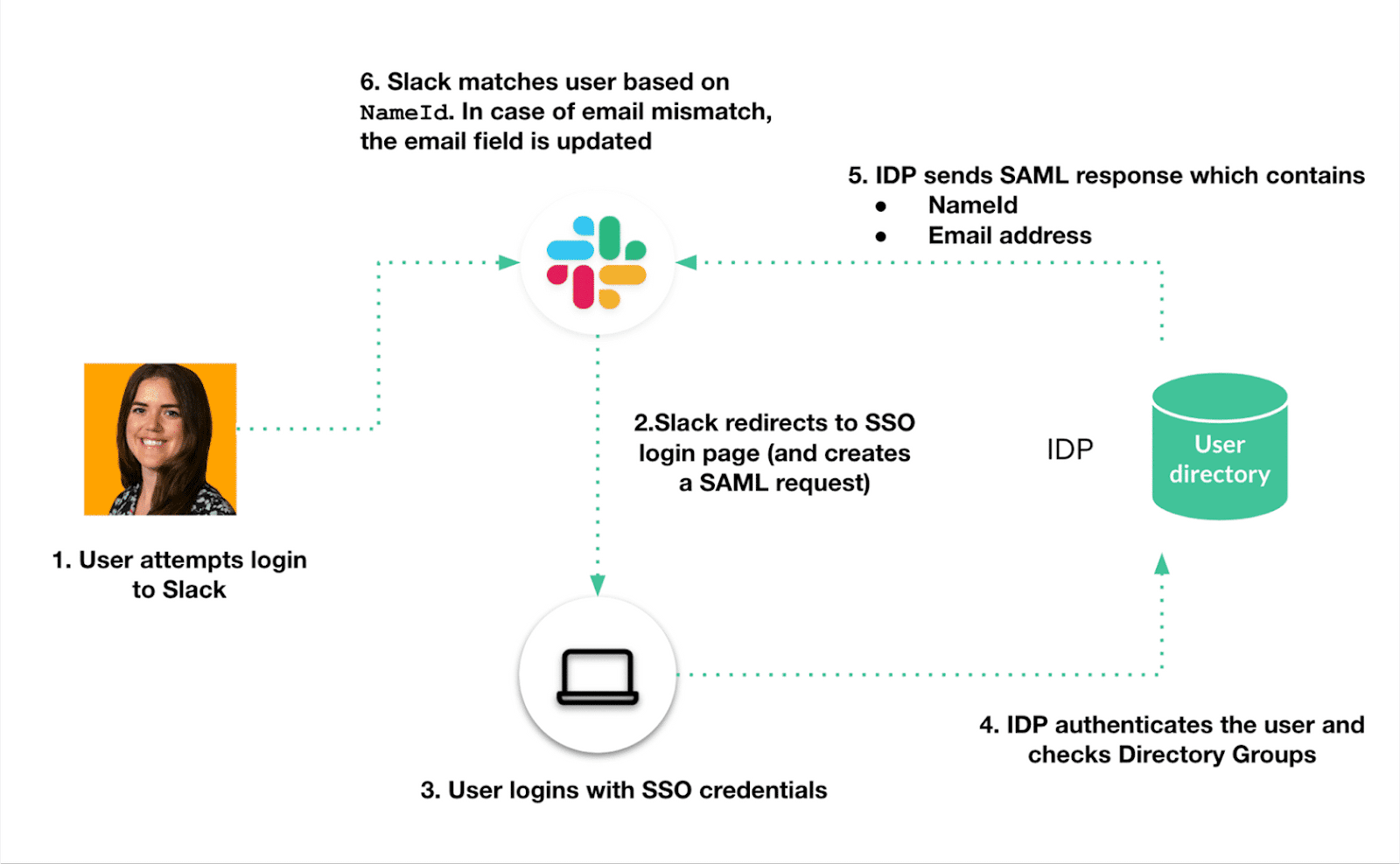
SCIM enables automatic user provisioning and deprovisioning, syncing user creation, updates, and deletions directly from your identity provider. Users who have been deprovisioned are not supposed to be allowed to retain access, so they should be deleted or disabled. Make sure that such roles as Primary Owner, Admins, and Workspace Owners are restrictive and should be audited. A role model in Slack consists of workspace permissions and organization permissions. Do not use generic or shared administration accounts. Use Slack’s Audit Logs API to track role changes and investigate any abnormalities.
Once users are authenticated, securing the session and endpoints is key to protecting data access. Use Slack’s Enterprise Mobility Management (EMM) integration to apply device-level restrictions for mobile access. You can enforce that Slack access is only allowed from devices enrolled with MDM solutions such as Intune or Workspace ONE.
For desktop users, rely on secure browser sessions and endpoint detection. Session control can be enforced through MDM/EMM policies, revoking user tokens via Slack’s Admin APIs, or automating user offboarding through SCIM.
Enable session duration limits and device restrictions where feasible. You can restrict downloads on unmanaged devices using MDM integrations or by enforcing endpoint policies in Slack EMM-enabled environments.
Security visibility into Slack is essential for ongoing risk management and threat detection. Slack provides audit logs for user actions, admin changes, login attempts, and message events. Integrate these logs with a SIEM like Splunk, Microsoft Sentinel, or Elastic.
Monitor for unusual behaviors such as:
Use automation rules to trigger alerts or responses based on specific Slack events. Enrich alerts with user identity, IP location, and device details.
Utilize the Discovery API to identify and classify sensitive content across messages and files, especially useful during compliance reviews or legal holds.
Slack apps and bots may be strongly integrated with internal systems, APIs, and third-party services. Failure to manage such integrations properly may lead to risks. Restrict the apps that users can install using Slack App Manager. Establish approval processes (workflow) around new app requests and keep a list of permitted apps by risk category.
Bring your own Slack-built internal applications with Slack granular OAuth scopes. Monitor and revoke unused tokens on a regular basis. The principle of least privilege also applies to bots and applications - only grant them the minimum necessary permissions. Track activity using the Audit Logs API and enable Event Subscriptions to get real-time notifications when apps are installed, uninstalled, or improperly configured.
Slack messages, files, and links may contain sensitive business data, including PII, PHI, financials, or IP. DLP enforcement is critical to avoid data leaks. Slack supports third-party DLP integration through APIs. Integrate Slack with solutions like Microsoft Purview, Symantec DLP, or Netskope to inspect messages and attachments in real time.
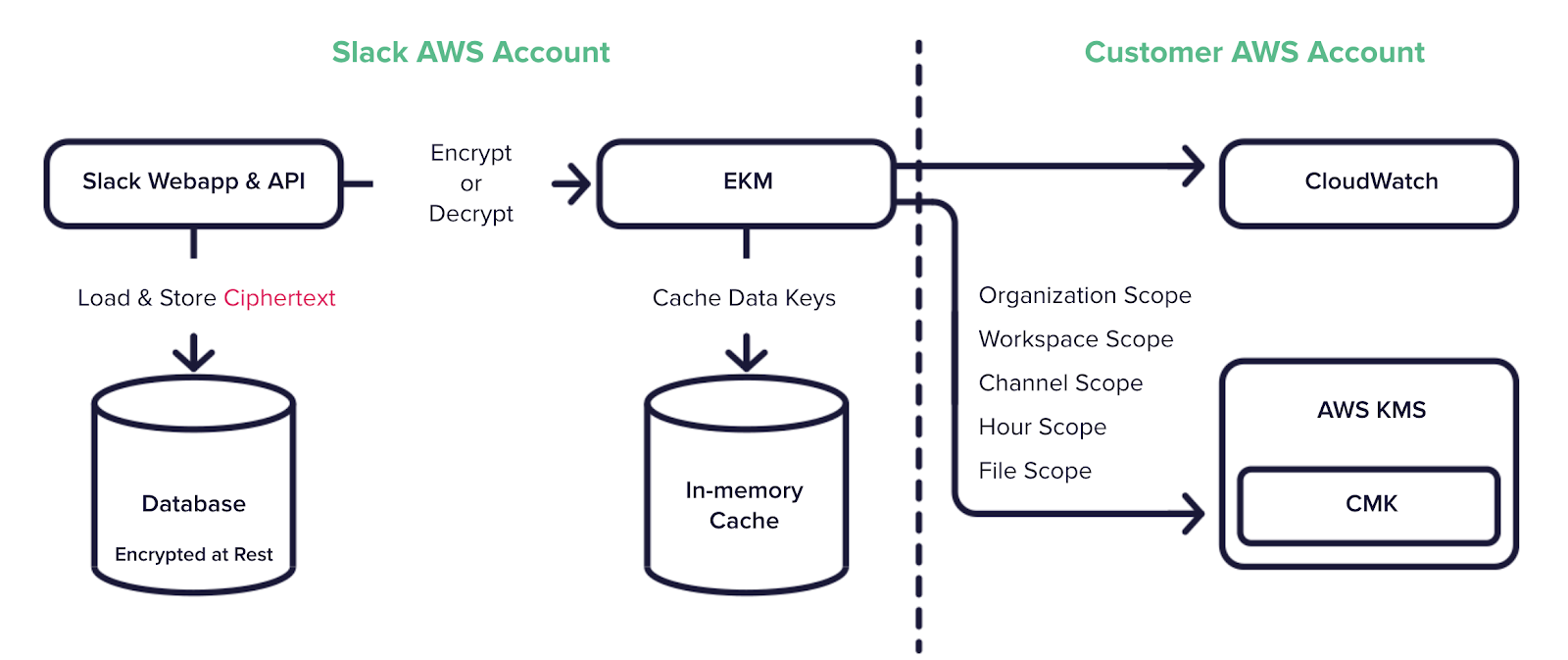
Set up DLP policies for public channels, file uploads, and messages that match sensitive patterns. Use regex rules or predefined classifiers (like credit card or SSN patterns) to trigger alerts or take action. Block file uploads from unauthorized users or untrusted devices. Consider encrypting all uploaded files and limiting retention. Slack’s Enterprise Key Management (EKM) lets you control encryption keys stored in AWS KMS for added control.
Beyond individual settings, it’s important to configure Slack workspaces securely and enforce admin hygiene practices.
Limit public channels for sensitive departments. Use private channels and user groups for access segmentation. Disable guest and external collaborators unless required.
Conduct quarterly reviews of:
Avoid turning on features like public file sharing or email invitations unless required. Set naming conventions for channels and enforce usage through bots or automation.
Slack Connect enables secure, inter-company collaboration by allowing users to share channels with external partners, vendors, or clients. While powerful, this feature introduces additional security concerns if not properly governed. To minimize risk:
Be sure to include shared channels in your quarterly workspace audits, and monitor shared activity using the Audit Logs API and Event Subscriptions to detect abnormal behavior or risky permissions.
Slack offers compliance features designed to support data residency, eDiscovery, and retention controls.
Enable message retention policies per workspace or channel. You can choose to retain messages indefinitely, for a fixed duration, or delete them after a certain time. Use Legal Holds to preserve data during investigations. Enable Corporate Export (with Slack’s approval) if your business needs direct access to content for compliance. Configure eDiscovery connectors with third-party platforms like Onna, Smarsh, or Relativity.
Slack also supports integrations for archiving tools to help comply with FINRA, HIPAA, or GDPR requirements. For regulated industries, Slack Enterprise Grid helps enforce compliance centrally across multiple business units.
For enterprises operating in regions with strict data protection laws, such as the EU (GDPR), Canada (PIPEDA), or Australia (APP), Slack offers Data Residency capabilities that allow customers to choose where select types of data at rest are stored.
Key features of Slack’s Data Residency program include:
It’s important to note that metadata (e.g., billing, logs) may still be stored globally. Therefore, combining Data Residency with strong encryption (via Slack’s Enterprise Key Management) and regular compliance audits is recommended to maintain full control over data sovereignty.
For security-conscious teams using Slack as a core business tool, go beyond the default settings. Make use of enterprise-grade features and external integrations to build a strong security foundation.
By treating Slack as a critical business system and securing it like any other enterprise application, organizations can reduce risks and meet their compliance requirements. A layered approach covering identity, devices, apps, data, and monitoring helps ensure that collaboration remains secure and resilient.