Securing Make.com integrations in an enterprise environment now requires addressing identity, data flows, API exposure, credential handling, governance, and operational monitoring. Make.com is a visual-first automation and integration platform that connects SaaS applications, APIs, databases, and AI-driven components through modular, no-code scenarios.
With the 2025 Wave releases, such as next-generation AI Agents, authenticated webhooks, Make Code, and expanded Make Grid capabilities, the integration surface has grown, but the security fundamentals remain consistent.
Enterprises must understand how workflows execute, how data moves between systems, and how new AI-driven automation components interact with internal and external services. This article explains how to secure Make.com comprehensively in modern enterprise settings.
To design a secure setup, you must first understand what Make.com introduces into your environment.
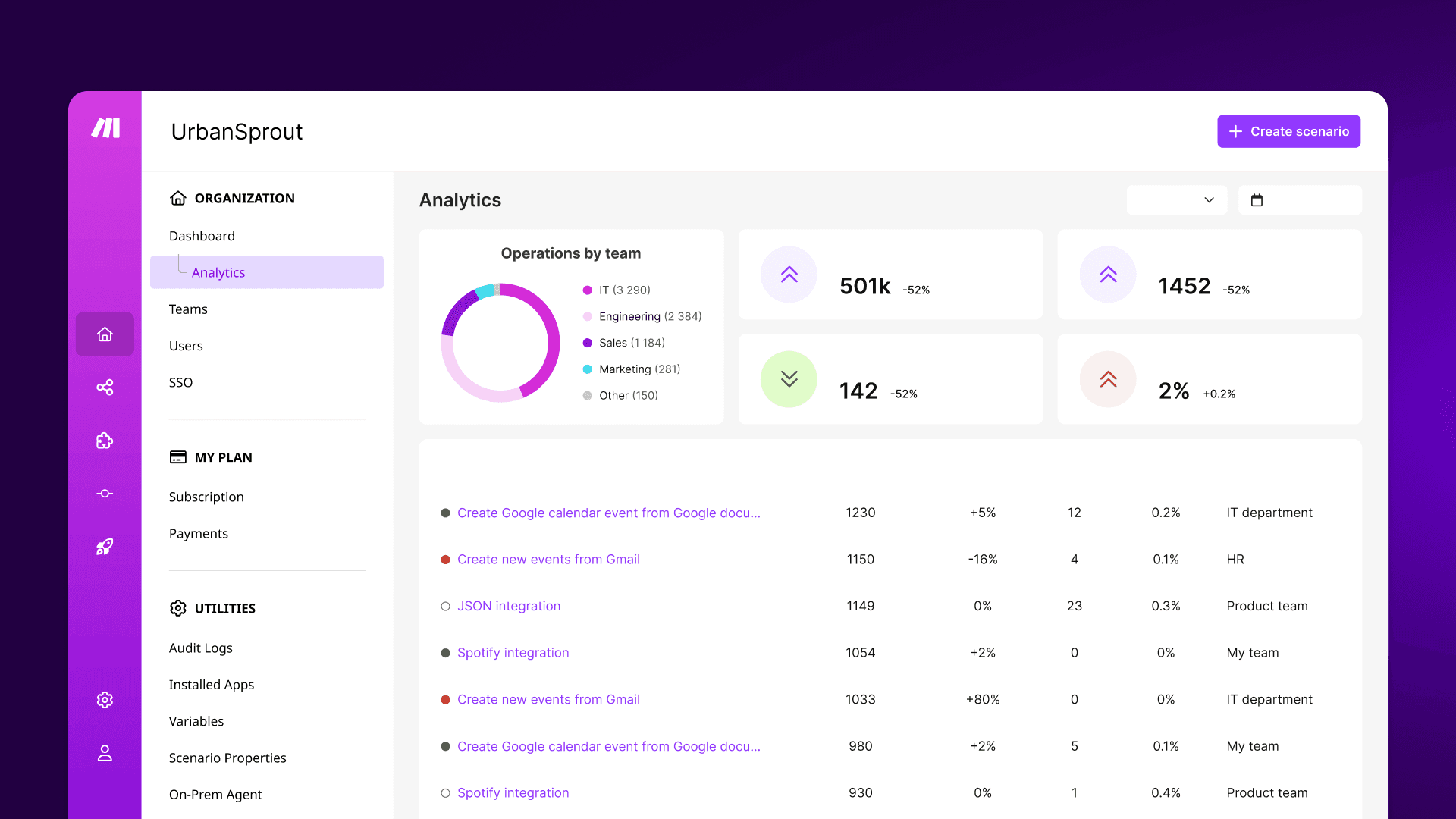
Make.com acts as an orchestration layer that connects to internal and external systems through modules and scenarios. These scenarios may handle customer data, internal documents, authentication tokens, and operational triggers from SaaS platforms, APIs, or databases. Because Make.com sits between systems, its security posture directly impacts your broader architecture.
Large enterprises typically integrate HR systems, CRMs, data warehouses, ticketing platforms, monitoring tools, and cloud services. This creates multiple attack surfaces: connection credentials, webhook triggers, API responses, data transformations, and runtime execution. The first step is mapping every system that Make.com interacts with, along with the sensitivity of the exchanged data.
Before adding your own controls, review what Make.com already provides.
Make.com’s Enterprise plans support:
These features form a secure base, but enterprises still need custom controls for identity, data handling, network restrictions, and operational governance.
This section builds on the platform’s controls and integrates them with enterprise IAM standards.
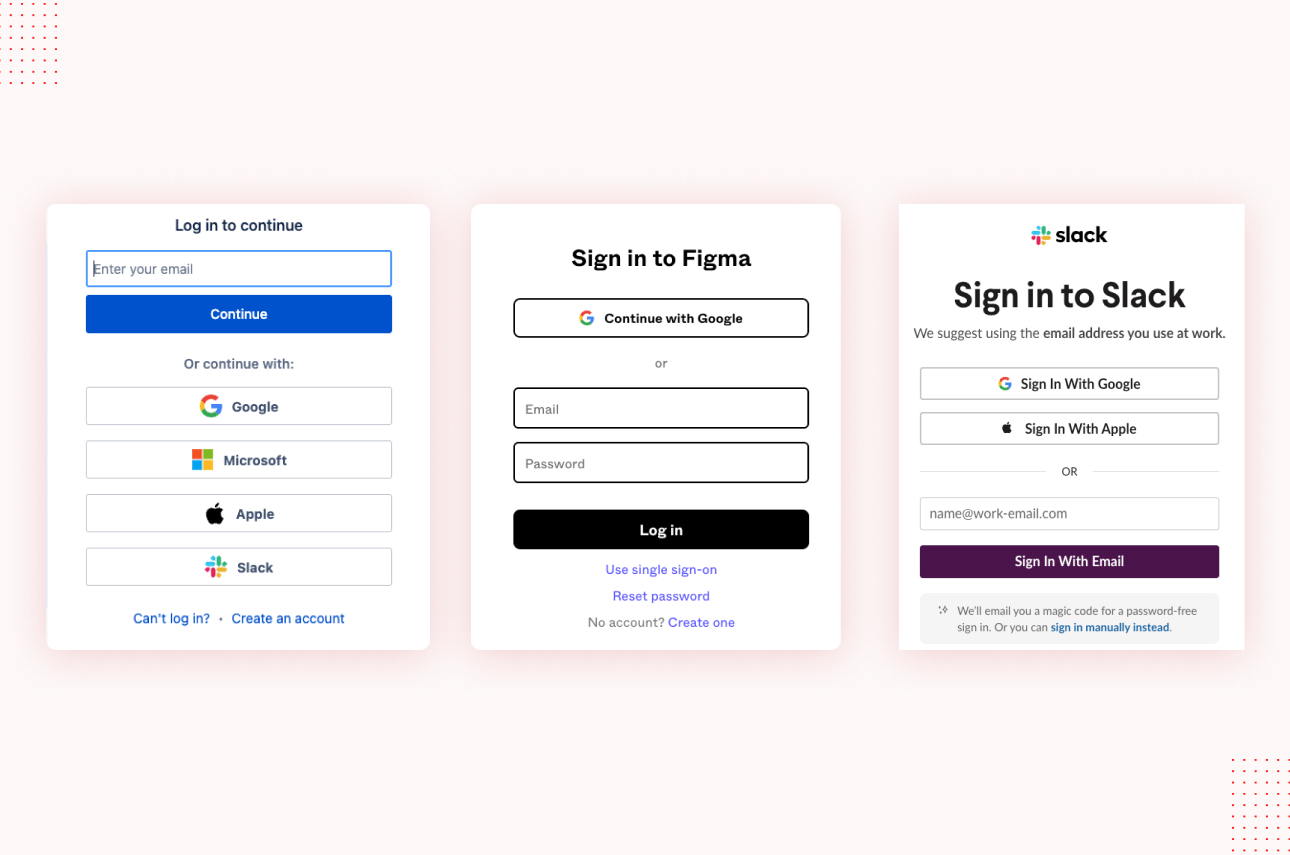
Start by enabling SSO for all Make.com users, enforced through your central identity provider. Multi-factor authentication should be mandatory for your IdP. Once SSO is configured, map business roles to Make.com’s role structure. For example, automation developers may edit scenarios but cannot modify production connections. Auditors may only view logs. Administrators in your enterprise IAM team can provision users automatically through SCIM or manual mapping.
Segregation of environments is also critical. Development, testing, and production should be separate workspaces with isolated credentials and connections. A developer should not have the ability to trigger workflows in production by mistake or to access production tokens. This separation reduces misconfiguration risk and helps build a pipeline-like automation lifecycle.
Make.com often moves data between systems. Each data exchange must be secured end to end.
All connections in Make.com communicate over HTTPS, but you should validate certificate handling and disable insecure endpoints. If your internal systems expose APIs, enforce TLS 1.2+ and strong authentication. When moving sensitive fields (like identity data, health records, financial attributes), filter or mask fields before sending them to external services.
Make.com stores scenario logs and temporary data snapshots. Enterprises with compliance requirements should configure retention periods and restrict log access. Teams handling regulated data (HIPAA, GDPR, PCI) must ensure that the Make.com region aligns with data residency policies.
Whenever possible, prevent full payload retrieval. If a module allows requesting specific fields, always reduce the data footprint. Limiting unnecessary data movement lowers the risk of unintended exposure.
Credentials are the most sensitive component in Make.com integrations. Every connection in Make.com stores tokens, API keys, or OAuth authorizations. To minimise risk:
If your organization uses a secret manager (AWS, Vault, Azure Key Vault), integrate secret rotation from the external system and periodically re-authenticate Make.com connections. Whenever possible, avoid embedding secrets in script modules or HTTP module URLs.
When exposing internal APIs to Make.com, front them with an API gateway that enforces rate limits, throttling, authentication checks, and logging. If a workflow loops unexpectedly, the gateway prevents it from overwhelming downstream systems.
Each workflow must follow an operational structure similar to any enterprise application.
Enterprises should maintain a governance model documenting:
Make.com’s monitoring tools provide logs, execution results, error details, and scenario histories. Forward these logs to your SIEM for unified alerting. Configure alerts for repeated failures, sudden increases in API calls, or large data transfers. These patterns often indicate misconfiguration or malicious activity.
Audit logs from Make.com should be integrated into your compliance process. Track who modified scenarios, who changed credentials, and what workflows moved regulated data. Regular audits help identify unnecessary scenarios or permissions that have accumulated over time.
Security must be part of workflow design, not only infrastructure.
Scenarios should be clear, modular, and easy to review. Instead of building a single large workflow, break it into smaller scenarios that expose only the required inputs. This reduces the risk of data leaking between unrelated steps and makes it easier to maintain individual components.
Add error-handling branches to catch failures and respond safely. For example, if an API returns a 500, the scenario should stop processing and raise an alert rather than continue with incomplete data.
When scenarios handle sensitive information, apply strict controls to limit exposure.
Approval steps are essential for high-risk workflows. When automation writes to a CRM, updates customer records, or triggers infrastructure actions, it should require a manual confirmation step from an authorized user. Version history must be preserved through exports or documentation. Any scenario change should follow the same review and approval process that your organization uses for code updates.
With the Waves ’25 updates, scenario design now includes a few additional elements that require attention. Features such as next-generation AI Agents, Module Tools, Make Code (Python/JS), and reusable Subscenarios introduce new execution surfaces that must be governed carefully. These components offer greater flexibility but also expand where data flows and how actions are triggered. When designing scenarios, review how agents make decisions, limit which tools they can call, validate code modules before production use, and apply clear rules for sharing and reusing subscenarios to ensure predictable and secure automation across teams.
Security for Make.com integrations should evolve with your automation landscape.
Enterprises should conduct periodic reviews of all active scenarios. Remove unused connections, invalid tokens, and outdated workflows. Map which workflows handle sensitive data and confirm their compliance posture annually. Threat modelling helps uncover risks in new scenarios. Evaluate where data enters, where it leaves, who accesses it, and what authentication is involved. Document risks and assign owners.
Your automation team should receive training on secure integration practices, data minimization, credential hygiene, and proper use of Make.com features. A strong security culture is essential as automation grows across departments. Finally, maintain an incident response plan specific to Make.com. If a scenario malfunctions, you should know how to disable it quickly, revoke credentials, analyze logs, and restore operations. Regular tabletop exercises ensure your team can react effectively.
Make.com can be safely deployed in enterprise environments when supported by a strong identity model, secure connection management, careful data handling, network-level protection, and continuous governance. By integrating Make.com's native security features with enterprise controls, especially IAM, audit logging, API gateways, and workflow design principles, you create a reliable and scalable automation foundation.
Enforce SSO-only access with MFA inherited from your identity provider.
Related reading: IAM for SaaS
Limit their tool access, validate code execution paths, and treat each component as a governed runtime.
Related reading: AI Governance & Security Platform
Reco ingests Make.com identities, tokens, and workflow actions to map exposure paths and enforce controls.
Learn more: Identity & Access Governance