Microsoft 365 DLP helps protect sensitive information by detecting policy violations and triggering automated remediation actions such as blocking, warning, or alerting—across Microsoft cloud services and endpoints. It operates across Microsoft’s ecosystem, including Exchange Online, SharePoint, OneDrive, Teams, and Windows endpoints. Thus, DLP gives an organization the ability to block the sharing of sensitive data such as credit card numbers, health records, or financial data.
This article provides information on DLP policy configuration in Microsoft 365 with step by step instructions, suitable examples, and implementation tips for technical teams toward establishing an effective and scalable data protection strategy.
Microsoft 365 DLP supports the following locations:
You can apply a single policy across these services or scope it to specific workloads depending on your data protection needs. Each DLP policy can have multiple rules, conditions, actions, exceptions, and user notifications.
To create a DLP policy, follow these steps in the Microsoft Purview compliance portal:
Visit https://compliance.microsoft.com, then select Data loss prevention > Policies > + Create policy.
Templates are available for regulatory frameworks like GDPR, HIPAA, or PCI-DSS. These templates include predefined sensitive information types. You can also choose Custom policy to define your own rules.
Give the policy a name and description. Choose which services to apply it to—Exchange, SharePoint, OneDrive, and Teams. You can scope it to specific users, groups, or locations.
Rules determine the conditions for enforcement. You can define:
Example:
Enable policy tips to notify users in context (e.g., when drafting an email). Set up incident alerts to be sent to administrators or security teams.
You can choose to run the policy in test mode with notifications, test mode without notifications, or enforce it immediately. Testing allows you to tune the policy before rolling it out in production.
You can use PowerShell to review existing policies.
Connect-IPPSSession
Get-DlpPolicy | Select Name, Mode, State
This helps in auditing current policies, checking their mode (test vs. enforce), and verifying whether they’re active.
Microsoft Purview DLP also integrates with Microsoft Defender for Endpoint to enforce data protection on Windows 10/11 devices. Actions you can block include:
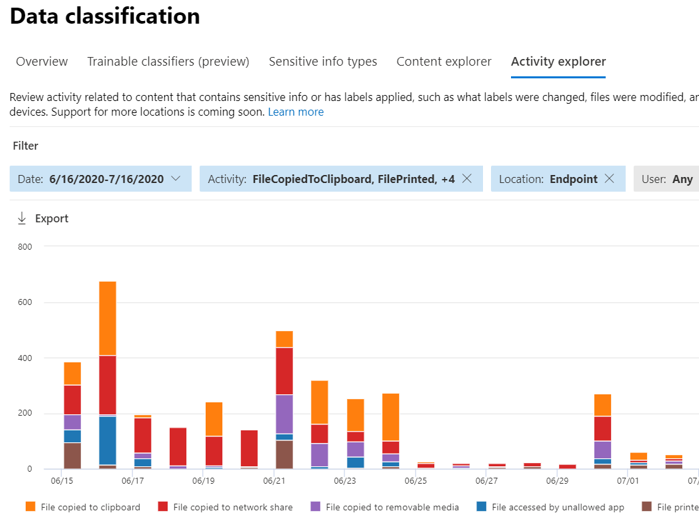
This is useful for preventing data exfiltration even when users are offline or working outside standard locations.
Built-in information types (e.g., U.S. Social Security numbers, credit card numbers) may not meet your organization’s specific needs. You can create custom sensitive information types using regular expressions and keywords.
For example, if your Employee ID follows the format EMP-xxxxxx, you can define a custom rule. This custom pattern can be uploaded using the Security & Compliance Center PowerShell or through the compliance portal.
Use EDM when you need to protect structured data such as patient records, employee databases, or financial spreadsheets.
This approach reduces false positives and is ideal for detecting specific identifiers (e.g., medical record numbers) rather than patterns alone.
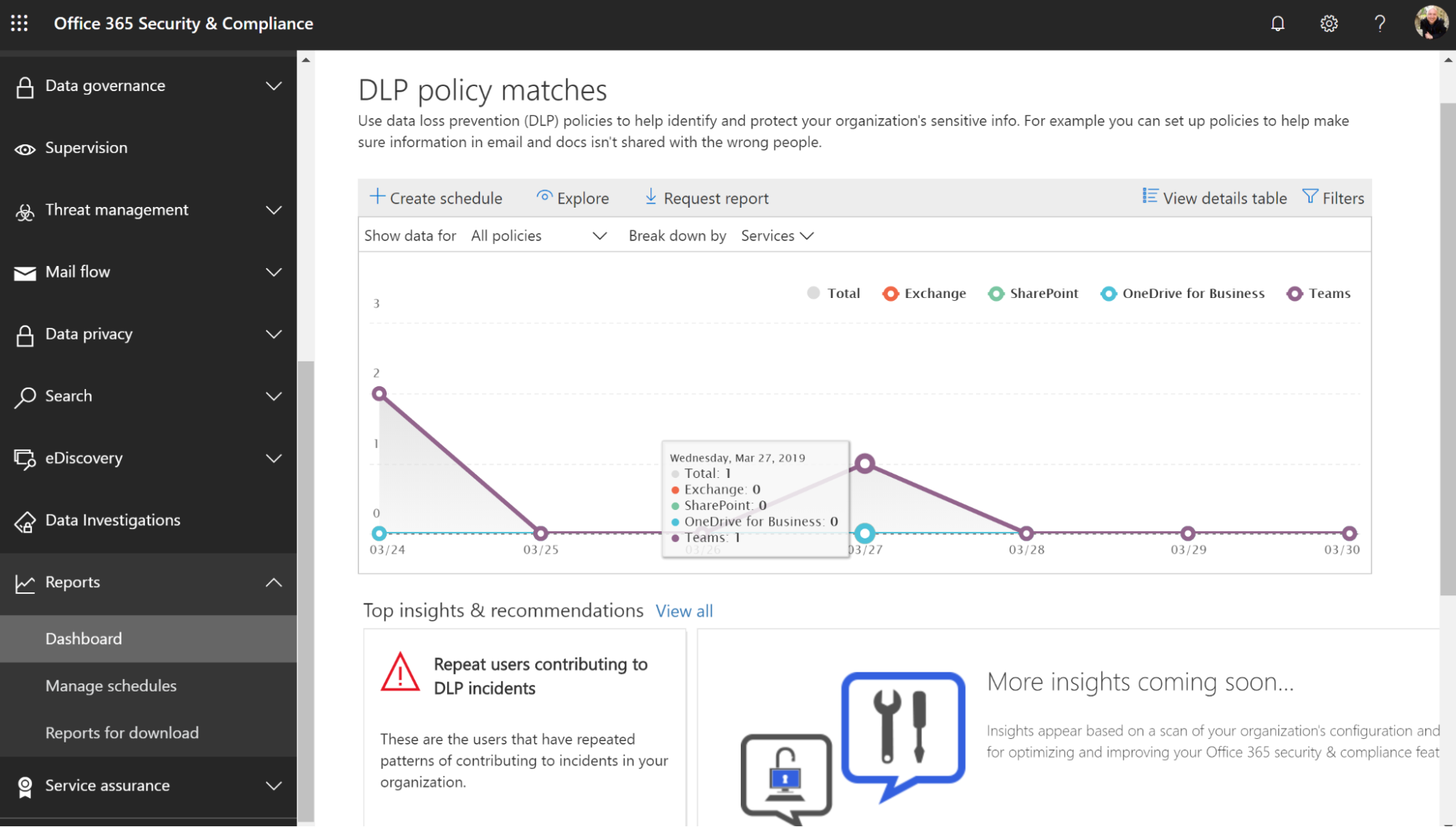
When the policy goes live, you must monitor it actively to make sure it is working properly and not creating any unwanted issues.
You can also export reports to your SIEM tool for long-term trend analysis.
DLP for Teams scans only text in chat and channel messages. File sharing in Teams is governed by SharePoint and OneDrive DLP policies.
Tips for Teams DLP:
This article describes the complete setup and configuration of DLP policies in Microsoft 365. Go slow; start small, carefully test a few policies, monitor the results, and then build up. A well-setup DLP approach can strongly shield your data without loss of productivity.