Traditional SIEM vs AI-Native Security Tools: The Next Generation of Cyber Defense
Traditional SIEM platforms played a defining role in shaping enterprise defense, but today’s cloud-native environments demand far more agility and intelligence. AI-native security tools are designed for this new era, learning dynamically from activity across systems and delivering real-time insights that help security teams act before incidents escalate.
What is Traditional SIEM?
Traditional SIEM is a security platform that aggregates and analyzes logs and events from across an organization’s network to identify potential threats. It relies on predefined correlation rules and manual tuning to detect anomalies, often operating on-premises with significant infrastructure requirements and limited scalability.
What are AI-Native Security Tools?
AI-native security tools are modern platforms built on artificial intelligence and machine learning to detect, analyze, and respond to threats with minimal human intervention. Unlike traditional SIEM systems that depend on static rules, these tools continuously learn from behavior patterns, correlate data across cloud, SaaS, and identity layers, and adapt detection logic as environments evolve. Their primary value lies in transforming detection from reactive rule-matching to proactive, behavior-driven defense.
Essential Capabilities of AI-Native Security Tools
The core capabilities of AI-native security tools define how they elevate detection and response beyond traditional systems.
Continuous Context Enrichment from User and App Behavior
AI-native tools continuously analyze user and application behavior to maintain a live model of normal activity across the environment. They monitor logins, access levels, data transfers, and application use to build evolving behavioral baselines. When activity diverges from expected norms, the system identifies anomalies with full context that includes user identity, device type, and session history. This ongoing enrichment allows early detection of insider misuse or credential abuse that static rules often miss.
Adaptive Detection Models That Learn from Environment Shifts
Modern AI-native platforms use machine learning models that adjust thresholds and detection logic automatically as environments change. When new applications, identities, or workloads appear, the models recalibrate without manual tuning. This adaptability maintains accuracy as cloud activity expands and user behaviors evolve, minimizing false positives that frequently burden traditional SIEM systems.
Integration With Identity, SaaS, and Data Security Ecosystems
AI-native platforms integrate seamlessly with identity systems, SaaS environments, and data security tools to unify context across all access points. By correlating authentication logs, cloud telemetry, and data movement, they reveal relationships among users, devices, and information that would otherwise remain hidden.
Automated Remediation Playbooks and Risk Scoring
AI-native platforms automate much of the incident response process through predefined playbooks and contextual risk scoring. When anomalies are detected, the system can isolate endpoints, revoke tokens, or apply access policies according to severity. Risk models assign priority levels so analysts can focus on high-impact threats while routine incidents are resolved automatically.
Unified Visibility Across SaaS, Cloud, and Endpoint Layers
AI-native platforms combine visibility across SaaS, cloud, and endpoint environments into one operational view. They correlate events from multiple systems to remove blind spots caused by disconnected tools.
Traditional SIEM vs AI-Native Security Tools: Key Differences
Traditional SIEM systems and AI-native platforms differ not just in architecture but in how they perceive and act on data. The following points outline the core distinctions that define how each approach impacts detection accuracy, scalability, and operational efficiency.
- Detection Approach: Traditional SIEM depends on static correlation rules and predefined thresholds, which require constant manual tuning. AI-native security tools apply learning algorithms that evolve with each new signal, identifying complex behavioral patterns and emerging threats that rigid rule sets often miss.
- Data Handling: In traditional SIEM, data ingestion is limited by storage, normalization, and processing capacity, often leading to blind spots or delayed insights. AI-native tools process structured and unstructured data in real time, correlating signals from endpoints, identities, and SaaS environments without manual normalization.
- Response Speed: Traditional SIEM relies heavily on analyst intervention to triage alerts and trigger responses. AI-native platforms automate much of this process by assigning contextual risk scores and executing playbooks instantly when critical events occur, reducing response times from hours to seconds.
- Cost and Scalability: Legacy SIEM deployments require significant infrastructure, maintenance, and license management. AI-native systems operate in cloud environments that scale automatically with data volume, lowering overhead while increasing analytical capacity.
- Insight Depth: Traditional SIEM offers surface-level visibility through event logs and rule matches. AI-native tools deliver deeper insight by mapping relationships among users, data, and applications, creating a context-rich understanding of intent, exposure, and risk across environments.
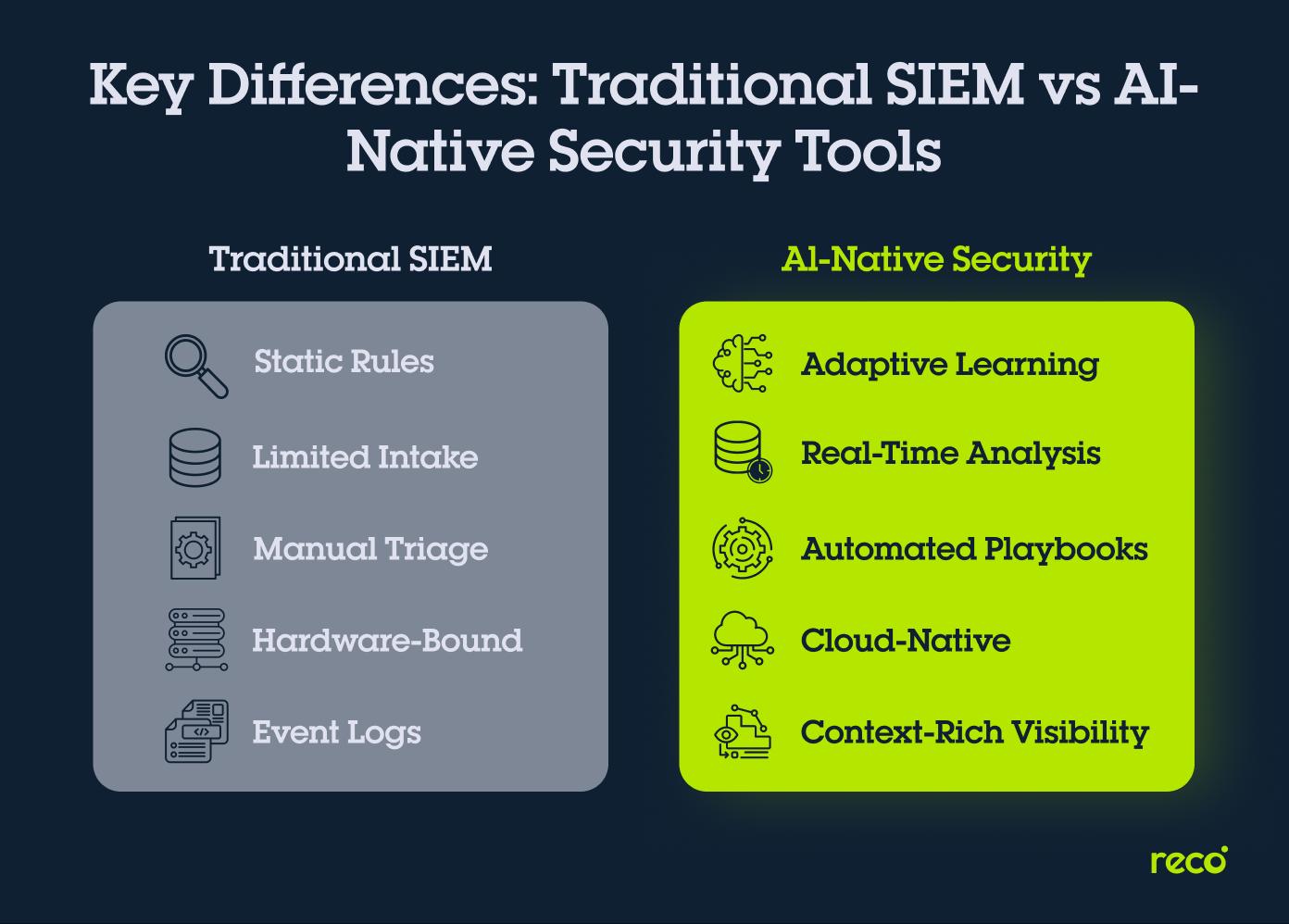
Comparison Table: Traditional SIEM vs AI-Native Security Tools
While both traditional and AI-native security solutions aim to detect and respond to threats, their underlying methods and operational models differ significantly. The table below summarizes the core contrasts that define how each performs in real-world security environments:
Benefits of Adopting AI-Native Security Tools
AI-native security platforms offer a transformative step forward from traditional detection systems by combining intelligence, automation, and adaptability. The following benefits show how these tools strengthen security operations and improve decision-making across complex environments.
- Real-Time, Context-Aware Threat Detection: AI-native tools process massive volumes of telemetry instantly and enrich alerts with behavioral, identity, and data context. This allows teams to spot threats as they occur, reducing detection latency and eliminating blind spots that rule-based systems overlook.
- Faster and More Autonomous Incident Response: Automated playbooks and contextual risk scoring allow AI-native platforms to contain or remediate threats immediately after detection. By minimizing manual triage, security teams can focus on investigation and strategy rather than repetitive response tasks.
- Reduced Operational Overhead and Complexity: Cloud-native AI platforms remove the need for on-premises infrastructure, manual updates, and rule maintenance. They streamline operations through automation and reduce costs associated with scaling traditional systems.
- Deeper Visibility Across Identities, SaaS, and Data Flows: These systems correlate user activity, access behavior, and data movement across multiple environments to reveal hidden relationships. This unified view helps security teams understand the full context of an incident rather than isolated alerts.
- Continuous Adaptation to Emerging Threats: AI-native detection engines evolve automatically as new attack patterns appear. Machine learning models adjust baselines and detection logic without manual tuning, maintaining accuracy as environments and threats change.
-
10 AI-Native Security Tools That Outperform Traditional SIEM
The following platforms represent the leading edge of AI-driven detection and response, each advancing enterprise security beyond the limits of traditional SIEM.
1. Reco

Reco is an identity-first SaaS security platform that builds a real-time relationship graph across users, applications, and data. Its AI continuously discovers connected SaaS apps, permissions, and data flows to expose excessive access and risky behavior. By correlating user, identity, and data activity through API integrations, Reco identifies insider threats and credential misuse with high accuracy while providing contextual insights for automated remediation.
Best for: Organizations managing complex SaaS ecosystems with identity-centric risk visibility needs.
Pricing: Quote-based on users and the number of integrations, offered directly and through the AWS Marketplace.
2. Hunters
Hunters provides an AI-native SOC platform that automates detection, investigation, and response. Its correlation engine transforms raw alerts into complete attack stories, using AI reasoning to highlight root causes and reduce analyst noise. The platform integrates across diverse data sources, enabling rapid prioritization and context-rich investigations without reliance on manual correlation rules.
Best for: Mid-sized and enterprise SOCs seeking automation to reduce analyst workload and accelerate investigations.
Pricing: Annual plans start around $280,000, depending on data volume and integrations.
3. Securonix
Securonix is a unified, cloud-native platform that integrates SIEM, UEBA, and SOAR to deliver behavior-driven detection and automated response. It analyzes telemetry from on-premises, cloud, and SaaS sources to detect anomalies, insider activity, and identity misuse. The platform’s AI models continuously learn from data patterns to enhance detection accuracy and streamline SOC operations through prebuilt playbooks.
Best for: Large organizations needing enterprise-grade analytics and integrated threat intelligence at scale.
Pricing: Subscription-based plans start at approximately $67,750 per year, with tiered packages available.
4. Exabeam
Exabeam’s New-Scale Security Operations Platform combines analytics, automation, and case management in a single environment. It uses user and entity behavior analytics to construct detailed activity timelines and detect credential abuse or lateral movement. The platform’s modular design allows flexible integration with existing pipelines while supporting centralized investigation and faster response cycles.
Best for: Security teams modernizing from legacy SIEM to analytics-driven detection and investigation workflows.
Pricing: Pricing begins at around $31,000 per year for 50 GB of daily log ingestion, with higher tiers (100 GB/day) costing approximately $53,000 annually.
5. Panther Labs
Panther is a cloud-native detection platform built around detections-as-code. Security engineers can author and version Python-based rules, automate testing in CI/CD workflows, and deploy at scale through a serverless architecture. The platform delivers high-performance querying, low-latency analytics, and transparent detection logic, making it ideal for modern, engineering-driven security teams.
Best for: Cloud-first organizations and engineering teams that prefer customizable detection workflows and serverless scalability.
Pricing: Pricing is quote-based and varies by data ingestion rate and feature set.
6. Vectra AI
Vectra AI applies machine learning and behavior analytics to identify advanced attacker techniques across network, cloud, and identity layers. It detects privilege escalation, lateral movement, and account compromise by analyzing traffic patterns and access behavior. The platform correlates signals across multiple domains to surface high-fidelity detections that accelerate incident investigation and response.
Best for: Organizations prioritizing identity-driven detection and lateral threat visibility.
Pricing: Monthly plans start at $499 for the Standard package and $1,299 for the Complete package.
7. Google Chronicle
Chronicle, part of Google Security Operations, unifies SIEM and SOAR functions with AI-driven investigation and automation. It ingests massive telemetry volumes, applies correlation through graph-based analytics, and supports YARA-L detection authoring. Integrated with Gemini AI, Chronicle enables natural language queries, automated summarization, and contextual recommendations for faster threat analysis.
Best for: Enterprises running on Google Cloud that need scalable data ingestion and historical search performance.
Pricing: Chronicle pricing is calculated by ingestion volume, with public-sector benchmarks showing rates of approximately £2,000 per terabyte per year.
8. Stellar Cyber
Stellar Cyber delivers an Open XDR platform that consolidates detection and response across network, endpoint, and cloud environments. It integrates SIEM, NDR, UEBA, and SOAR capabilities under a single interface to provide unified visibility and correlation. The platform uses machine learning to prioritize alerts, automate playbooks, and simplify operations for security teams of any size.
Best for: MSSPs and small-to-mid-sized teams seeking full coverage under one platform license.
Pricing: Stellar Cyber follows a simplified “one license, one price” model with quote-based packages available through its official pricing page.
9. Lacework

Lacework’s core technology now powers Fortinet’s FortiCNAPP, a unified cloud-native application protection platform. FortiCNAPP combines cloud security posture management, workload and container protection, and behavioral analytics to identify configuration risks, runtime anomalies, and potential exploits across multi-cloud environments. It integrates natively with Fortinet’s broader ecosystem to deliver continuous visibility, context-aware detection, and automated risk prioritization from build through runtime.
Best for: Cloud-native companies focused on securing workloads, containers, and compliance in dynamic environments.
Pricing: Average annual costs for mid-sized organizations start near $67,500, with customized plans available.
10. Anvilogic
Anvilogic is a detection engineering platform that operates across multiple SIEMs and data lakes. It enables teams to create, test, and deploy detection content programmatically, with AI assistance for rule recommendations and tuning. The platform provides version control, coverage mapping, and automation that help security teams modernize detection pipelines while maintaining compatibility with existing systems.
Best for: Enterprises with multiple SIEM platforms that want consistent, automated detection coverage.
Pricing: $80,000 per year for up to 2,000 employees and $185,000 per year for up to 5,000 employees.
Common Obstacles When Adopting AI-Native Security Tools
Transitioning to AI-native security platforms offers significant advantages, yet the shift can expose operational and organizational gaps. The following obstacles often determine how quickly and effectively teams realize the benefits of AI-driven detection and response.
- Data Quality and Integration Challenges: AI-native tools rely on large, diverse datasets to train and refine detection models. Inconsistent data formats, fragmented log sources, or incomplete SaaS and identity integrations can reduce detection accuracy and limit automation potential.
- Limited Internal AI Expertise: Many security teams lack in-house knowledge of data science, model tuning, and AI-driven analysis. This can slow deployment and limit understanding of how detection algorithms function or evolve.
- Change Management and Cultural Resistance: Moving from manual rule-based processes to autonomous systems can create friction within security operations. Analysts may distrust machine-driven recommendations or hesitate to relinquish manual control.
- Balancing Automation With Human Oversight: While automation accelerates incident response, excessive reliance on AI may overlook nuanced threats that require human judgment. Effective implementation requires defining clear human intervention points in response workflows.
- Regulatory and Compliance Alignment: AI models introduce new transparency and explainability concerns. Organizations must ensure that automated decision-making aligns with industry compliance frameworks and privacy regulations.
How to Transition from Traditional SIEM to AI-Native Security
Migrating from traditional SIEM to AI-native systems requires a structured approach that minimizes disruption while maximizing learning and automation gains. The table below outlines the essential steps and their objectives during this transition:
How Reco Bridges the Gap Between SIEM and AI-Native Security
Reco acts as a bridge between traditional SIEM frameworks and modern AI-native ecosystems by introducing real-time intelligence, automation, and SaaS-aware context into existing security operations. The following capabilities illustrate how it delivers that connection.
- AI-Powered Relationship Graph for User, Data, and App Context: Reco uses graph-based machine learning to map relationships between users, applications, and data assets. This visual and analytical model helps identify risky permissions, abnormal behaviors, and lateral access paths that traditional SIEMs often miss.
- Autonomous Threat Prioritization and Policy Enforcement: Through continuous monitoring and AI-driven scoring, Reco automatically prioritizes incidents based on risk and enforces adaptive access policies. This enables security teams to respond more quickly while maintaining granular control.
- Unified Visibility Across SaaS, Identities, and Access: Reco centralizes insights from diverse SaaS applications, user activities, and identity systems to create a unified view of an organization’s exposure. This eliminates data silos, ensuring that context is preserved across all investigation layers.
- Seamless Integration With SIEM and SOAR Tools: Reco integrates natively with existing SIEM and SOAR environments to enhance their detection logic and response automation. It extends traditional setups with AI-powered context enrichment, ensuring that legacy systems benefit from modern intelligence without full replacement.
Conclusion
AI-native security tools mark a turning point in cyber defense, moving from static event monitoring to intelligent, context-driven detection and response. They do not replace the principles behind SIEM but extend them with speed, learning, and automation that match today’s digital complexity. For organizations seeking deeper insight, faster decisions, and reduced manual effort, the shift toward AI-native platforms is not just progress - it is the foundation of modern security operations.
What are the biggest limitations of traditional SIEM solutions?
Traditional SIEM platforms face several operational and architectural constraints that limit their effectiveness against modern threats:
- Static detection logic: They depend on fixed correlation rules that struggle to adapt to new attack behaviors.
- High alert volume: Analysts face alert fatigue due to repetitive or low-value notifications.
- Limited scalability: On-premises infrastructure often cannot handle today’s cloud and SaaS data volumes efficiently.
- Manual tuning and maintenance: Continuous rule updates and system configuration demand extensive human oversight.
- Context gaps: SIEMs rarely connect signals across identity, data, and SaaS ecosystems, reducing detection accuracy.
How do AI-native security tools improve detection accuracy?
AI-native systems enhance precision and reduce false positives through several interlinked capabilities:
- Adaptive learning: Machine learning models evolve continuously as new behaviors emerge.
- Behavioral baselines: They establish normal activity profiles for users, devices, and applications to identify subtle anomalies.
- Contextual correlation: AI combines identity, access, and data context to understand intent rather than isolated events.
- Automated feedback loops: Each detection refines future accuracy, creating a self-improving system over time.
Can AI-native platforms replace SIEM completely?
Not yet entirely. While AI-native platforms can outperform traditional SIEM in context, speed, and automation, many organizations still rely on SIEM for regulatory logging, compliance reporting, and long-term data retention. The most effective strategy today is integration, where SIEM handles archival and compliance functions, while AI-native tools manage adaptive detection, prioritization, and response.
How does Reco integrate with existing SIEM and SOAR systems?
Reco complements and strengthens existing SIEM and SOAR workflows through direct and API-driven integration:
- Data enrichment: It feeds relationship context about users, apps, and data into SIEM pipelines for deeper analysis.
- Alert correlation: Reco contextualizes existing alerts to highlight access risks or policy violations.
- Automated playbooks: Integrations with SOAR systems allow incident response to trigger adaptive access controls instantly.
- Bidirectional visibility: Data flows between Reco and legacy systems remain synchronized, ensuring unified monitoring without redundancy.
What makes Reco’s AI-native approach different from legacy detection tools?
Reco’s design centers on understanding relationships between users, identities, and data rather than focusing solely on events. Its graph-based AI models continuously map how permissions and interactions evolve across SaaS environments, providing proactive detection of risky access patterns. This relationship-driven approach enables Reco to deliver insights that traditional, rule-based systems cannot replicate.






















.svg)