Top 10 ITDR Tools for Identity Security in 2026

Most cyberattacks nowadays begin with a stolen identity rather than a breached device. As organizations expand across SaaS, cloud, and hybrid environments, protecting user and machine identities has become a top priority. ITDR tools play a crucial role by detecting and containing identity-based threats before they disrupt operations.
Through continuous monitoring of logins, privilege changes, and unusual access behavior, ITDR platforms provide the insight security teams need to act quickly. They are now a defining part of enterprise defense, helping protect the digital identities that power modern business.
Understanding ITDR (Identity Threat Detection and Response)
Identity Threat Detection and Response (ITDR) focuses on identifying and mitigating attacks that target user and machine identities. These tools analyze login activity, privilege changes, and policy deviations to detect suspicious behavior that may indicate compromised credentials or insider misuse.
While endpoint tools secure devices, ITDR solutions protect the people and services controlling them. Integrated with identity and access management platforms, ITDR strengthens visibility, improves incident response, and helps maintain a consistent security posture across complex digital ecosystems.
10 Best ITDR Tools to Strengthen Enterprise Identity Security
Identity threats require purpose-built technology that can see beyond endpoints and detect misuse at the identity layer. The following top 10 ITDR tools represent the leading solutions in 2026, each offering distinct capabilities for securing users, machines, and SaaS identities across complex environments.
1. Reco
Reco continuously monitors user behavior, session activity, and privilege changes across SaaS environments to detect identity compromise, privilege drift, and insider misuse. The platform correlates activity across both human and machine identities and automates policy-based responses, such as enforcing MFA challenges, revoking risky sessions, or escalating alerts to security teams.
Best for:
Enterprises with extensive SaaS ecosystems that require unified visibility into user and machine identities.
Pricing:
Quote-based on users and the number of integrations, offered directly and through the AWS Marketplace.
2. Microsoft Entra (Defender for Identity)
Microsoft Entra, which includes Defender for Identity, identifies credential theft, lateral movement, and privilege escalation across on-premises Active Directory and Azure AD environments. It integrates with Microsoft 365 Defender to deliver unified threat detection and policy enforcement.
Best for:
Organizations using Microsoft 365 and Azure that want native identity threat detection and integration with existing Microsoft tools.
Pricing:
Microsoft Entra ID P1 is priced at $6 per user/month with an annual commitment, while advanced ITDR features are part of Entra ID P2 or Microsoft 365 E5, starting from $9.00 per user/month and $12.00 per user/month yearly with an annual commitment, respectively.
3. Palo Alto Networks (Cortex XDR + SaaS Security)

Palo Alto Networks combines Cortex XDR and SaaS Security to deliver correlated analytics across endpoints, identities, and applications. It detects credential misuse, insider activity, and privilege abuse while linking identity signals with endpoint and network telemetry.
Best for:
Organizations seeking a unified detection platform for identity, endpoint, and network events.
Pricing: Quote-based, available through Palo Alto Networks' enterprise licensing.
4. CrowdStrike Falcon Identity Protection
Falcon Identity Protection integrates identity analytics with endpoint detection to identify credential theft and privilege abuse. It uses behavioral modeling and adversary intelligence to detect attacks that exploit identity access points.
Best for:
Organizations already using Falcon for endpoint security and seeking consolidated identity visibility.
Pricing:
Falcon free trial for 15 days, Falcon Go at $59.99, Falcon Pro at $99.99, and Falcon Enterprise at $184.99 - all per device and billed annually.
5. Okta Identity Threat Protection
Okta enhances its identity platform with risk-based authentication and anomaly detection. It analyzes sign-in behavior, location patterns, and device context to trigger adaptive MFA or revoke access automatically when risks are detected.
Best for:
SaaS-first companies use Okta as their main identity and access management platform.
Pricing:
The Workforce Identity Starter plan starts at $6 and Essentials at $17, per user per month. The Professional and Enterprise plans are quote-based. The Customer Identity pricing starts at $3k per month for the Enterprise base platform.
6. Ping Identity Threat Protection
Ping Identity delivers adaptive risk-based protection through its PingOne Protect platform. It evaluates user behavior and device attributes to assess session risk in real-time, enabling step-up authentication or blocking high-risk activity.
Best for:
Enterprises that require identity threat detection integrated into single sign-on and access management frameworks.
Pricing:
The Customer Essential plan starts at $35k annually, and Plus at $50k annually. The Workforce Essential plan starts at $3 and the Plus plan starts at $6 per user, monthly.
7. CyberArk Identity Security Platform
CyberArk extends its privileged access management capabilities with identity detection and response. It continuously analyzes privileged account activity, enforces least-privilege access, and identifies credential abuse in real-time.
Best for:
Organizations managing high-value privileged and service accounts that require continuous risk detection.
Pricing:
Quote-based, available through CyberArk’s enterprise licensing program.
8. Semperis Directory Services Protector

Semperis Directory Services Protector monitors and protects Active Directory by detecting unauthorized modifications, persistence mechanisms, and domain-level attacks. It provides recovery tools for rapid rollback after identity-based breaches.
Best for:
Enterprises heavily reliant on Active Directory, seeking protection from identity-driven attacks and misconfigurations.
Pricing:
Quote-based, offered through Semperis’ enterprise licensing program.
9. Silverfort Unified Identity Protection

Silverfort unifies identity protection across cloud, hybrid, and legacy environments without deploying agents. It enforces adaptive authentication and continuous verification across protocols, detecting identity abuse that bypasses standard IAM systems.
Best for:
Hybrid enterprises that need agentless enforcement and protection for legacy and nonstandard authentication protocols.
Pricing:
Quote-based, available through Silverfort’s official pricing request portal.
10. SentinelOne Singularity Identity
SentinelOne’s Singularity Identity module uses deception-based defense to detect lateral movement and credential theft. It deploys decoy credentials and honeytokens to expose attackers while integrating identity telemetry into its XDR platform.
Best for:
Security teams using SentinelOne XDR who want to add identity deception and lateral movement detection.
Pricing:
Singularity annual packages start from $69.99 per endpoint for Core, $79.99 per endpoint for Control, $179.99 per endpoint for Complete, $229.99 per endpoint for Commercial, and quote-based for Enterprise.
ITDR Tools Feature Comparison Table
Each ITDR solution approaches identity protection differently, depending on its architecture and scope. The table below outlines how the leading tools compare in deployment models, coverage across SaaS and hybrid systems, and their unique detection and response capabilities:
Core Features Every ITDR Tool Should Have
Modern ITDR platforms combine advanced analytics, automation, and continuous monitoring to detect and contain identity-based threats across diverse environments. The features below outline the essential capabilities that distinguish comprehensive ITDR solutions from traditional identity or access management tools:
1. Continuous Identity and Access Discovery
Effective ITDR solutions continuously map all user, machine, and service accounts across SaaS, cloud, and on-prem environments. This ongoing discovery identifies dormant, shadow, or duplicate identities that attackers can exploit. By maintaining a real-time inventory of access relationships, teams can quickly detect gaps in identity governance.
2. High-Fidelity Anomaly and Behavior Analytics
Advanced behavior analytics form the core of identity threat detection. ITDR tools establish baselines for normal login activity, privilege changes, and session patterns. When deviations occur, such as logins from unfamiliar locations or excessive privilege escalation, alerts are generated with contextual precision that reduces false positives.
3. Privileged Access Monitoring and Risk Reduction
Privileged accounts represent the highest-value targets for attackers. ITDR systems must monitor privileged sessions continuously, detect risky elevation attempts, and provide insight into cross-domain permissions. Integrating these insights with access control policies ensures that only legitimate administrative actions are permitted.
4. SaaS-to-SaaS and Machine Identity Visibility
As SaaS adoption expands, machine-to-machine and SaaS-to-SaaS connections often bypass traditional security monitoring. ITDR tools should provide unified visibility into these non-human identities to prevent unmonitored data exchanges and automation misuse.
5. Automated Remediation and Policy Enforcement
Timely containment is critical once an identity-based threat is detected. Leading platforms include automated workflows that revoke tokens, force MFA re-authentication, or disable compromised accounts immediately. This minimizes dwell time and reduces the need for manual intervention during incidents.
6. Integration with SIEM, SOAR, and IAM Platforms
ITDR operates most effectively when integrated into the broader security stack. By sharing enriched identity telemetry with SIEM and SOAR tools, organizations gain faster correlation between identity anomalies and other attack vectors. Tight integration with IAM systems also enables seamless enforcement of policy-based controls.
7. Support for Zero Trust and Least-Privilege Models
Mature ITDR solutions reinforce the principles of Zero Trust by validating every access attempt continuously and ensuring that users maintain only the permissions required for their roles. Alignment with least-privilege practices limits lateral movement opportunities and strengthens overall identity security posture.
How to Select the Right ITDR Tool for Your Organization
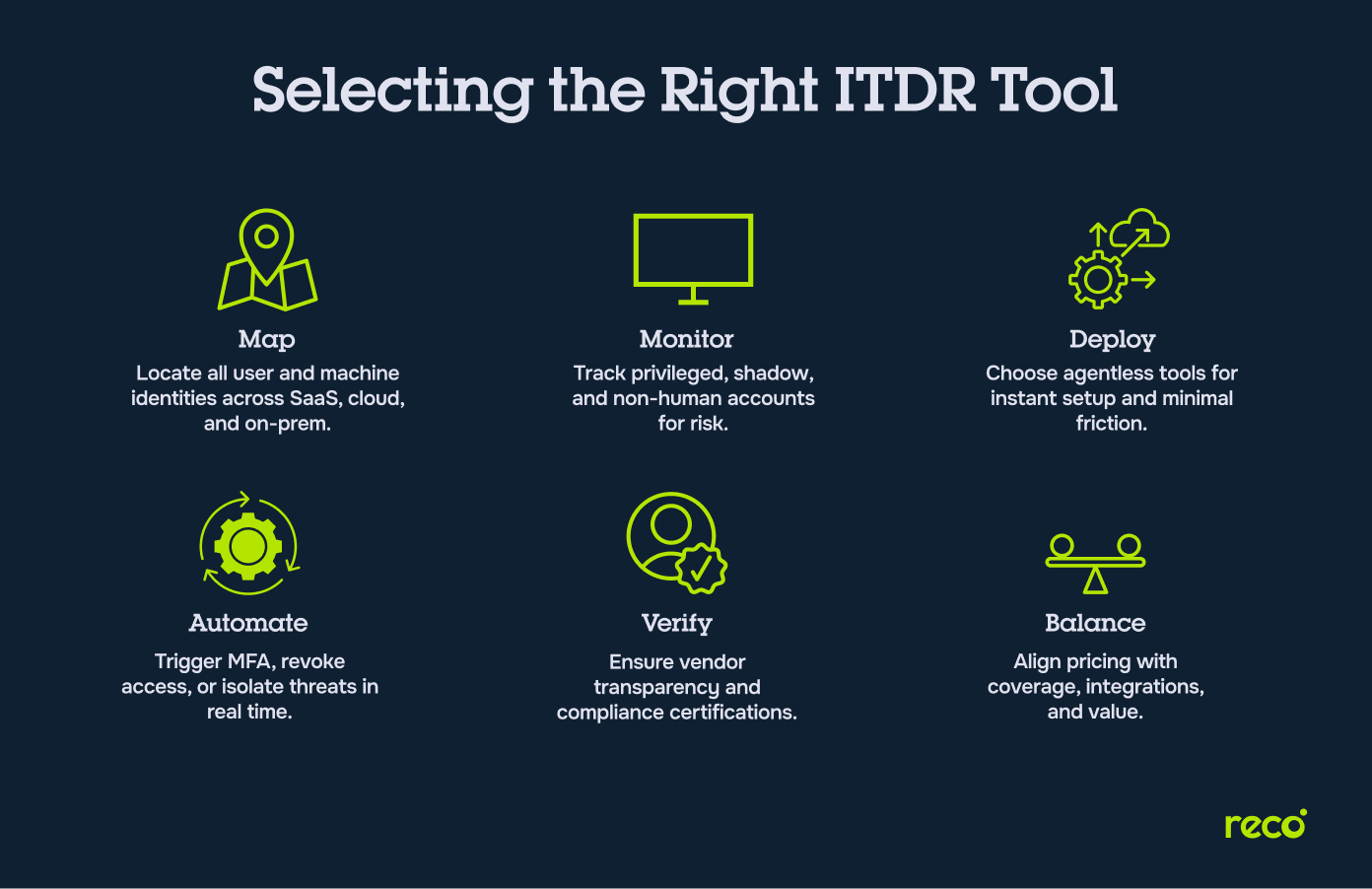
Choosing an ITDR platform involves more than comparing detection accuracy. The right solution should align with your organization’s identity architecture, security maturity, and operational priorities. The following factors help guide a structured evaluation process.
- Map Identity Risks Across SaaS, Cloud, and On-Premises Systems: Begin by identifying where identities reside and how they interact across environments. This mapping helps reveal blind spots such as unmanaged accounts, unmonitored service connections, or unused legacy credentials. A strong ITDR platform should correlate identity data from multiple sources, enabling unified visibility across all ecosystems.
- Assess Privileged Accounts, Shadow SaaS, and Non-Human Identities: Privileged and non-human accounts are often the most exploited attack paths. Evaluate tools that continuously monitor these identities and detect risky privilege elevation or misuse. Look for solutions that can surface hidden SaaS access (shadow IT) and machine identities that operate without direct human oversight.
- Look for Low-Friction, Agentless Deployments with Fast Time-to-Value: ITDR adoption should not disrupt existing infrastructure. Agentless or API-based deployments simplify integration and reduce operational overhead. Select vendors that offer quick onboarding, automatic discovery of identities, and actionable insights within days instead of months.
- Prioritize Tools with Automated Threat Response and Policy Controls: Speed matters in identity defense. The most effective platforms include automated workflows that revoke access, enforce MFA, or quarantine compromised sessions in real time. Evaluate the flexibility of policy engines and confirm that automated actions can integrate seamlessly with existing response systems.
- Validate Vendor Transparency and Regulatory Compliance Readiness: ITDR platforms often process sensitive identity and behavioral data. Verify that the vendor provides clear documentation on data handling, storage, and compliance with frameworks such as GDPR, ISO 27001, or SOC 2. Transparency ensures both operational trust and regulatory alignment.
- Balance Cost Models with Identity Coverage and Integration Needs: Pricing varies significantly depending on deployment scale and integration depth. Compare licensing models carefully, and ensure subscription tiers reflect your number of users, apps, and identity sources. Favor tools that balance cost efficiency with broad coverage and native integrations into your security stack.
Conclusion
Identity has become the foundation of enterprise security, reshaping how organizations protect users, systems, and applications. ITDR tools are no longer secondary layers but essential frameworks for detecting misuse, containing breaches, and preserving trust in every identity transaction.
As identity threats grow more complex and distributed, ITDR platforms will evolve toward greater automation, AI-driven analytics, and continuous visibility across hybrid and SaaS environments. The enterprises that embed these tools strategically will not only detect threats faster but also strengthen their long-term resilience, ensuring that identity remains a point of control rather than a point of compromise.
What are ITDR tools, and why do security teams need them today?
ITDR tools detect and respond to identity-based attacks by monitoring how users, service accounts, and machines actually behave across environments.
- Inventory identities across SaaS, cloud, and on-prem directories
- Monitor logins, privilege changes, and session activity continuously
- Alert SecOps when behavior deviates from normal baselines
- Trigger containment actions like MFA challenges or session revocation
Discover how ITDR reduces identity-based risk.
How do ITDR tools differ from traditional IAM or PAM solutions?
ITDR tools detect and respond to identity-based threats in real time, while IAM and PAM primarily focus on provisioning, access control, and credential management.
- IAM/PAM define who should have access by managing users, roles, and privileged accounts
- ITDR monitors how identities are actually used to detect abuse, compromise, or anomalous behavior
- IAM/PAM operate mostly preventively and statically
- ITDR adds continuous detection, investigation, and response across human and non-human identities
What are the biggest blind spots ITDR tools can uncover in SaaS environments?
Many SaaS identity risks remain unseen by traditional IAM systems. ITDR tools expose these overlooked areas by revealing where identity misuse often hides:
- Dormant or orphaned accounts that still have access to critical systems.
- Third-party integrations with excessive or outdated permissions.
- Machine identities performing high-risk operations without oversight.
- Gaps in MFA enforcement or inconsistent access controls across applications.
By uncovering these weaknesses, ITDR solutions provide visibility into identity risks that often evade standard IAM tools.
How does Reco combine ITDR with SaaS security posture management?
Reco unites identity threat detection and SaaS posture monitoring to help security teams see and act across every identity surface. Its combined visibility and automated control provide a deeper layer of defense through:
- Mapping both human and machine identities across connected SaaS platforms.
- Detecting privilege drift, policy misalignment, and insider misuse.
- Automating remediation through MFA challenges, access revocation, or alert escalation.
Learn more about Reco’s Identity Threat Detection and Response platform and how it unifies detection, prevention, and SaaS configuration security.
Can Reco detect lateral movement and insider misuse tied to identities?
Yes, Reco detects lateral movement and insider misuse by correlating identity behavior, permissions, and data access patterns across SaaS applications in real time.
- Ingest identity and activity signals across users, service accounts, OAuth apps, and AI agents
- Correlate behaviors across apps to identify abnormal access expansion, privilege hopping, or data overreach
- Apply business and data context (role, sensitivity, app ownership) to reduce false positives
- Trigger response workflows such as alerts, tickets, or automated containment actions
Understand how Reco detects threats in real time.
What role will AI and behavior analytics play in the future of ITDR tools?
AI is reshaping how ITDR platforms anticipate and respond to identity-based attacks. These technologies strengthen precision and adaptability by:
- Predicting identity threats before compromise through adaptive modeling.
- Reducing false positives by refining baselines with machine learning.
- Automating incident response based on real-time behavioral context.
- Enhancing continuous protection across hybrid and SaaS identity environments.
Explore how to Stop SaaS identity attacks in minutes with AI-driven incident response.






















.svg)