10 Best SaaS Security Tools to Protect Your Organization in 2026

The rapid expansion of SaaS adoption has brought unprecedented convenience, scalability, and flexibility to organizations. Yet this growth has also led to SaaS sprawl and the spread of shadow IT as employees adopt new applications without IT oversight. Critical data now often moves beyond the organization’s visibility and control, making identity-related breaches one of the fastest-growing threats in modern enterprise environments.
Traditional security solutions can't manage this level of complexity, leaving blind spots across user access, app integrations, and data sharing. Purpose-built SaaS security tools are now essential for addressing these challenges, providing continuous visibility, automated compliance monitoring, and identity-focused controls that strengthen risk management and access governance.
10 Best SaaS Security Tools in 2026
As SaaS environments evolve weekly, these ten platforms deliver the visibility, identity intelligence, and automated governance capabilities that modern enterprises depend on:
1. Reco
Reco continuously monitors user behavior, session activity, and privilege changes across SaaS environments to detect identity compromise, privilege drift, and insider misuse. The platform correlates activity across both human and machine identities and automates policy-based responses such as enforcing MFA, revoking risky sessions, or escalating alerts to security teams.
Best for: Teams that require identity-centric context across rapidly changing SaaS and AI app usage.
Pricing: Quote-based on users and the number of integrations, offered directly and through the AWS Marketplace.
2. AppOmni
AppOmni provides continuous SaaS posture monitoring, threat detection, and data exposure management across applications like Microsoft 365, Salesforce, ServiceNow, Google Workspace, and Workday. Its deep configuration analysis and automated policy enforcement help security teams detect misconfigurations, manage third-party connections, and maintain audit readiness.
Best for: Security teams that want deep configuration and connection insight in widely used enterprise SaaS.
Pricing: Vendr’s benchmark shows an average annual cost close to $97,000. AppOmni sells by subscription with quotes via sales or marketplaces.
3. Obsidian Security

Obsidian Security unifies SaaS posture management, identity threat detection, and data governance in a single platform. Using its SaaS Intelligence Graph, it maps user activity, detects anomalies, and integrates with ITSM, SIEM, and SOAR systems for contextual remediation and compliance reporting.
Best for: Organizations that want posture, identity, and threat response in one product, including browser-level protections.
Pricing: Obsidian advertises a free plan for up to 1,000 users. AWS Marketplace lists $100 per user per year for the paid platform. Enterprise plans are quote-based.
4. Adaptive Shield

Adaptive Shield, now part of CrowdStrike, offers continuous SaaS posture and identity monitoring integrated within the Falcon ecosystem. It identifies misconfigurations, tracks identity signals, and delivers continuous coverage across SaaS and AI applications, giving enterprises unified visibility within their security operations stack.
Best for: Enterprises standardizing on CrowdStrike that want a SaaS posture and identity risk in the same operational stack.
Pricing: Adaptive Shield is now integrated within CrowdStrike’s Falcon platform and follows its subscription-based pricing model. Purchases of Falcon Go are limited to a maximum of 100 devices at approximately $59.99 per device annually, Falcon Pro at approximately $99.99 per device annually, and Falcon Enterprise at approximately $184.99 per device annually, as per their website.
5. Valence Security
Valence Security strengthens SaaS identity and integration governance by analyzing SaaS-to-SaaS connections and non-human identities such as service accounts and OAuth tokens. It automates remediation, manages API key exposure, and provides guided workflows to reduce risk across interconnected business applications.
Best for: Teams that need to control third-party integrations and non-human identity risk across core business apps.
Pricing: Listed in partner marketplaces with contact-for-pricing. Vendr shows a median annual spend of $64,400.
6. Grip Security
Grip Security acts as a SaaS Security Control Plane that consolidates discovery, identity management, and posture monitoring into a unified framework. It continuously validates configurations, enforces least-privilege access, and runs automated remediation workflows to help enterprises control shadow SaaS and identity drift.
Best for: Organizations facing shadow SaaS at scale that want a connected posture and identity context.
Pricing: AWS Marketplace shows annual contracts that start at $300,000 per user band.
7. Nudge Security
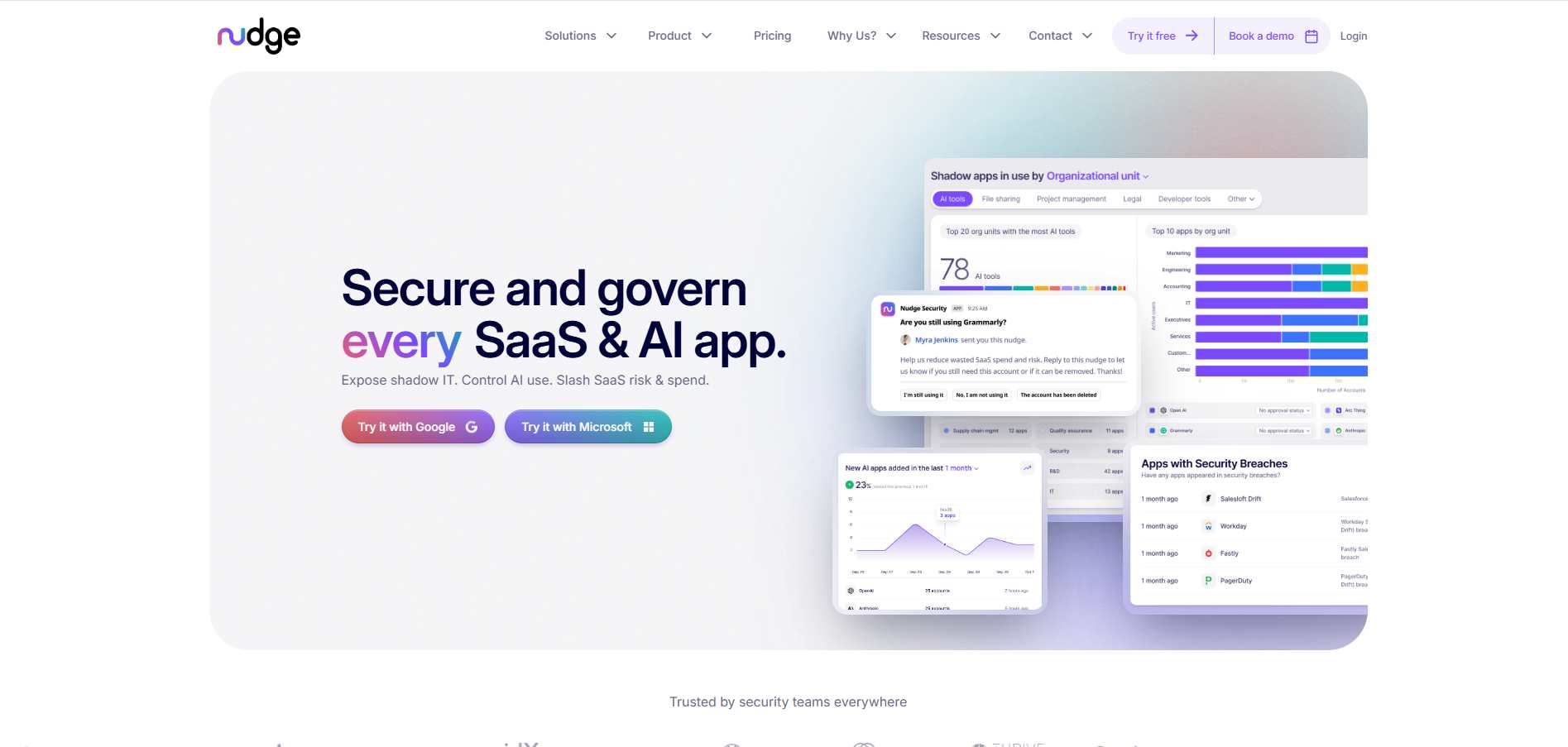
Nudge Security combines shadow SaaS discovery with employee engagement to help users adopt approved tools safely. It maps SaaS dependencies, monitors OAuth permissions, and delivers real-time “nudges” that guide users toward compliant behavior while alerting security teams to potential supply-chain risks.
Best for: IT and security teams that want quick discovery with user-friendly workflows to reduce unmanaged app risk.
Pricing: Public pricing starts at $5 per active user per month for teams in the 150 to 2,500 account range.
8. Nightfall AI
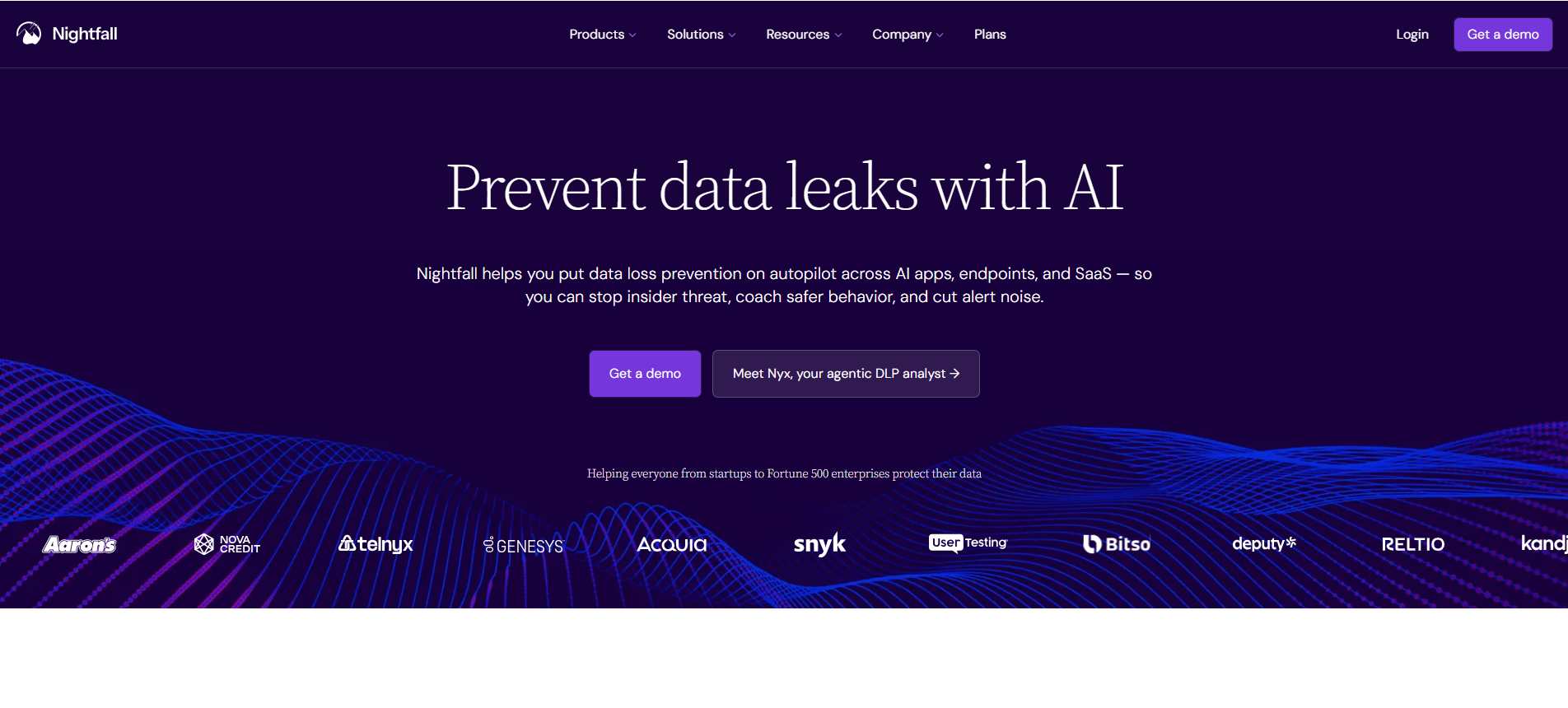
Nightfall AI provides data loss prevention (DLP) powered by machine learning to identify and protect sensitive information across SaaS and cloud collaboration tools like Slack, GitHub, Google Drive, and Jira. It scans data in motion and at rest, sending alerts to security teams through Slack, Jira, or email for quick triage.
Best for: Teams that need accurate data discovery and policy enforcement across collaboration and developer tools.
Pricing: Developer platform offers a free plan with 3 GB per month and an enterprise plan based on scanned data volume. Vendr shows a median annual spend of $23,250.
9. Symmetry Systems
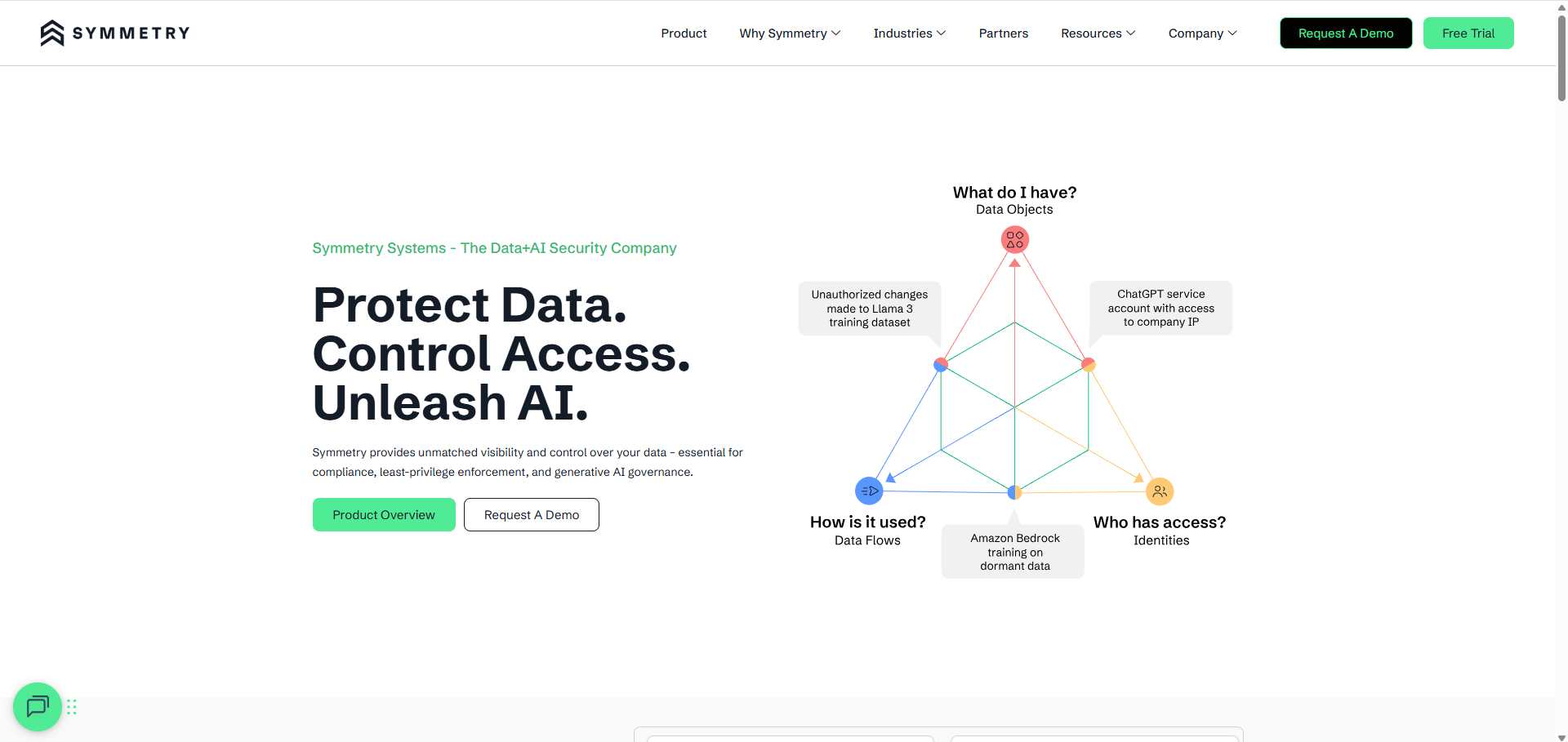
Symmetry Systems delivers data-centric security through Data Security Posture Management (DSPM) and Data Detection & Response (DDR). The platform maps sensitive data, monitors access, and applies identity-aware controls aligned with a zero-trust-for-data model to secure hybrid and SaaS-connected environments.
Best for: Enterprises that need data-centric governance across SaaS-connected stores and cloud services.
Pricing: Sold by contract through marketplaces with private offers, ranging from $50,000 to $100,000 annually.
10. DoControl

DoControl protects SaaS data access through granular policy enforcement, continuous posture monitoring, and automated remediation workflows. It provides deep visibility into sharing and access across collaboration tools like Google Workspace, Microsoft 365, and Box, helping organizations reduce data exposure and strengthen governance at scale.
Best for: Security teams focused on controlling data exposure and automating governance at scale.
Pricing: Vendr reports an average annual cost of $72,000 for buyers.
SaaS Security Tools Feature Comparison
Now that we’ve explored the leading SaaS security platforms in detail, it’s easier to see how their strengths align across discovery, posture, identity, and integration coverage. The table below compares their key capabilities, SaaS-to-SaaS risk visibility, and ideal use cases:
Key Features to Look for in a SaaS Security Tool
With the market crowded by overlapping capabilities, understanding which features actually make a difference helps narrow the field. The core functions below define what separates advanced SaaS security tools from legacy or partial solutions. Each contributes to better visibility, stronger identity control, and a more proactive defense posture.
- Centralized Discovery of All SaaS and Shadow Apps: A complete inventory of every sanctioned and unsanctioned application is the foundation of SaaS security. Centralized discovery exposes hidden tools adopted outside IT oversight and connects usage data with corporate identity stores. This eliminates blind spots, allowing security teams to measure exposure, set ownership, and take targeted action.
- Identity-Centric Access Visibility and Behavioral Analytics: Modern SaaS security depends on knowing not only which users have access but also how they behave within applications. Identity-centric analytics track permissions, sessions, and anomalies across accounts, devices, and roles. Behavioral baselines make it easier to detect compromised accounts and misuse before data loss occurs.
- SaaS-to-SaaS and OAuth Connection Control: Third-party integrations and OAuth tokens often expand the attack surface without explicit approval. Tools that map and govern these connections prevent excessive privileges and data flows between unrelated services. Proper control over inter-app trust relationships is critical for containing lateral movement and reducing integration-based risk.
- Automated Remediation and Policy Enforcement: Manual response cannot keep pace with SaaS scale. Platforms that automate remediation - revoking risky access, correcting misconfigurations, or enforcing compliance policies - help maintain consistency. Automation also ensures issues are addressed immediately, freeing teams to focus on high-impact analysis instead of routine fixes.
- Insider Threat and Data Exposure Detection: Data exposure is not always external. Advanced tools monitor sharing patterns, file transfers, and user actions that could signal malicious or accidental insider behavior. Continuous data-flow inspection helps detect risky uploads or unauthorized sharing before they turn into breaches.
- AI-Powered Risk Prioritization and Contextual Insights: Machine learning models can correlate events across multiple SaaS platforms to surface the risks that matter most. Instead of static alerts, these systems deliver contextual insights by weighing identity trust, data sensitivity, and behavioral anomalies. This prioritization helps security teams focus resources where the impact is greatest.
- Compliance Coverage for SOC 2, HIPAA, ISO 27001, GDPR: Meeting diverse compliance standards requires ongoing monitoring of configurations, access, and audit trails. SaaS security tools with built-in compliance mapping simplify evidence collection and reporting. Automated checks against frameworks like SOC 2 and GDPR maintain alignment without slowing business operations.
- Continuous Posture Monitoring and Alerting: Because SaaS environments change daily, security posture must be monitored in real time. Continuous assessment of configurations, permissions, and integrations provides early warning of drift or new exposure. Automated alerts keep teams informed so they can respond quickly and maintain control across the SaaS ecosystem.
How to Choose the Right SaaS Security Tool
Once you understand what to look for, the next step is selecting the tool that best fits your environment. The right choice depends on your SaaS footprint, team maturity, and operational priorities. The considerations below help narrow the field by focusing on depth, compatibility, and long-term scalability:
1. Evaluate Coverage for Your Critical SaaS Stack
Start by confirming that the platform supports your most important business applications, such as Salesforce, Microsoft 365, Google Workspace, or ServiceNow. Breadth of coverage ensures visibility across high-value data flows, while native integrations reduce the need for custom connectors or manual imports.
2. Assess Depth of Identity and Access Intelligence
SaaS security is now identity-driven. Evaluate how well the tool maps permissions, detects anomalies, and links identities to activities across apps. Solutions with deep access intelligence uncover overprovisioned accounts, unused roles, and risky privileges that traditional IAM systems may miss.
3. Verify Integration with IAM, SIEM, and Ticketing Tools
SaaS security rarely operates in isolation. Strong integration with identity platforms, SIEMs, and ticketing tools creates a connected response workflow. Look for APIs and native connectors that feed alerts and remediation steps directly into your existing operational systems.
4. Consider Deployment Ease and Agentless Capabilities
Agentless deployment simplifies rollout and avoids performance issues on user devices. Evaluate how quickly the tool can connect through APIs and OAuth to begin discovery. Tools that require minimal setup deliver faster time-to-value and make ongoing maintenance simpler for security and IT teams.
5. Look for Real-Time Context and Least-Privilege Insights
Continuous monitoring is only useful if it provides actionable context. Platforms that correlate identity, data sensitivity, and access behavior can highlight where privileges exceed actual need. This visibility supports least-privilege enforcement and reduces the attack surface without disrupting productivity.
6. Balance Pricing Against Breadth of Integrations and Scale
Pricing models vary widely, from per-user to per-connection or tiered annual contracts. When comparing vendors, weigh the cost against integration coverage, feature depth, and scalability. The most cost-effective choice is one that grows with your SaaS landscape while maintaining visibility and control.

Conclusion
It would be safe to say that SaaS security is no longer about perimeter control but about managing identities, configurations, and data movement across a constantly expanding ecosystem. The tools highlighted above show how the market has matured from simple discovery toward continuous posture, identity intelligence, and automated remediation.
Choosing the right platform means aligning technical capabilities with business context. Focus on tools that deliver unified visibility, reduce complexity, and provide actionable insights instead of static alerts. With the right mix of coverage, context, and automation, organizations can keep pace with SaaS growth while maintaining trust, compliance, and control.
What makes SaaS security tools different from traditional CASB or DLP solutions?
SaaS security tools go beyond the network-centric visibility of CASBs or the content labeling used by DLP solutions. They address the unique identity, configuration, and integration risks that come with large SaaS environments.
- Identity and access awareness: Map user roles, privileges, and OAuth permissions across all connected applications.
- Configuration posture: Continuously assess and remediate misconfigurations that expose sensitive data.
- SaaS-to-SaaS integrations: Monitor and control third-party app connections that older security tools often overlook.
- Behavioral context: Detect unusual activity across sanctioned and shadow apps using real-time identity analytics.
Explore the breakdown in SSPM vs CASB.
How do SaaS security tools detect and manage insider threats?
Modern SaaS security platforms combine behavioral analytics with identity intelligence to uncover internal risks before they lead to data exposure.
- User activity monitoring: Track file sharing, downloads, and permission changes in real time.
- Behavioral baselines: Establish typical usage patterns to flag anomalies such as off-hour access or data exfiltration.
- Automated alerts and remediation: Apply policies that can immediately revoke access or restrict sharing.
- Data exposure detection: Identify sensitive records shared externally or across unapproved domains.
Explore the CISO’s Playbook for Insider Risk Management.
Can SaaS security tools help discover shadow and unmanaged SaaS apps?
Yes, modern SaaS security tools are specifically designed to discover and manage shadow and unmanaged SaaS apps that sit outside IT’s visibility. They do this by:
- API-based SaaS discovery: Analyzing identity providers (Okta, Entra ID, Google Workspace) and core apps to uncover unsanctioned SaaS usage tied to real users.
- OAuth and integration mapping: Identifying third-party apps, AI tools, and automations connected via OAuth, API tokens, or service accounts.
- Usage and access correlation: Linking discovered apps to user activity, permissions, and data access to assess real risk, not just presence.
- Governance and remediation workflows: Enabling security and IT teams to classify apps, revoke risky access, enforce approval flows, or block unmanaged integrations.
Learn how Reco detects Shadow SaaS.
How do SaaS security platforms support compliance and audit readiness at scale?
They continuously monitor configurations, access paths, and data exposure instead of relying on periodic audits.
- Track configuration drift across apps like Microsoft 365, Salesforce, and Workday.
- Maintain audit-ready evidence tied to identity and access events.
- Alert on policy violations that break compliance baselines in real time.
- Reduce manual evidence collection during SOC 2 or ISO audits.
Learn more about Automated SaaS Compliance Monitoring.
How does Reco use identity intelligence to enhance SaaS security posture?
Reco enhances SaaS security posture by using identity intelligence as the core signal to understand who has access, how that access is actually used, and where risk is emerging across SaaS environments. Specifically, Reco:
- Correlates identities across apps: Links human and non-human identities (users, service accounts, OAuth apps, AI agents) across SaaS platforms to map real access paths.
- Analyzes effective permissions and behavior: Compares assigned privileges to actual usage to uncover overprivileged accounts, dormant access, and privilege drift.
- Detects identity-driven threats: Uses behavioral analytics to identify anomalies such as unusual logins, risky session activity, lateral movement, or insider misuse.
- Drives automated posture improvement: Triggers workflow-based actions, like revoking access, enforcing MFA, or reducing permissions, to continuously tighten least-privilege posture.
Explore Reco’s Identity Threat Detection and Response solution.
What factors should organizations consider when budgeting for SaaS security tools?
Choosing a tool that fits both technical and financial goals requires balancing depth, integrations, and scalability.
- Coverage and integrations: Confirm native support for core SaaS platforms like Salesforce, Microsoft 365, or Google Workspace.
- Depth of insight: Prioritize tools that provide identity, configuration, and data context in one view.
- Operational overhead: Consider agentless options with simple API-based deployment.
- Compliance automation: Look for built-in mapping to SOC 2, ISO 27001, and GDPR controls.
- Growth alignment: Ensure pricing remains predictable as your SaaS portfolio expands.
Check our guide on Choosing Your SSPM vendor.






















.svg)