What the Salesloft Drift and ShinyHunters Breaches Reveal About SaaS Risk



The SaaS security ecosystem faced major disruption in the summer of 2025. First, ShinyHunters used social engineering to trick Salesforce users at Google and Workday into disclosing credentials and approving malicious OAuth apps. Shortly afterwards, a supply-chain attack on Salesloft’s Drift integration let cybercriminals steal OAuth tokens and access Salesforce data at hundreds of companies.
ShinyHunters Target Salesforce at Google & Workday
The first attacks were not the result of a Salesforce vulnerability but rather of social engineering carried out by ShinyHunters. The group used voice phishing (vishing) calls to impersonate IT or HR staff and trick employees into granting access to Salesforce.
Google confirmed that one of its corporate Salesforce instances was impacted in June 2025, exposing contact details for small and medium-sized business clients. Around the same time, Workday employees were targeted with similar calls that led to unauthorized Salesforce access. In multiple cases, attackers quietly extracted customer lists, support cases, and other CRM records before the unusual activity was detected.
Attackers exploited the human element (by vishing employees to gain initial access). Then, once they had a foothold, they employed a second technique: quietly installing a malicious OAuth app in the target’s Salesforce org. They persuaded someone to install what appeared to be a legitimate Salesforce integration (a trojanized version of Salesforce’s own data loader tool). By doing so, the attackers obtained an OAuth token, granting ongoing API access to the Salesforce environment without needing the user’s password again or setting off immediate alarms.
The malicious app had the same permissions as any approved integration, so it could query and extract data freely. Using this method, ShinyHunters pulled massive amounts of data from several companies' Salesforce databases (customer lists, support cases, etc.) before the unusual activity was noticed.
The Salesloft Drift Breach - A SaaS Supply Chain Attack
After the ShinyHunters breaches that affected Salesforce users at Google and Workday, another incident exposed how vulnerable SaaS platforms can be. This time, attackers hacked into Salesloft’s Drift chatbot integration with Salesforce.
The attackers stole OAuth authentication tokens for the Drift app, essentially the keys that allowed the app to connect to its customers' Salesforce instances. Armed with these tokens, they could impersonate the trusted Drift integration and gain unauthorized access to the Salesforce data of over 700 organizations.
Once inside those Salesforce tenants, the attackers quietly exfiltrated large amounts of data. They ran queries on Salesforce objects like accounts, contacts, opportunities, and cases, pulling out records in bulk. In many companies, the stolen data included business contact details – the kind of information that might seem mundane but is useful for follow-up attacks like spear phishing.
Even worse, at some organizations, the cybercriminals hit the jackpot by finding sensitive credentials buried in support case logs, such as API keys, cloud platform tokens, and even passwords that had been shared in troubleshooting conversations.
They covered their tracks by deleting query job logs to avoid detection.
Google’s security team later revealed the same threat group also compromised some Google Workspace OAuth tokens via Drift, accessing a few Gmail accounts that were connected to the chatbot. In some cases, the attackers even poked into Slack integrations. It was all part of a wider campaign abusing inter-SaaS trust, not a hack of Salesforce’s code, but an abuse of its ecosystem.
How Interconnected SaaS Creates New Security Risks
Both the ShinyHunters attacks on Salesforce users at Google and Workday, and the Salesloft Drift incident, point to a larger trend in cloud security: SaaS platforms are becoming more and more interconnected, and that interconnectedness can be a double-edged sword.
On one hand, integrations can dramatically boost productivity. Sales teams might link Slack with Salesforce to keep deals moving, or connect Google Calendar with Zoom to simplify scheduling. A revenue organization could even tie Salesforce CRM to HubSpot for data sync and to LinkedIn Sales Navigator for enriched prospect details. But the same connections also amplify risk.
A single weak point in one SaaS app can quickly cascade into others. The Drift chatbot breach proved this: a vulnerability in one integration didn’t remain isolated to Salesloft, it spilled into Salesforce, Google Workspace, and even Slack for some companies. The trust between these services became a pathway for attackers.
We saw a similar pattern in the ShinyHunters campaign. Once attackers tricked their way into a Salesforce org, they gained access to all CRM data and could use that information (like contact details or OAuth tokens) to pivot into other systems.
The reality is that SaaS apps rarely operate alone. Your CRM, email, file storage, chat, and AI tools are all linked through APIs and single sign-on. It’s efficient when it works, but if any one link is weak, attackers can move laterally across your cloud environment.
Securing just the primary app (like Salesforce) isn’t enough. You also have to consider the ecosystem around it. Every connected app, every browser plugin, and every API key becomes a potential entry point. Unfortunately, many organizations aren’t fully aware of all the SaaS apps employees have connected or all the data being shared.
This shadow IT and SaaS sprawl can lead to situations where, say, revoking a compromised token in one app might be overlooked, leaving a door open into another.
The Need for Dynamic SaaS Security Platforms
Traditional security tools (firewalls, endpoint protection, etc.) don’t easily extend into this tangle of cloud applications. To address the new breed of SaaS threats, companies are turning to dynamic SaaS security solutions, security platforms designed specifically for the cloud app ecosystem.
What does “dynamic” mean in this context? It means these solutions are built to adapt in real time to the complexity and constant change of SaaS environments, rather than relying solely on static rules or infrequent audits. Some capabilities of dynamic SaaS security platforms include:
Comprehensive Visibility
The solutions typically discover and inventory all the SaaS apps and integrations in use – including those that security teams might not know about. You get a complete view of connected applications and accounts across your environment, which is invaluable for spotting unexpected connections or shadow IT. For example, if an employee suddenly authorizes a new third-party app to access Salesforce, the security team will know immediately.
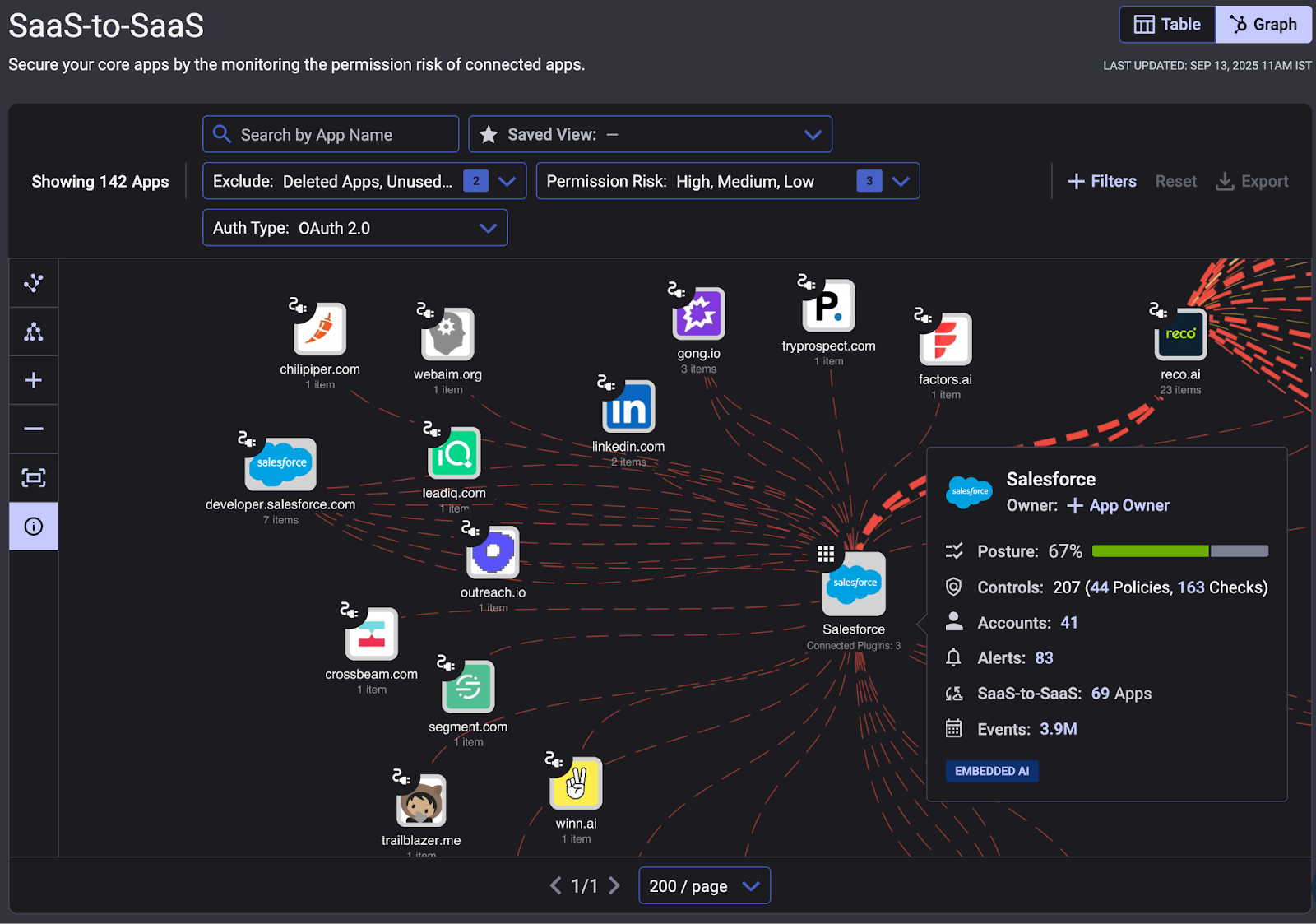
Adaptive Access Governance
Dynamic SaaS security tools enforce least-privilege principles and integration governance automatically. This can mean requiring admin approval for any new app connection to a core platform like Salesforce, or automatically flagging an OAuth token that requests more permissions than usual. By tightening who and what can link into your SaaS data, you reduce the risk of a Drift-like supply chain attack. To be more precise, had such measures been in place, a malicious Salesforce data loader app inserted by ShinyHunters would have been caught or blocked at the outset.
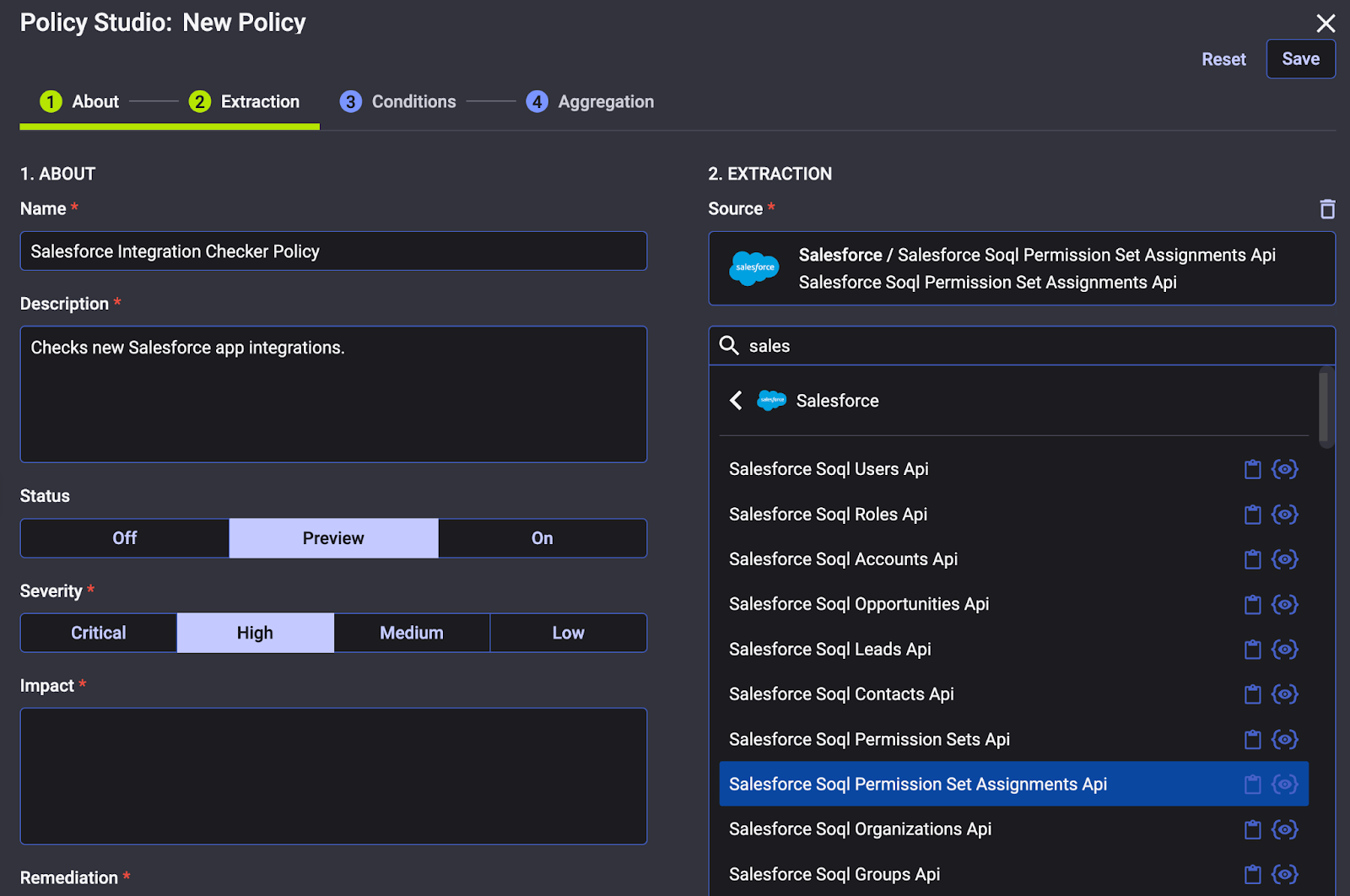
Monitoring & Anomaly Detection
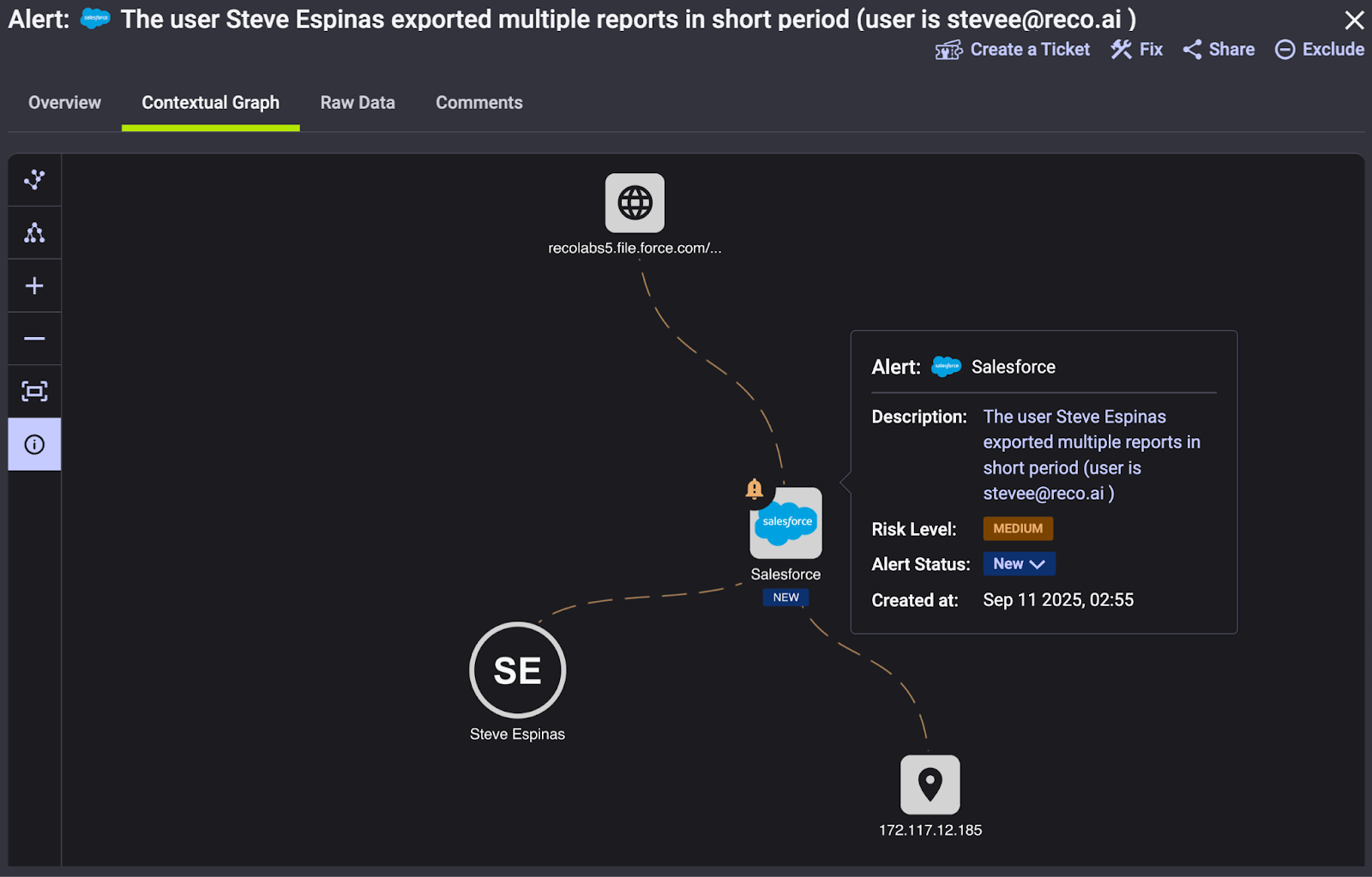
Perhaps most importantly, dynamic SaaS security solutions can monitor user activity and data flows within and between SaaS apps. It uses context and behavior analytics to detect the subtle signs of a breach. For instance, if a normally inactive service account starts querying thousands of records at 2 AM, or if an employee’s account suddenly performs a massive data export after a phone call to IT, those are anomalies that would trigger an instant alert. In the breaches we discussed above, this type of anomaly detection could have sounded the alarm on unusual Salesforce data access – limiting how much data was taken.
Take Your Next Steps With Reco
One goal of dynamic SaaS security is to help address the gaps that these 2025 breaches revealed. Companies need to keep an eye on their SaaS integrations, limit access to only what's necessary, and protect sensitive data stored in the cloud. A dynamic SaaS security platform helps with this by working continuously. It sees the cloud SaaS environment as something that is always changing and adjusts security rules and detection tools to match how users and apps behave over time.
This kind of solution would have been invaluable in stopping ShinyHunters (by blocking unapproved apps and catching the odd login behaviors) and in detecting the Drift breach (by flagging the token misuse early or the unusual query patterns). Dynamic SaaS security is about being as agile and interconnected as the SaaS apps themselves. It’s an emerging must-have layer of defense for companies that rely on a constellation of cloud services.
Click here to explore our dynamic SaaS security platform and register for our upcoming Salesloft Drift product demo on September 30 at 9AM PST/12PM EST.

Gal Nakash
ABOUT THE AUTHOR
Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.

Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.



%201.svg)



















.svg)