The Hidden Risk Inside Your SaaS Stack: How SaaS-to-SaaS Connections Expose Sensitive Data


The Unseen Problem Beneath SaaS Growth
SaaS adoption has exploded over the past decade, reshaping how organizations operate. Yet for every new app deployed, dozens of smaller integrations quietly join the party - connecting system to system, automating workflows, and exchanging data through OAuth.
Each one of those connections, called a SaaS-to-SaaS integration, requests permissions - known as scopes - to access or modify data in your core applications.
It’s a convenience most teams barely notice. But in the wrong circumstances, those same scopes can become a backdoor to your environment.
The Dark Side of Convenience
OAuth scopes define what a plugin can do: “read files,” “modify data,” “manage users.” Most users click Allow without hesitation, and the plugin gains lasting access, often far beyond what’s necessary.
Multiply that across hundreds of integrations inside a single workspace, and suddenly:
- Plugins can read or write sensitive data from multiple systems.
- Dormant apps retain access tokens long after they’re used.
- Security teams don’t even know which permissions exist or who approved them.
This is how small, invisible risks turn into full-scale SaaS breaches. Not through vulnerabilities in the main apps, but through trusted connections between them.
The Modern SaaS Threat Surface
The modern attack surface isn’t just your users or endpoints - it’s the connections between your apps.
Consider this chain reaction:
- A compromised plugin connected to Slack gains “read/write messages” permission.
- That same plugin also connects to Google Workspace, accessing shared files.
- Suddenly, data from one platform is available to another through an unmonitored OAuth tunnel.
Each connection extends your security boundary further into the unknown. And without centralized visibility, there’s no way to measure, let alone mitigate, that risk.
The Next Wave of SaaS Risk: AI Agents and MCP
The rapid rise of AI Agents and automated decision systems adds a new—and largely ungoverned—dimension to the SaaS risk equation.
AI Agents: When Automation Becomes Authority
AI Agents are designed to act on behalf of humans, they analyze data, make decisions, and even take actions like approving workflows, sending messages, or syncing records across apps. They connect deeply into your core SaaS platforms—Slack, Google Workspace, Salesforce, Jira—using OAuth tokens and API scopes to access the same sensitive data your team does.
Every AI Agent is a non-human identity (NHI) with high privilege, often spanning multiple systems. And unlike humans, they don’t go on vacation, change roles, or leave the company, their access persists indefinitely.
Without oversight, this creates:
- Untraceable automation chains where one agent triggers actions in another app.
- Over-permissioned integrations that can read, write, or delete data autonomously.
- Shadow identities that operate outside HR or IAM awareness.
In essence, AI Agents are multiplying your organization’s trust surface, expanding risk at machine speed.
Model Context Protocol: Centralized Power, Distributed Risk
To coordinate these agents, many organizations and AI ecosystems are introducing what’s known as a Model Context Protocol (MCP): a layer that governs how agents communicate, share data, and execute actions across environments.
MCP is powerful, it can orchestrate actions across every connected SaaS tool. But it also represents a single, systemic point of compromise. If an attacker gains access to the MCP or manipulates an agent’s permissions, they don’t just breach one app - they inherit control of every app connected through it.
A compromised agent or context protocol:
- Exfiltrate data from multiple systems simultaneously.
- Approve actions or workflows without human validation.
- Propagate malicious instructions to other connected agents.
What began as productivity automation became an autonomous breach vector.
The Hidden Layer of Non-Human Access
Both AI Agents and MCPs operate as non-human identities: entities with credentials, tokens, and permissions but no direct human owner. They blur the line between software and identity, making traditional identity and access management models obsolete.
These NHIs require the same—if not stronger—governance as human users:
- Which data can they access?
- Who approved their scopes?
- Can their actions be audited or revoked?
Without visibility into these relationships, AI-driven SaaS environments become black boxes: fast, efficient, and dangerously opaque. And at the center of it all are OAuth scopes: the invisible contracts that define what these agents, control planes, and integrations can see and do. Understanding them is the foundation for securing the AI-driven SaaS era.
Why Scopes Matter More Than Ever
Security leaders are starting to recognize that OAuth scopes are the DNA of SaaS risk, tiny fragments of permission that collectively define what every plugin can view, share, or change.
Understanding them means understanding:
- Who holds access - which users and service accounts have active tokens.
- What data is exposed - which permissions grant read/write access to sensitive resources.
- Where to act first - which integrations pose the greatest risk to the organization.
Without that clarity, even the most mature SaaS governance program is flying blind.
Where Traditional Tools Fall Short
Most SaaS management platforms stop at app discovery, they show which applications exist but rarely reveal how those apps interact or what permissions connect them. And when they do, it’s only for a limited subset, not the entire SaaS ecosystem.
That’s why many organizations still struggle with:
- Unmanaged OAuth tokens.
- Over-privileged third-party plugins.
- Compliance gaps around least-privilege enforcement.
In short: they see the “what,” but not the “how.”

How Reco Solves the SaaS-to-SaaS Blind Spot
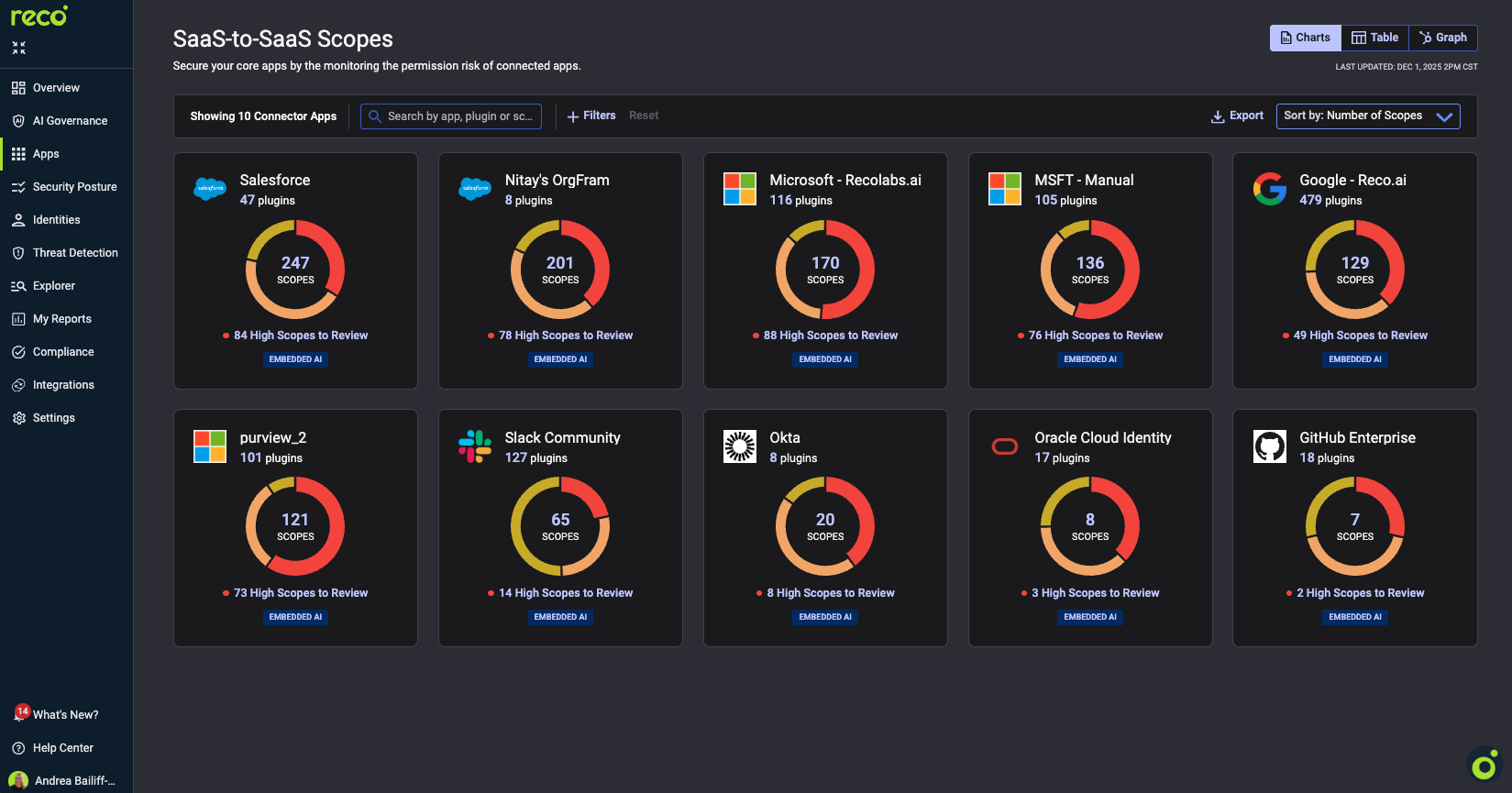
Reco is designed for exactly this problem. Its SaaS-to-SaaS Scopes visibility turns the invisible web of app-to-app connections into an actionable security map.
Here’s how Reco changes the game:
1. Complete Integration Discovery
Reco automatically identifies every plugin connected to your SaaS apps (from Google Workspace to Slack to Salesforce) including those installed by individual users. You get the full picture, not just the authorized ones.
2. Scope-Level Visibility
Rather than stopping at “what apps are connected,” Reco surfaces which scopes they hold - the exact permissions each integration has requested and which accounts are tied to them. It’s like an X-ray into your SaaS ecosystem.
3. Risk-Based Prioritization
Reco automatically classifies scopes as High, Medium, or Low risk based on what data they touch - so you can focus on the permissions that actually matter. No more chasing every alert; focus on the ones that could lead to a breach.
4. Actionable Governance
From that same view, teams can tag plugins, track authorization status, or export findings for audit and remediation. Reco turns visibility into governance - enabling true least-privilege SaaS access management.
Why This Matters Now
The line between a sanctioned SaaS app and a shadow integration has never been thinner. In the wake of recent high-profile breaches driven by over-privileged third-party plugins, it’s clear that visibility into scopes is no longer a nice-to-have, it’s essential.
Reco’s SaaS-to-SaaS Scopes feature gives security and IT teams the intelligence they need to:
- Detect risky or unnecessary connections.
- Investigate which accounts hold sensitive scopes.
- Act to revoke or restrict access before attackers exploit it.
It’s proactive defense in a space that’s historically been reactive.
Taking Back Control of Your SaaS Ecosystem
SaaS-to-SaaS connections aren’t going away, they’re the backbone of modern productivity. The challenge isn’t stopping them; it’s securing them. Reco brings visibility, intelligence, and control to this unseen layer of SaaS risk - so you can embrace third party applications without inviting exposure. Because in the world of SaaS security, the most dangerous access is the one you don’t know exists.




%201.svg)
.png)

















.svg)