Top 10 Identity Lifecycle Management Tools for SaaS Security in 2026
SaaS environments rarely fail because a user gets access. They fail because access stays behind after roles change, projects end, or identities go inactive. That is exactly what identity lifecycle management tools are built to control. In identity governance terms, Gartner defines identity governance and administration as managing the identity life cycle and governing access across on-premises and cloud environments.
10 Best Identity Lifecycle Management Tools for Modern Enterprises
Most organizations already have IAM in place, but lifecycle control is where real gaps show up across SaaS apps, contractors, service accounts, and third-party connections. The tools below are widely used to automate joiner-mover-leaver workflows and strengthen governance so access stays aligned as the environment changes.
1. Reco
Reco Identity Lifecycle Management turns manual identity processes into automated workflows and is designed to govern identities across the SaaS lifecycle. It highlights discovering and connecting every app, user, and connection in your stack, then monitoring and responding by catching new apps and changes in real time. It also positions lifecycle control as part of a broader Dynamic SaaS Security approach for SaaS sprawl and constant change.
Best for: SaaS first enterprises that want lifecycle automation plus continuous visibility as identities, access, and apps change.
2. Okta Lifecycle Management
Okta Lifecycle Management is a cloud-based identity lifecycle automation solution that streamlines onboarding, provisioning, user updates, and offboarding by connecting HR systems and directories to hundreds of applications. It automates joiner, mover, and leaver actions while centralizing identity processes, so users receive appropriate access on day one and lose it immediately when roles change or they depart.
Best for: Organizations that want automated provisioning and deprovisioning tied to HR and directory systems with extensive pre-built app integrations.
3. Microsoft Entra ID Governance
Microsoft Entra ID Governance is Microsoft’s identity governance solution that provides automated lifecycle workflows, access reviews, and entitlement management to govern user and group access across cloud and hybrid environments. It helps organizations continuously certify access rights, enforce policies, and remove unnecessary access as roles change or identities become inactive.
Best for: Enterprises using the Microsoft ecosystem that want lifecycle automation integrated with Azure AD, compliance reporting, and access certification.
4. SailPoint Identity Security Cloud
SailPoint Identity Security Cloud is a unified, cloud-native identity governance and security platform that automates lifecycle management, access provisioning, access certification, and compliance reporting for all enterprise identities. It uses AI-driven automation and analytics to ensure identities have appropriate access throughout onboarding, role changes, and offboarding while continuously enforcing least-privilege policies.
Best for: Large enterprises that need comprehensive identity governance with automated lifecycle controls and advanced risk and compliance visibility.
5. Saviynt Identity Cloud
Saviynt Identity Cloud is a converged cloud-native identity security platform that combines identity governance, access management, privileged access controls, and lifecycle automation across human and non-human identities. It provides automated onboarding, provisioning, access reviews, policy enforcement, and reporting to ensure identities receive appropriate access throughout onboarding, role changes, and offboarding.
Best for: Enterprises seeking a unified identity governance and lifecycle solution that spans cloud, hybrid, and hybrid-legacy environments with AI-driven insights.
6. One Identity Manager

One Identity Manager is an enterprise-grade identity governance and administration platform that automates identity provisioning, access updates, and offboarding while maintaining centralized control over user accounts and entitlements. It helps organizations govern who has access to what, enforce security policies, and satisfy compliance requirements by unifying identity lifecycle processes across on-premises, hybrid, and cloud systems.
Best for: Enterprises that need a modular IGA solution to automate lifecycle tasks while supporting complex hybrid environments and compliance workflows.
7. JumpCloud
JumpCloud is a cloud-native Directory-as-a-Service platform that centralizes identity, access, and device management into a single cloud directory. It automates identity creation, provisioning, deprovisioning, and access changes across user lifecycles, supports SCIM and SAML connectors for application provisioning, and provides unified user and access control from hire to departure.
Best suited for: Organizations seeking a unified cloud directory with automated user lifecycle management, access control, and cross-platform device support.
8. Ping Identity Governance
Ping Identity Governance is a cloud-native identity governance solution that provides visibility into who has access to what, automates access reviews and certification campaigns, and supports lifecycle actions such as provisioning and deprovisioning in line with compliance policies. It uses AI and machine learning to analyze entitlements, simplify access decisions, and help ensure that user access is appropriate and continuously reviewed.
Best for: Enterprises that require identity governance with automated access certification and lifecycle oversight integrated into a broader identity platform.
9. CyberArk Identity
CyberArk Identity is a workforce access management product that provides Single Sign-On and adaptive multi-factor authentication so employees can sign in securely to business applications. It uses Identity Flows to orchestrate access journeys and automate workforce identity processes, helping teams manage access changes across the user lifecycle and align controls for privileged access use cases within the broader CyberArk platform.
Best for: Organizations that want workforce SSO and adaptive MFA as part of a broader identity security stack.
10. Zluri
Zluri is a SaaS Management and Identity Governance platform that automates identity lifecycle processes - including user onboarding, role changes, access updates, and offboarding - across federated and non-federated applications. It enables IT teams to provision and deprovision users automatically, adjust access dynamically during role transitions, and revoke access on departure, while also providing visibility into SaaS usage and access policies.
Best for: Teams that want automated lifecycle workflows tied to broader SaaS discovery, governance, and access management across sprawling app portfolios.
Identity Lifecycle Management Tools Comparison Table
What Identity Lifecycle Management Means in SaaS-First Environments
In SaaS environments, identities are not limited to employees in a directory. Access is created through users, service accounts, API tokens, and third-party apps that connect directly to business data, often outside traditional IAM visibility.
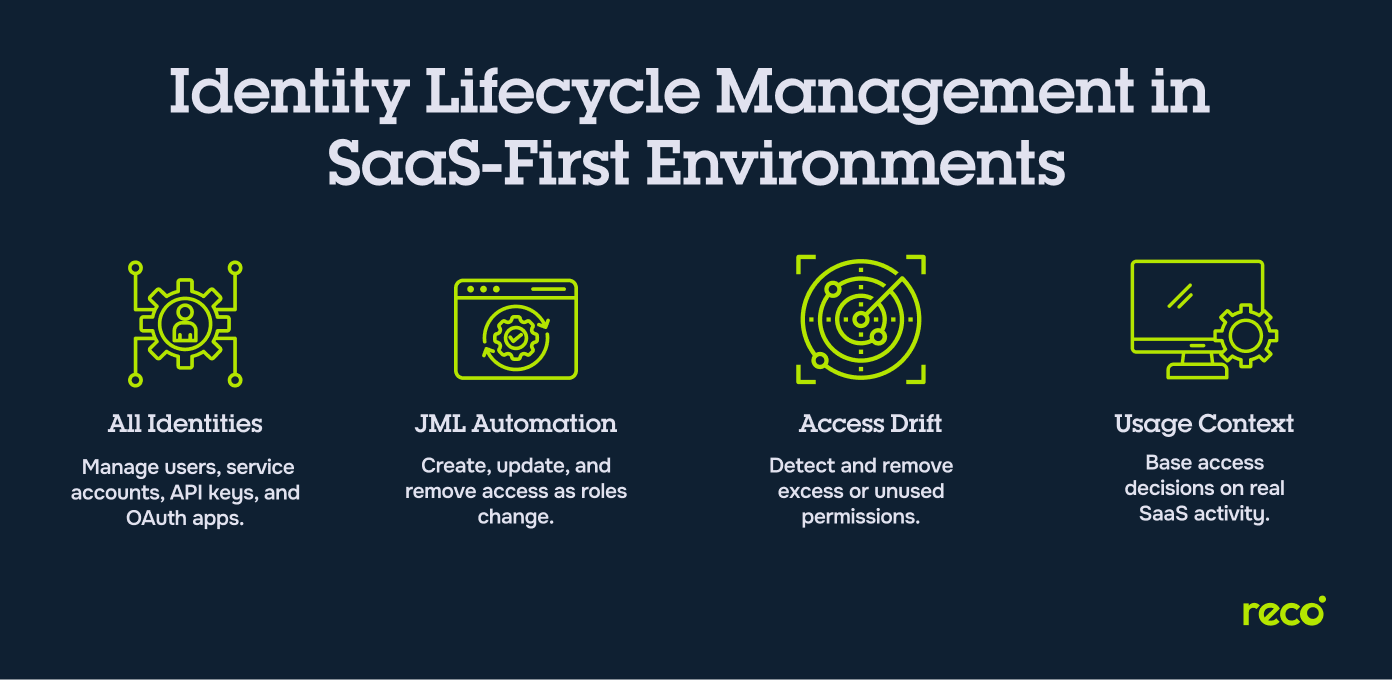
- Human and Non-Human Identities: Identity lifecycle management must cover employees, contractors, service accounts, API keys, and OAuth applications, since all of them can hold persistent access to SaaS data and systems.
- Joiner, Mover, Leaver JML Workflows: Modern ILM tools automate onboarding, role changes, and offboarding so access is created, adjusted, or removed as people join teams, switch roles, or leave the organization.
- Access Drift and Privilege Creep: Over time, users and service accounts accumulate permissions that no longer match their responsibilities, creating risk when old access is never removed.
- Identity Usage and Behavior Context: SaaS first ILM requires visibility into who is actually using applications, data, and integrations, so access decisions are based on real activity, not static role assignments.
Key Features to Look for in Identity Lifecycle Management Tools
In SaaS-first organizations, identity lifecycle management tools must go beyond basic provisioning and focus on visibility, automation, and continuous governance across all applications and identity types.
Common Use Cases for Identity Lifecycle Management Tools
Identity lifecycle management tools are used to ensure access remains appropriate throughout an identity’s tenure, whether that identity is human or non-human, and to reduce risk and operational burden in SaaS-first environments. Below are three core real-world scenarios where these tools deliver measurable value.
Employee Onboarding, Role Changes, and Offboarding
Identity lifecycle management automates provisioning of access when employees join, updates access when they change teams or roles, and revokes access when they depart. Without this automation, orphaned accounts and stale permissions accumulate, creating security and compliance gaps that are hard to track manually. Automated lifecycle workflows ensure access aligns with current responsibilities and is removed promptly at separation.
Contractor and Third Party Access Management
Modern enterprises grant temporary access to contractors, partners, and consultants across SaaS tools. Identity lifecycle management extends beyond employees to cover these external users by provisioning access based on contract terms and automatically removing access when engagements end. By treating all identity types through a unified lifecycle, organizations avoid lingering third-party access that could be exploited.
Service Accounts and Application Integration Governance
Today’s SaaS environments rely heavily on APIs, bots, service accounts, and other non-human identities for automation and integrations. These identities require lifecycle governance just like human users - from creation and permission assignment to ongoing monitoring and decommissioning when they are no longer needed. Effective lifecycle management includes visibility into these non-human identities and automated controls to prevent unused or overly privileged connections from persisting as hidden risks.
Identity Lifecycle Risks Traditional IAM Tools Miss
Traditional IAM systems are designed to control authentication and initial access, but they struggle to keep up with how identities and permissions actually change inside modern SaaS environments.
- Access Persistence Beyond Role Changes: Users often keep access from previous roles after moving teams or projects, leaving behind permissions that no longer match their responsibilities.
- Shadow Identities and Orphaned Accounts: SaaS apps, contractors, and integrations create identities outside central directories, resulting in accounts that remain active even after the owner is gone.
- Excessive Permissions Accumulated Over Time: Access is usually added to solve immediate needs but rarely removed, leading to privilege creep that expands the blast radius of any compromised account.
- Lack of Usage and Exposure Context: Traditional IAM tools show who has access but not who is actually using it, making it hard to spot risky or unnecessary permissions tied to real activity.
How to Choose the Right Identity Lifecycle Management Tool
Selecting the right identity lifecycle management tool requires looking beyond basic provisioning and focusing on how well a platform fits the realities of SaaS driven environments.
How Reco Redefines Identity Lifecycle Management for SaaS Security
Reco approaches identity lifecycle management differently by embedding continuous SaaS-native intelligence and automation into every stage of identity access and governance across all connected apps.
- Continuous Visibility Into the Full Identity Lifecycle: Reco delivers real-time visibility into every identity across the SaaS estate, tracking onboarding, role changes, access adjustments, and offboarding with timestamped audit trails so teams can see exactly what access exists and how it changes over time.
- Interaction-Based Risk Detection (Who Is Actually Using the Data?): Reco combines continuous discovery with identity analytics to map how users and applications interact across the environment, enabling behavioral context for risk assessments rather than just static permissions maps.
- Automatic Identification of Dormant and Orphaned Access: The platform identifies inactive accounts, stale privileges, and orphaned access remnants from incomplete offboarding so risk teams can flag and remediate them automatically with workflows.
- Managing the Lifecycle of Shadow Identities and OAuth Apps: Reco discovers and governs identities created outside central directories - including third-party apps, API identities, and OAuth connections - ensuring every identity type gets lifecycle oversight instead of being a blind spot.
- Prioritizing Identity Risks Based on Actual Business Context: Reco’s AI-driven agent correlates identity data with business context, exposing the identity risks that matter most, such as high-risk accounts and privilege escalation patterns, and prioritizes them for action.
Conclusion
Identity lifecycle management is moving from an IT workflow to a core layer of business risk control. As SaaS ecosystems grow more interconnected and automation replaces manual work, identities will increasingly act on behalf of people, systems, and external partners in ways that are harder to predict and harder to reverse. That makes static access models and periodic reviews less relevant with every passing year.
In 2026 and beyond, the organizations that stay ahead will be the ones that treat identity as a living system, continuously shaped by real usage, real integrations, and real business activity. Tools that can adapt to this reality will give teams the confidence to move faster without losing control.
What is the difference between identity lifecycle management and traditional IAM?
- Traditional IAM focuses on authentication and granting access, such as SSO and MFA.
- Identity lifecycle management focuses on how access evolves after it is granted, including role changes, inactivity, and offboarding across SaaS applications.
Explore Reco’s approach to Identity Lifecycle Management for SaaS.
Why is identity lifecycle management harder in SaaS-heavy organizations?
It is harder because SaaS environments create identities and access through users, service accounts, integrations, and OAuth connections that often exist outside central directories and change constantly as teams and applications evolve.
How do identity lifecycle tools handle non-human and service identities?
They apply lifecycle control to non-human access in the same way they do for users:
- Discover APIs, bots, and service accounts
- Track what they can access
- Review and remove stale or unused connections
Discover how to control non-human identity sprawl in SaaS.
How does Reco complement existing IAM or IGA tools like Okta or SailPoint?
Reco adds SaaS-native discovery and lifecycle visibility on top of directory-based IAM and IGA platforms by showing which applications, identities, and integrations exist outside provisioning systems and how access changes over time.
Can Reco detect identity lifecycle risks without enforcing disruptive access changes?
Yes. Reco focuses on visibility and prioritization rather than automatic enforcement:
- It identifies dormant, orphaned, or risky access
- It ranks risk based on real usage and business context
- It lets security teams decide how and when to remediate






















.svg)