Google AuraInspector: What the New Salesforce Security Tool Means for Your Organization



Google's Mandiant team recently released AuraInspector, an offensive security tool designed to identify misconfigurations in Salesforce Experience Cloud sites (formerly Community Cloud). While this tool has garnered significant attention, the vulnerabilities it exploits are not new and organizations should have been protecting against them long before this release. In this post, we'll explain what AuraInspector does, the broader context of Salesforce site security, and why proactive security measures are essential.
Understanding Salesforce Experience Cloud and the Aura Framework
Before diving into the security implications, it's important to understand what we're talking about.
Salesforce Experience Cloud allows organizations to create customer-facing portals, partner communities, and self-service sites. These sites enable external users to interact with Salesforce data without requiring full Salesforce licenses. Common use cases include customer support portals, partner relationship management sites, and knowledge bases.
Aura is Salesforce's component-based framework for building these dynamic web applications. It provides a rich set of UI components and a client-server architecture that communicates via Lightning Data Service and various APIs, including GraphQL endpoints. All sites have a guest user: a special user profile that exists regardless of site configuration. Even when "Guest users can see and interact with the site without logging in" is disabled, the guest user still exists and can still interact with the site through Aura. The challenge arises when the configuration between what should be public and what is public becomes misaligned, creating potential security vulnerabilities that could be exploited through this guest user context.
The Misconfiguration Problem: Guest User Sharing Rules
The core vulnerability that AuraInspector and similar tools exploit isn't a flaw in Salesforce itself, it's a misconfiguration in how organizations set up their sharing rules.
Sharing rules in Salesforce control which users can access which records. For Experience Cloud sites, administrators can configure sharing rules for guest users (unauthenticated visitors). The intended use case is straightforward: share specific, public-appropriate data like knowledge articles or product catalogs.
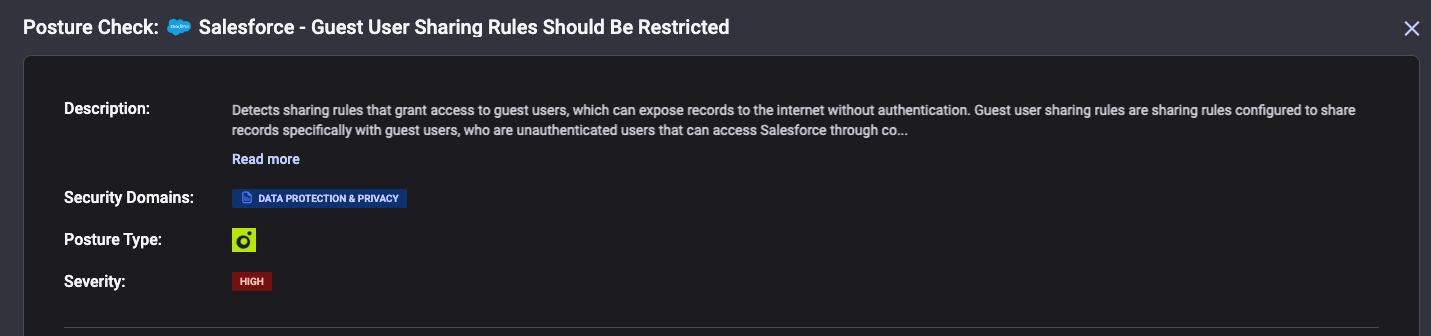
However, misconfigurations are alarmingly common. Organizations often implement overly permissive sharing rules that grant guest users access to entire object types rather than specific records. Even when object-level access seems appropriate, many fail to restrict sensitive fields, creating exposure vectors they never intended. Insufficient testing of what data is actually accessible to unauthenticated users compounds the problem, as does the tendency for legacy configurations to persist long after business needs have evolved.
These misconfigurations can expose a wide range of sensitive information, from personally identifiable information and business-critical data to internal communications found in Tasks, Events, and Alerts. Financial records and customer relationship data are also frequently exposed through these misconfigured sharing rules.
AuraInspector: Not the First, But Notable
Google's AuraInspector is significant for one key reason: it's the first publicly released tool to leverage GraphQL endpoints for data exfiltration from misconfigured Salesforce sites.
However, it's important to understand the context. Other tools have existed for years: "sret" and "cirrusgo" have been publicly available since at least 2022, capable of exploiting the same fundamental misconfigurations through different API methods. The GraphQL technique itself isn't new either. The first public mention of using Salesforce's GraphQL endpoint for this purpose dates back to 2021, documented by security researcher Nitay Bachrach, who is now a researcher at Reco.
The crucial point here is that AuraInspector is a symptom, not the disease. The real issue is that organizations have been running misconfigured Salesforce sites for years. The tool simply makes it easier to identify and exploit what was already exploitable.
What AuraInspector Does
AuraInspector automates the process of discovering accessible Salesforce Experience Cloud sites, enumerating objects and fields available to guest users, querying GraphQL endpoints to extract data, and exfiltrating potentially sensitive information that should not be publicly accessible. The tool makes it trivially easy for attackers—or security auditors—to identify and exploit these misconfigurations at scale.
Beyond AuraInspector: Advanced Attack Techniques
While AuraInspector represents a significant step in making these attacks more accessible, it's not the end of the story. More sophisticated threat actors are aware of additional techniques that go beyond what public tools cover. These include advanced enumeration methods that can identify and exploit Apex methods configured to run "without sharing,” a Salesforce directive that tells the system to ignore sharing restrictions. While these techniques can bypass certain detection mechanisms and be used for privilege escalation, the primary threat is their ability to bypass access restrictions entirely, allowing unauthorized access to sensitive data that should be protected.
Reco researchers have identified and reported such misconfigurations and vulnerabilities in major F500 companies.
Organizations cannot rely on simply defending against known public tools. A comprehensive security posture requires understanding and protecting against the full threat landscape including techniques that haven't yet been publicized.
Protecting Your Salesforce Environment: Actionable Recommendations
The first and most critical step is to conduct a comprehensive audit of all guest user sharing rules. Organizations should review every sharing rule that applies to guest users, ensuring they follow the principle of least privilege. Each rule should have a clear, documented business justification. This isn't a one-time exercise but rather the foundation for ongoing security.
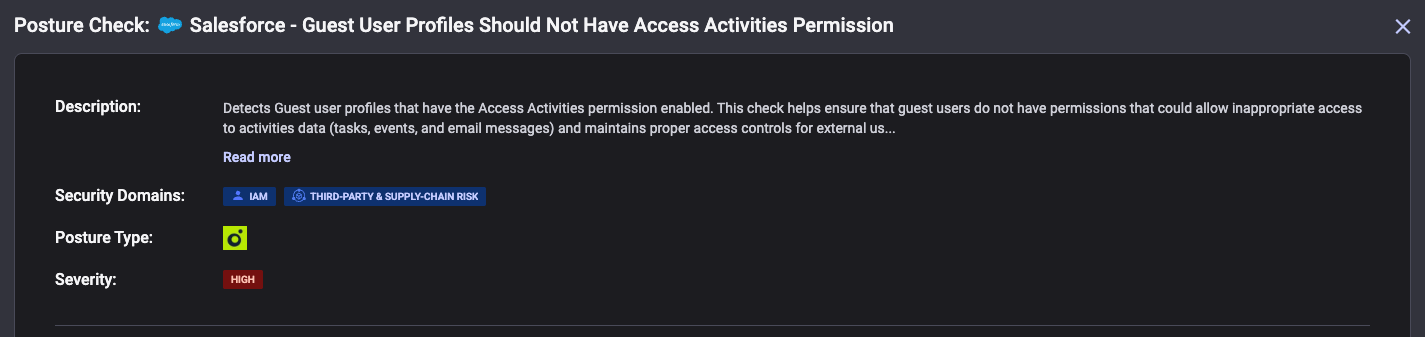
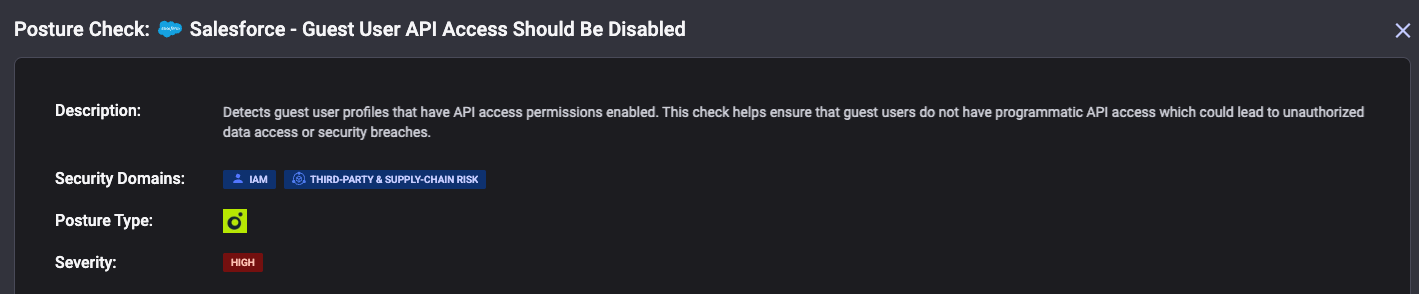
Equally important is disabling unnecessary permissions. Many organizations leave API access enabled for guest users even when there's no legitimate business need for programmatic access. The "Access Activities" permission is particularly dangerous because Tasks and Events frequently contain sensitive internal data. This permission used to be enabled by default until Reco researchers reported and demonstrated the security implications to Salesforce. In response, Salesforce changed the default settings and updated their best-practices guides to recommend disabling it. However, many older sites still have this permission enabled, creating a significant legacy security risk. Disable this unless it's absolutely essential. Where possible, disable access to entire objects rather than relying solely on sharing rules to prevent access to sensitive records.
Field-level security deserves special attention as well. Even when an object legitimately needs to be accessible to guest users, organizations should review field-level security settings to ensure sensitive fields are hidden. This defense-in-depth approach means that even if a sharing rule is too permissive, the most sensitive data remains protected.
Beyond these immediate actions, organizations need to establish ongoing security practices. Regular security audits should be conducted at least quarterly, with testing to verify what data is actually accessible to unauthenticated users. Security tools that continuously monitor for misconfigurations provide an important safety net. Change management processes should include security review for any changes to sharing rules or permissions, with a clear audit trail of all configuration changes. Finally, implementing comprehensive monitoring and logging for guest user access patterns, with alerts for unusual access or bulk data retrieval, can help detect exploitation attempts before significant damage occurs.
How Reco Protects Our Customers
At Reco, we've been detecting and alerting on these types of Salesforce misconfigurations long before AuraInspector's release. Our platform continuously monitors Salesforce configurations for overly permissive sharing rules and identifies when guest users have access to sensitive data types. When misconfigurations are detected, we alert security teams immediately and provide specific remediation guidance for each finding. We also track configuration changes over time to detect drift that might introduce new vulnerabilities.
Moreover, our research team—including researchers like myself who have been at the forefront of understanding these attack vectors—ensures that we're protecting against both current and emerging threats. This includes advanced techniques that haven't yet been incorporated into public tools, giving our customers protection against tomorrow's threats today.
The Bigger Picture: Proactive AI-SaaS Security
The release of AuraInspector underscores a broader truth about SaaS security: configuration is critical, and misconfigurations are common. As organizations increasingly rely on SaaS platforms like Salesforce, the attack surface expands beyond traditional network perimeters.
Effective SaaS security requires continuous visibility into configurations across all SaaS platforms, not just point-in-time assessments. Automated detection of security misconfigurations helps catch issues before they can be exploited. Understanding the context of what data is at risk allows for proper prioritization of remediation efforts. Most importantly, organizations need to shift from reactive response to proactive remediation, addressing vulnerabilities before they appear in attacker tools.
Conclusion
Google's release of AuraInspector is a valuable contribution to the security community, making it easier to audit Salesforce configurations. However, it's not a new vulnerability, it's a new tool for exploiting long-standing configuration issues.
Organizations should view this release as a wake-up call: if you haven't audited your Salesforce Experience Cloud sites for guest user misconfigurations, now is the time. Better yet, implement continuous monitoring to ensure these misconfigurations don't occur in the first place.
The threat landscape is constantly evolving, with new tools and techniques emerging regularly. Staying protected requires not just reacting to each new tool release, but understanding the fundamental security principles and implementing comprehensive controls.
Want to learn more about how Reco can help secure your Salesforce environment and other SaaS platforms? Request a demo to see how continuous SaaS security posture management can protect your organization from misconfigurations and emerging threats.




%201.svg)


















.svg)