Device Inventory – Unified Visibility & Security Insights


It’s hard to protect what you can’t see. Unmonitored endpoints and hidden devices can become open doors for attackers. If your team has ever struggled to reconcile multiple mobile device management (MDM) dashboards, endpoint detection and response (EDR) consoles, and identity provider (IdP) logs just to figure out what devices are in use, you know the pain of fragmented visibility.
We’re excited to announce a solution to these blind spots.
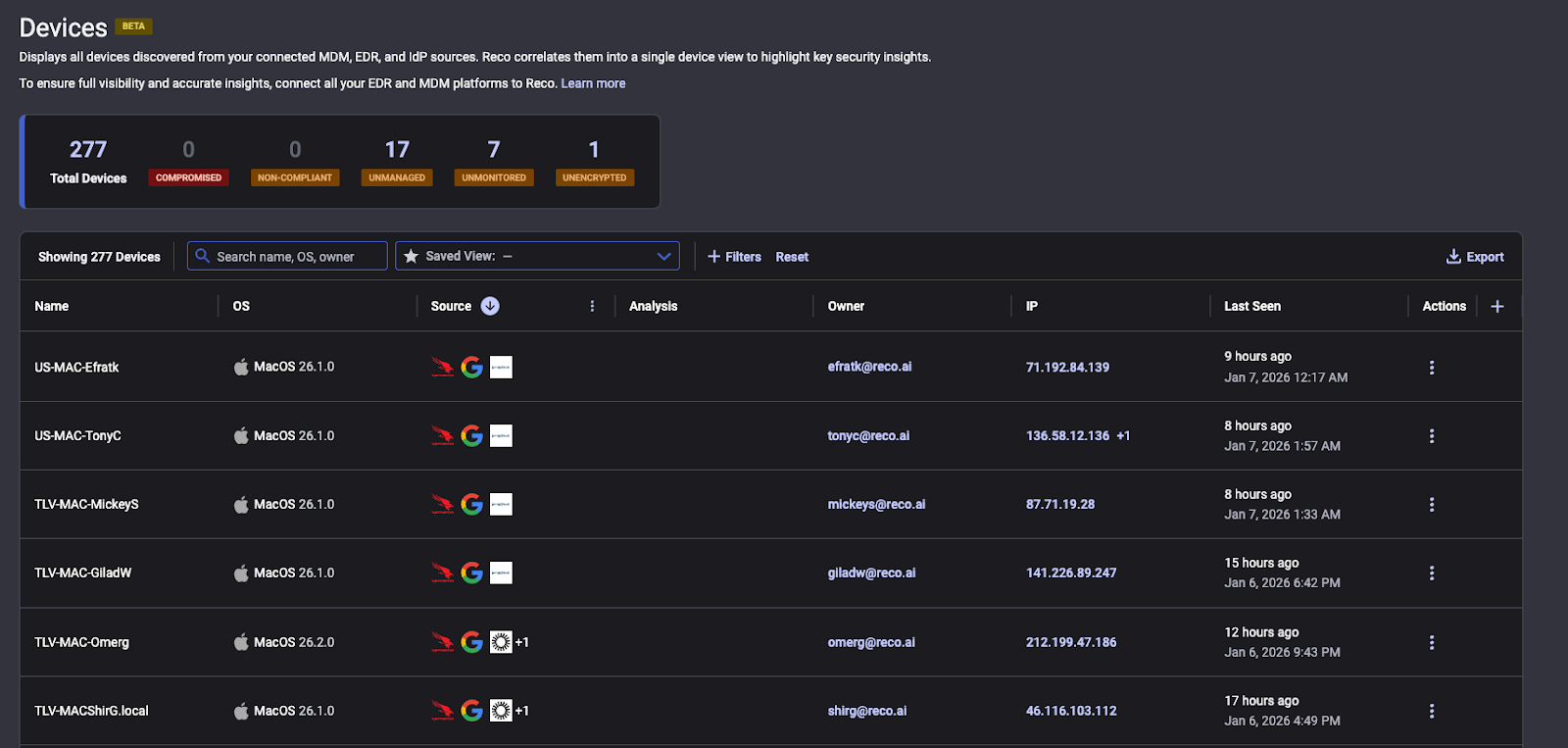
Reco’s new Device Inventory feature provides a single, consolidated view of every device across your organization, finally giving you unified visibility and actionable security insights for all endpoints, including clear signals for unmanaged, unmonitored, and unencrypted devices so teams can prioritize remediation faster.
What’s New - One Source of Truth for All Devices
Device Inventory (Beta) brings together data from your MDM tools, EDR agents, and IdP platforms into one unified interface. Instead of jumping between siloed tools (and dealing with spreadsheets or manual audits), you can now see all corporate devices and their security posture in Reco at a glance.
Reco automatically consolidates and correlates device attributes from these sources to create a single profile per real device, including tying each device to its owner’s identity for context. Reco support any EDR such as Palo Alto Networks Cortex XDR, CrowdStrike Falcon Shield, SentinelOne EDR, and Microsoft Defender for Endpoint or any MDM such as Microsoft Intune, Jamf, and VM Workspace One.
Some powerful insights surfaced by the Device Inventory include:
Rogue devices connected via your IdP
See any device that authenticates to your cloud apps (through Okta, Google, etc.) without being managed by IT. Nearly half of companies still allow employees to access resources on unmanaged devices with only credentials - our inventory will flag those stealth BYOD or personal machines.
Devices missing EDR or MDM coverage
Instantly spot endpoints that should be protected by an agent or enrolled in management but aren’t. Every asset missing a required security tool increases risk, so catching these gaps is important.
Posture and compliance status
For each device, quickly assess its compliance with policies - for example, whether disk encryption is enabled, OS up-to-date, and the device meets your MDM’s compliance rules. If an EDR has flagged a device as compromised or at risk, you’ll see that too.
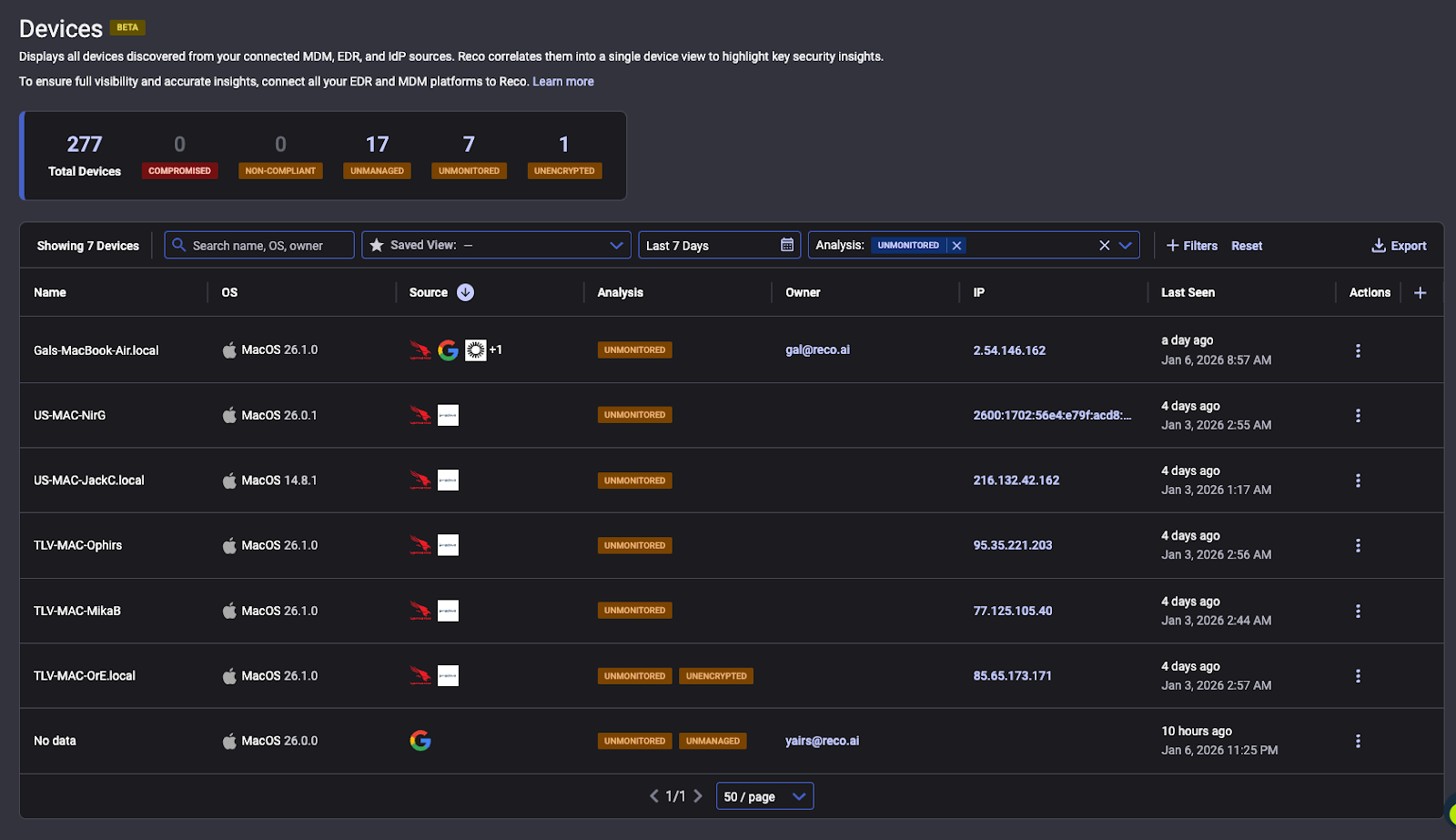
Why It’s Useful - Closing Endpoint Blind Spots
Having full visibility into your device ecosystem is essential for identifying security blind spots and strengthening endpoint protection. Traditionally, IT and security teams lacked a single source of truth for devices - MDMs showed some data, EDRs showed another, and identity platforms showed who was logging in from where.
This fragmentation meant gaps could go unnoticed. Security surveys confirm that inconsistent agent deployment and poor asset inventory lead to dangerous visibility gaps where attackers can hide and move freely.
Reco’s Device Inventory closes these gaps in real time. By automatically correlating feeds from MDM, EDR, and IdP, it immediately uncovers devices that are unmonitored or unmanaged - the very assets that would have slipped through the cracks before.
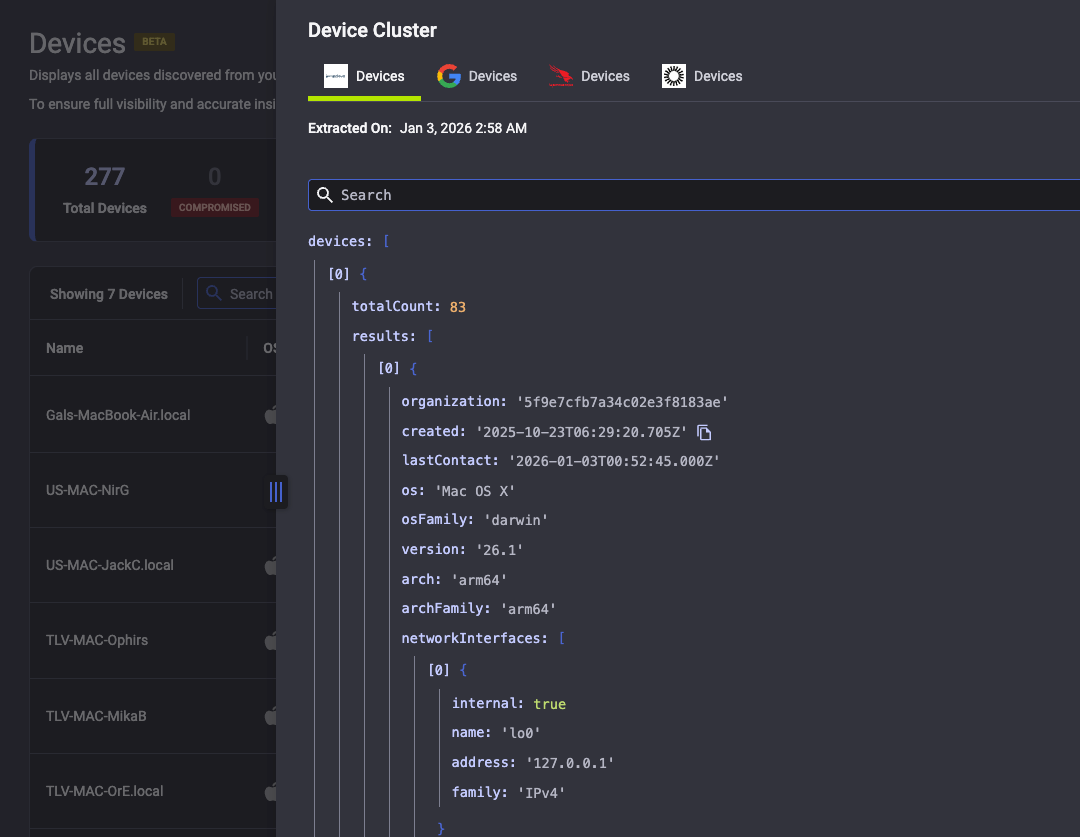
If an employee uses a personal laptop to log in to a corporate app, our inventory will identify that Windows device seen in Okta as unmanaged (not enrolled in the corporate MDM) and alert you to its presence. Without this unified view, such a rogue device might only be discovered in a quarterly audit or after a security incident, if at all. Now, it’s flagged as soon as it shows up.
Consolidating device data also helps you prioritize remediation effectively. Rather than juggling spreadsheets and multiple consoles, your team gets a clear, unified dashboard showing the risk areas. With Reco, you can instantly see which laptops don’t have an EDR agent, which machines are out of compliance, and which unknown devices are accessing company apps. This lets you focus on closing those coverage gaps before attackers exploit them.
There’s a compliance angle here as well.
A lot of frameworks and policies (ISO 27001, NIST CSF, etc.) require centralized asset tracking and proof of endpoint protection. It’s hard to fulfill that with fragmented inventories. By providing a consolidated device catalog with security health indicators, Reco makes it easier to demonstrate that every endpoint is accounted for and secured. Auditors love evidence of “no device left behind.” And if a device isn’t managed or is non-compliant, now you have a single report to pinpoint it and document corrective action.
A Stronger Security Posture through Unified Visibility
By unifying device telemetry and identity context into a single pane of glass, Reco helps you move from reactive firefighting to proactive management. You’ll know exactly which devices are in your environment and their security status, without stitching together information from multiple tools.
This feature is just the beginning of our expanded capabilities around devices.
As we refine the beta and gather your feedback, we’re already working on more ways to leverage this unified device data, from automated alerts (e.g. notifying you of a new unmanaged device connecting to your network) to deeper analytics and integrations. Our goal is to give you full visibility and control over every asset, so nothing falls through the cracks.
Try out the Device Inventory in Reco Today
Gaining full visibility into your device ecosystem will help you identify blind spots, reduce your attack surface, and strengthen your endpoint defenses from day one. Request a demo to see device inventory in action. With Reco as your single source of truth for SaaS and devices, you can finally stay one step ahead of the risks lurking in the shadows – and turn unknowns into insights.

Liron Ben Haim
ABOUT THE AUTHOR
Liron is a Product Manager at Reco and is also an experienced Software Engineer and Team Leader. Prior to joining Reco, Liron was a Software Engineer at Immunai and served in various software and security roles in the Israel Defense Forces.



%201.svg)
.png)


















.svg)