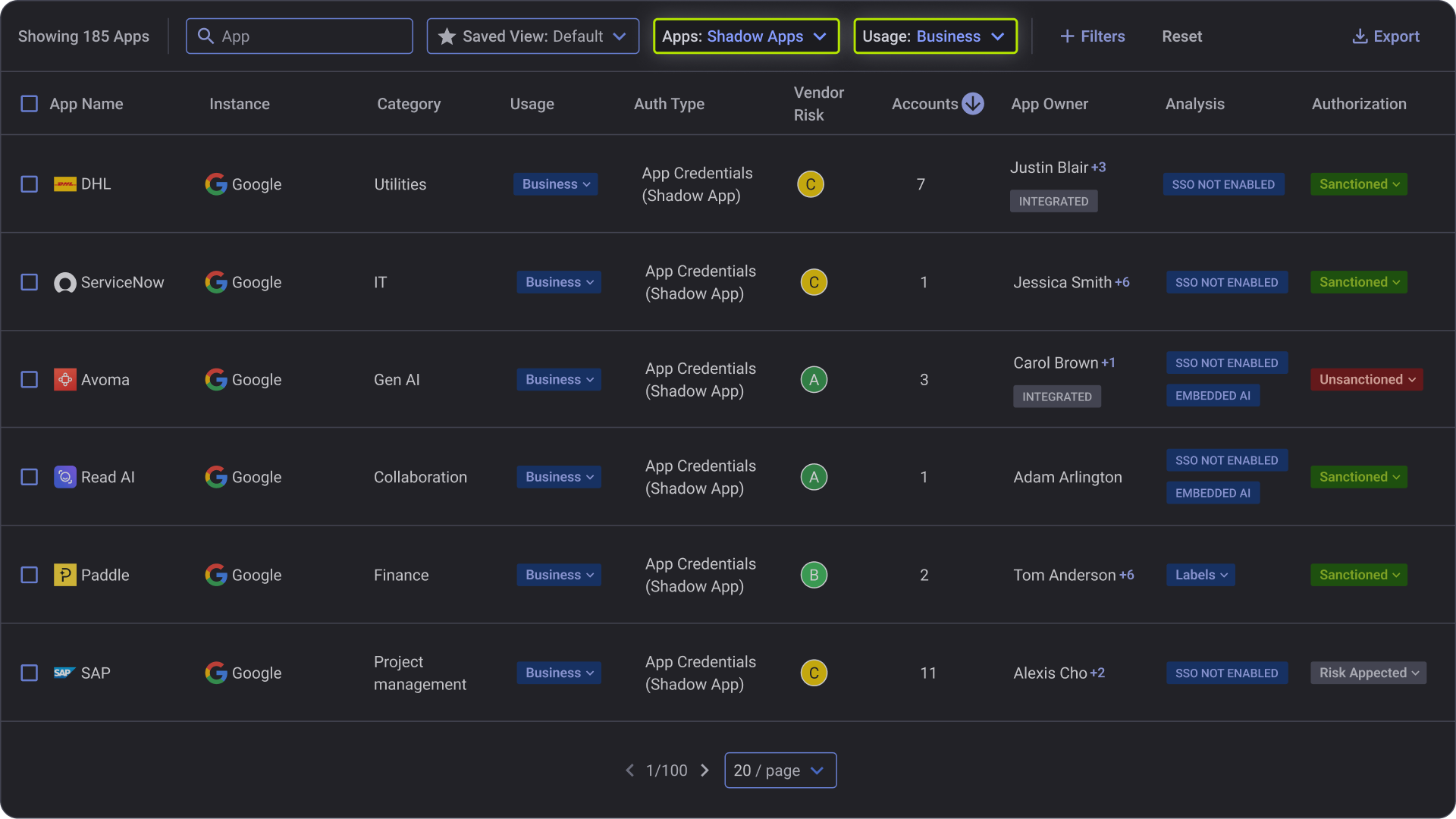
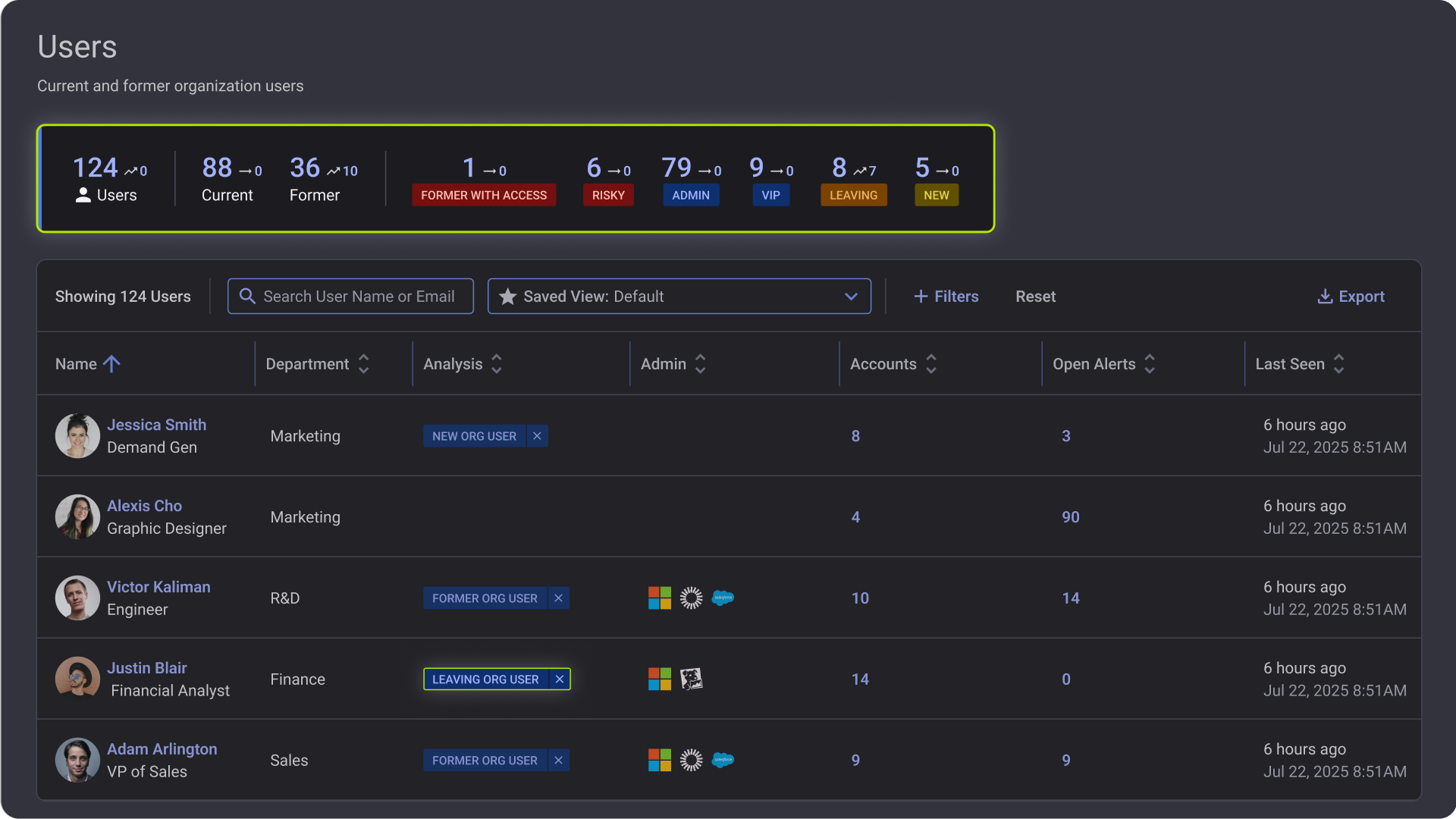
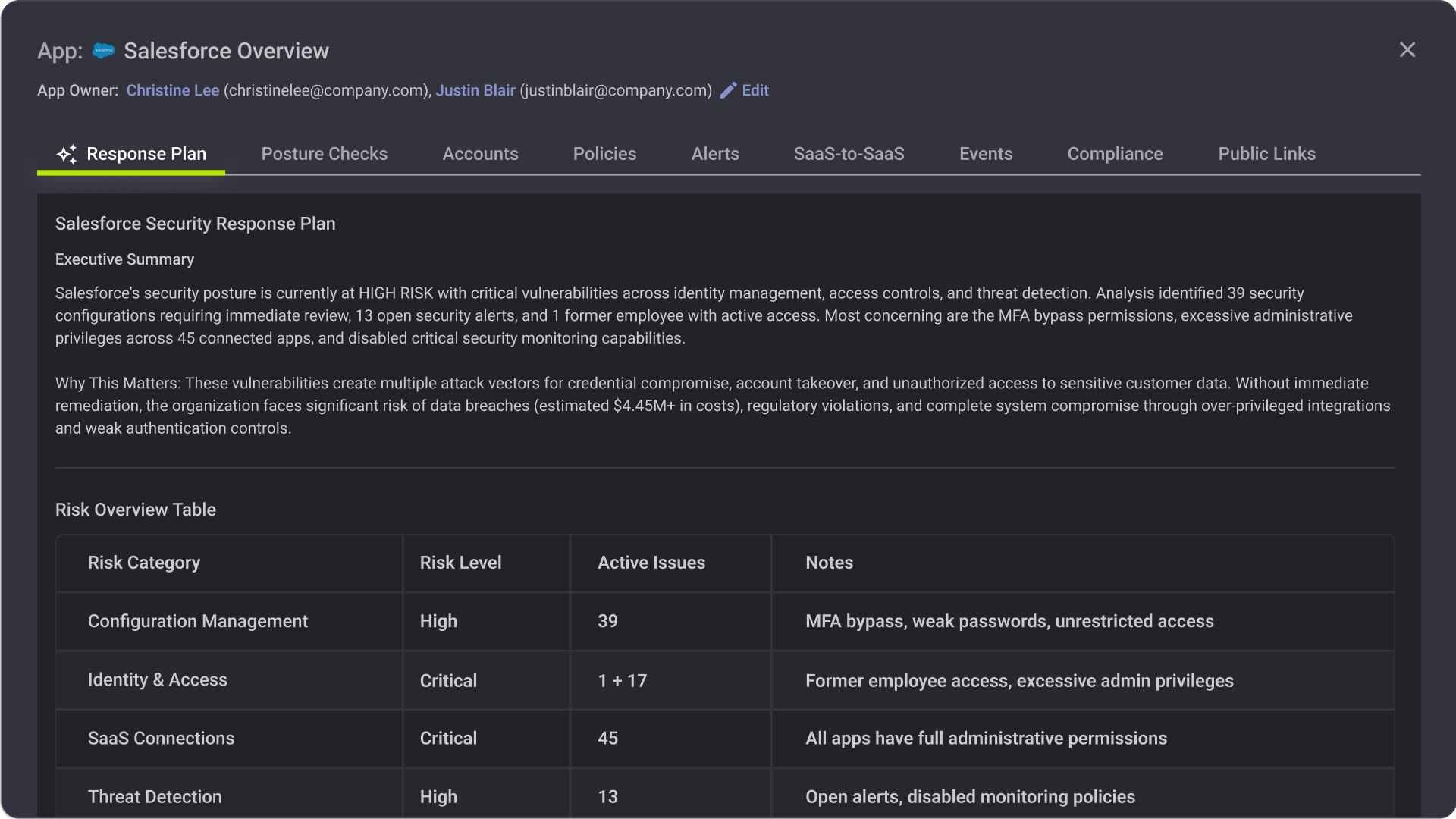
Reco monitors security posture across the major AI platforms and embedded AI features in enterprise SaaS applications.
• Microsoft Copilot: Full posture monitoring, prompt analysis, data access tracking
• OpenAI Platform (ChatGPT Enterprise): Audit logs, API keys, projects, user invites
• Anthropic Claude: Users, workspaces, API keys, compliance activities, files
• Cursor: AI coding assistant monitoring for development teams
• Glean: Enterprise AI search security monitoring
• Embedded AI: Salesforce Einstein, ServiceNow AI, and 200+ apps with AI capabilities
The App Factory adds support for new AI platforms in days, not quarters.
Explore the full
integrations list.