


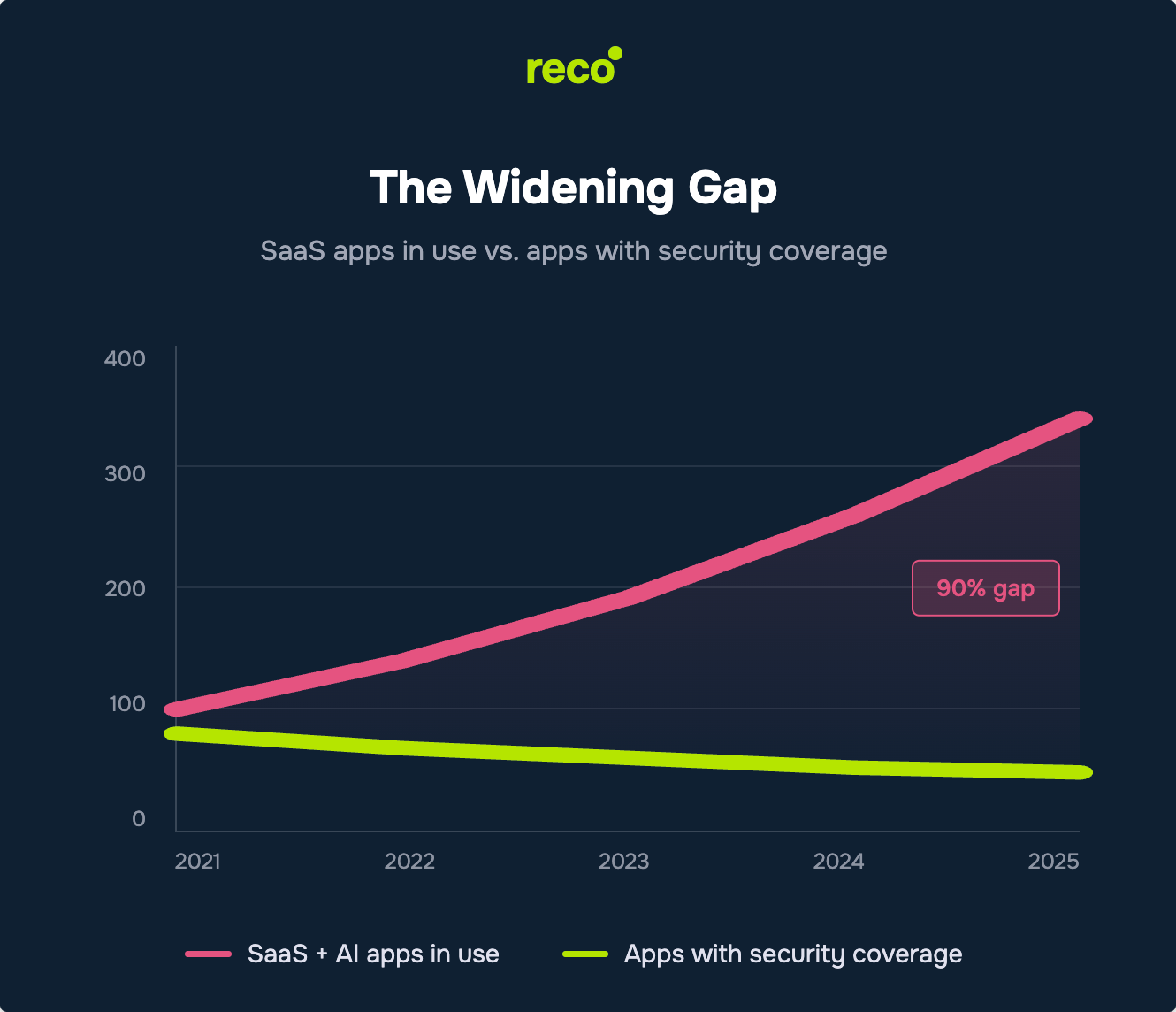
Your CASB watches network traffic. Your SSPM checks configurations. Together, they cover maybe 10% of your actual SaaS risk.
The other 90%? Browser-based AI tools with no installs. OAuth tokens that silently chain across your stack. Configuration drift inside apps you already approved. Identity sprawl that crosses permission boundaries you didn't know existed.
Traditional security tools weren't built for what SaaS has become.
Security teams bought CASBs to watch cloud traffic. They bought SSPMs to enforce configurations. Both tools work exactly as designed. The problem is what they were designed for no longer matches reality.
CASBs were built when SaaS meant Salesforce and a handful of approved applications. They inspect traffic between your network and cloud services. But an employee pasting source code into ChatGPT never crosses your network perimeter. A Chrome extension reading your Salesforce data doesn't show up in traffic logs. Browser-based AI tools operate entirely outside what CASBs can see.
SSPMs were built to audit configurations in the apps you know about. They check whether MFA is enabled in Okta, whether sharing settings are locked down in Google Workspace. Important work. But they can't tell you about the project management app that an employee connected to your HR system last Tuesday using OAuth. They can't see the AI integration that's pulling customer data through an API token no one approved.
Over 80% of SaaS incidents start silently. Not with a dramatic breach, but with a stalled dependency, an expired certificate, a leaked credential. Small issues that build quietly until something breaks.
Think of your SaaS security like an iceberg. The tip above the waterline? That's your sanctioned applications. IT-approved, SSO-connected, monitored. Your CASB sees them. Your SSPM audits them. You feel confident.
Below the waterline sits everything else.
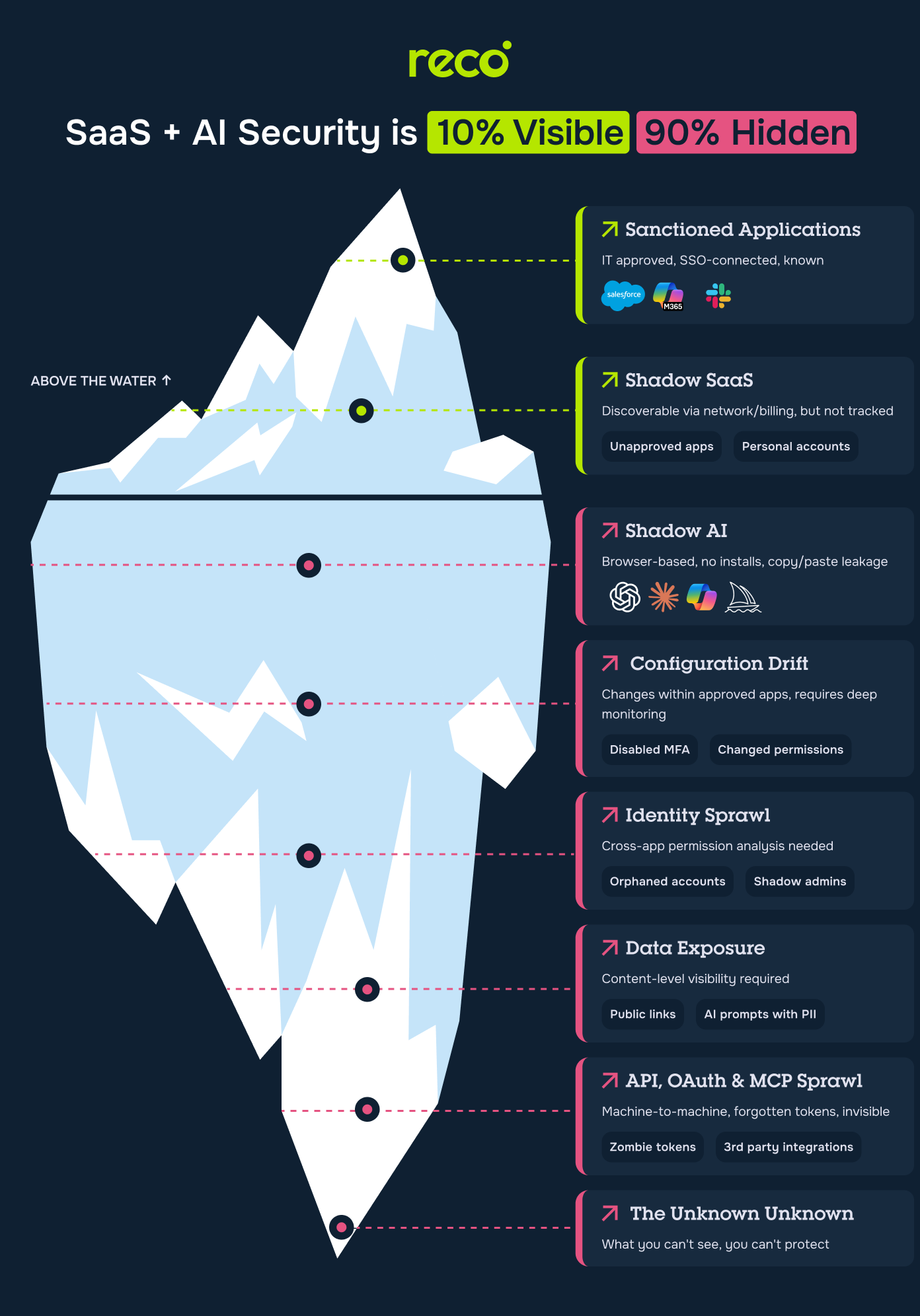
Unapproved apps and personal accounts. Discoverable through network logs or billing, but rarely tracked systematically. Your finance team might catch the expense report, but security never sees the access.
Browser-based tools that require no installation. An employee copies sensitive data, pastes it into an AI tool, gets their answer. No network signature. No install to detect. No visibility whatsoever. This is copy/paste data leakage at scale.
Changes happening inside your approved apps that your SSPM catches, but only on scheduled scans. Someone disabled MFA for a service account. A sharing setting reverted to public. You'll find out in the next audit cycle, which might be weeks away.
Cross-app permission analysis that no single tool provides. One employee, two identities: one from their freelance contract, another from their full-time hire. Both live, both privileged. Together, they form a hidden escalation chain. No alerts. No detection. Until the moment someone breaks in.
Content-level visibility into what's actually being shared. Public links to sensitive documents. AI prompts containing PII. The sharing happened three months ago. The exposure is ongoing.
Machine-to-machine connections that multiply silently. One OAuth token in a developer tool can unlock your repos, designs, and identity provider all at once. Traditional security tools weren't built to trace sanctioned SaaS talking to other sanctioned SaaS. So by the time you know, data's already walking out the door.
What you can't see, you can't protect. That's not philosophy. That's the gap your current tools leave wide open.
CASBs and SSPMs aren't broken. They're just solving yesterday's problem.
When these tools were designed, SaaS adoption was controlled. IT approved apps. Procurement tracked licenses. Users accessed everything through managed devices on corporate networks. The perimeter existed, and watching it made sense.
Today, employees spin up new AI tools faster than security can evaluate them. A single OAuth click connects applications in ways that cascade across your entire stack. Browser extensions touch your data without ever appearing in your app inventory. The attack surface isn't static. It reshapes itself daily.
The reality: Most teams track the apps they buy, not the ones employees connect on their own. That's where the trouble starts.
Closing this gap means going beyond network inspection and configuration audits. You need visibility into the connections themselves.
Which third-party apps have active OAuth access to your HR or finance systems right now? Which AI tools are employees authenticating with their corporate credentials? What data is moving between applications through API integrations no one sanctioned?
If you can't answer these questions today, you don't have discovery. You have hope.
Dynamic SaaS Security means monitoring not just the apps you approve, but the connections between them. It means catching shadow AI before the data leaves, not after. It means understanding that the breach won't come from the applications you're watching. It'll come from the 90% you can't see.
Your CASB and SSPM aren't failing. They're succeeding at a scope that no longer matches reality. The question isn't whether you have SaaS security tools. It's whether those tools see what your employees are actually doing.
Because right now, 90% of your risk is underwater. And the iceberg is growing.

Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.
