


GenAI regular use more than doubled in 18 months, from 33% to 71% of organizations (McKinsey 2024). What started as experiments became enterprise standard before security could catch up.
Your board approved those AI initiatives. They celebrated the productivity gains. Now they're asking: "What's our AI security posture?"
The problem isn't that you lack an answer. It's that your answer lives in a language boards don't speak. Configuration policies. OAuth token sprawl. Prompt injection risks. These concepts matter to security teams. They mean nothing to a CFO allocating capital.
63% of organizations that experienced a breach either didn't have an AI governance policy or were still developing one (IBM 2025). Security budgets are growing at only 4% while data management responsibilities surge with AI adoption.
The CFO needs to understand that an AI tool connected to Salesforce can export 1.2 million customer records worth $199.2M in breach liability at $166 per record. That's the translation.
Your employees adopted GenAI faster than security infrastructure could adapt. The gap between what employees use and what security monitors is your primary AI risk.
Every AI tool connected to your environment creates potential exposure. Quantify it:
Board-ready: '41 AI tools with access to 1.35M records. At $166/record, maximum breach exposure is $224.9M.
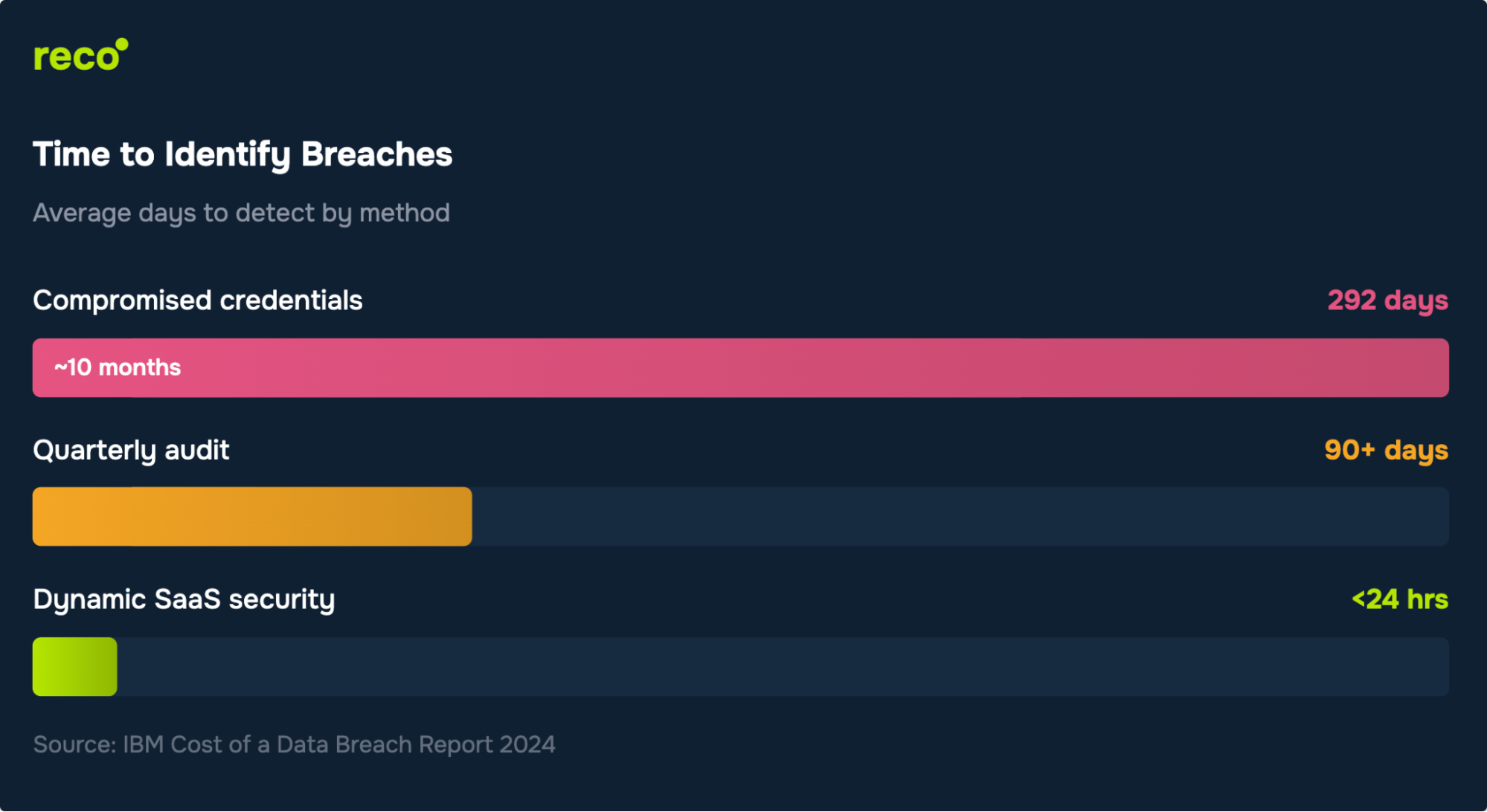
Board-ready: "Industry benchmarks show credential breaches take 292 days to identify. Our current quarterly audits create a 90-day blind spot. We are closing that gap to under 24 hours with dynamic monitoring."
AI governance affects cyber insurance, audits, and regulatory exposure. 97% of organizations that suffered an AI breach lacked proper access controls (IBM 2025). Governance isn't just paperwork; it’s the primary difference between a secure AI rollout and a breach.
"Shadow AI" means nothing to boards. Translate it:
The cost: Shadow AI adds $670,000 in additional breach costs on top of the $4.44M global average (IBM 2025)
The governance gap: 97% of AI-related breaches happened because basic access controls were missing.
You can't quantify AI exposure if you can't see AI tools.
Platforms like Reco's dynamic SaaS security change "we think employees use some AI tools" into "we discovered 47 AI tools, 23 with customer data access, representing $12.4M in exposure."
The Knowledge Graph maps which AI tools connect to which data sources automatically. It shows that marketing's transcription AI can access 340,000 customer records, not just that "an AI tool has OAuth access."
What changes:

Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.
