


It’s 9 PM. Your board meeting starts at 8 AM. The CFO just messaged you on Slack: “Can you give us a quick security update? Five minutes, tops.” You are staring at 47 security tools, 312 SaaS applications, and eight hours to explain why the budget increase matters.
This is not a presentation problem. It is a translation problem. You understand your security posture in detail. The board does not need that level of depth. They need three numbers: exposure, trend, and the ask.
In this situation, most CISOs default to comprehensive coverage. SIEM metrics. EDR percentages. Policy violations remediated. By slide seven, the CFO is checking email. Then the CEO asks the question the deck cannot answer: “Are we more secure than last quarter or not?”
Many security leaders report facing pressure from their boards to downplay the severity of cyber risks. In a global survey of IT security leaders, approximately 79% said they have felt boardroom pressure to understate the severity of cyber risk facing their organization. This often happens not out of choice but because an overly technical presentation can be dismissed as repetitive or overly negative.
The communication gap between CISOs and boards is structural, not personal. CISOs report what security tools are designed to measure, including threats blocked, configurations fixed, and compliance percentages. Boards, by contrast, allocate capital based on financial indicators such as dollar exposure, trend trajectory, and return on investment.
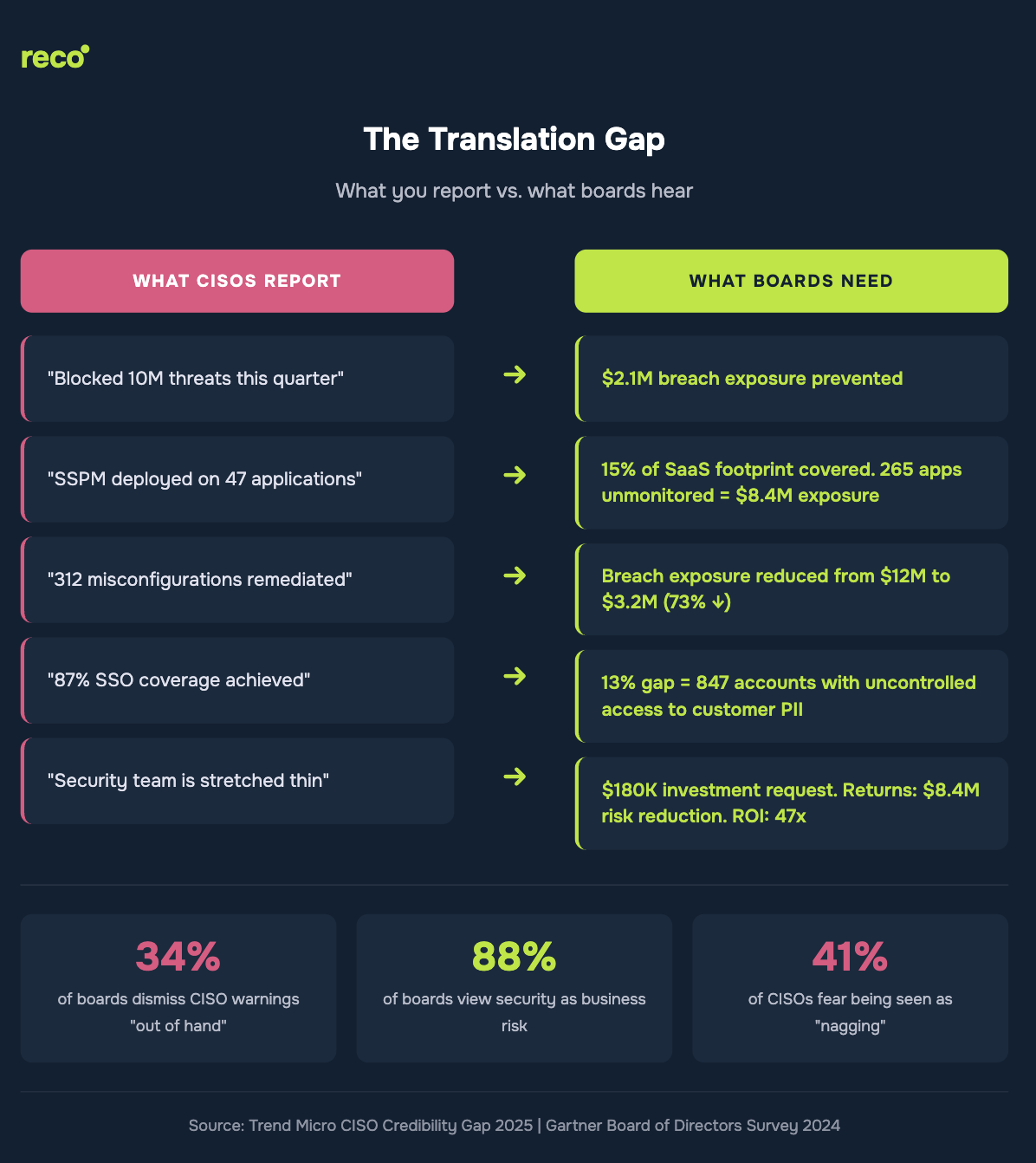
Research shows that 34% of CISOs say their boards dismiss security warnings out of hand. The issue is not board apathy. Gartner reports that 84% of board members identify cybersecurity as a business risk (Gartner Board of Directors Survey, 2024). The problem is misalignment. Technical comprehensiveness does not translate into capital allocation.
Every board-ready security update is built on three essential components. If anyone is missing, the update fails to support effective board-level decision-making.
One slide. Four numbers. Each has a dollar value.
Template:
One slide. Four numbers. Each has a dollar value.
Calculation formulas:
Three risks maximum. Each is framed in business impact.
What makes this work:
Connect investment to outcome. The goal is to move from a general resource request to a clearly defined loss prevention decision.
Template:
"Requesting $X for [solution]. Return: $Y breach exposure eliminated + $Z operational savings. Timeline: N days to coverage. Alternative: Accept $W ongoing exposure."
Example:
“Requesting a $180K annual investment in dynamic SaaS security. Expected return includes an $8.4M reduction in exposure and $340K in annual insurance premium savings. Full coverage achieved within 30 days. Alternative: accept a 60% visibility gap across the SaaS environment.”
Most CISO presentations fail because they attempt to cover too much rather than focus on what drives decisions. Before a board meeting, remove any content that lacks a dollar value and a clear decision point.
If the CFO wouldn’t approve it, the board won’t either. Test your deck by asking: “Would finance greenlight this based solely on this slide?”
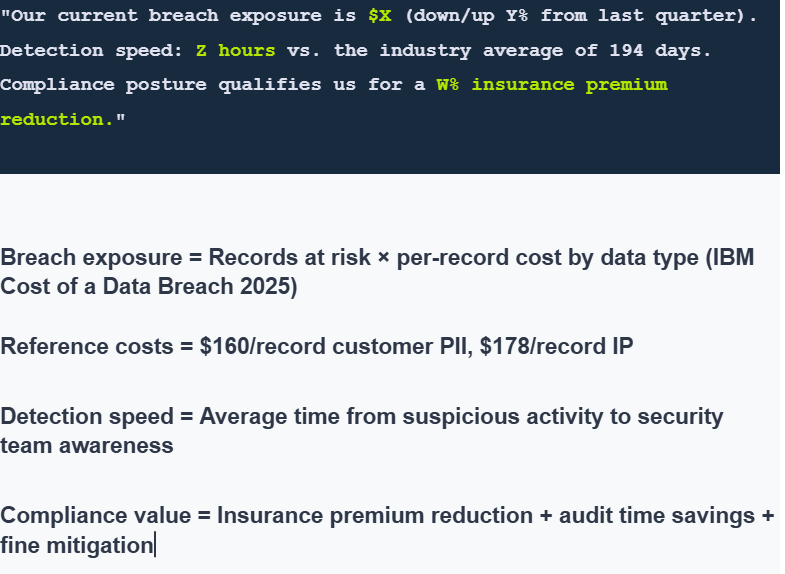
Use this to convert technical metrics into board-level language:
The average data breach now costs $4.88M, according to IBM’s 2024 report, representing a 10% increase from 2023. While this benchmark provides context, it does not inform board decisions. What matters is your organization’s specific exposure.
Step 1: Identify records at risk
Customer PII records accessible through current gaps × per-record cost by data type (IBM Cost of a Data Breach 2024)
Step 2: Add regulatory exposure
Step 3: Calculate detection penalty
Step 4: Document trend
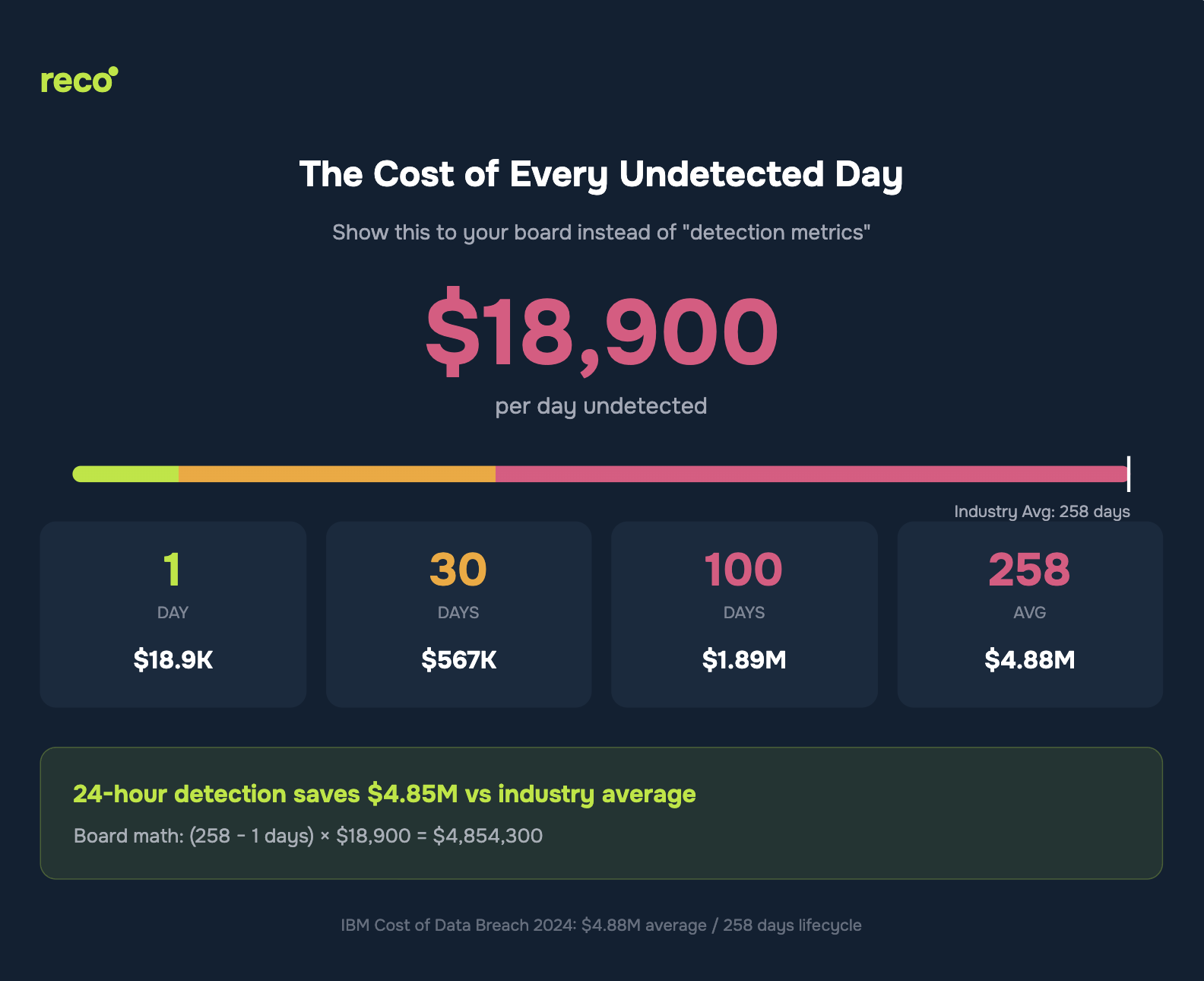
The gap in many board presentations stems from limited visibility. Risk cannot be quantified or reported accurately when material portions of the environment remain unseen.
Traditional SSPM focuses on sanctioned applications. Dynamic security extends visibility to what traditional tools often miss, including shadow AI tools adopted outside formal processes, OAuth tokens with excessive permissions, and SaaS-to-SaaS connections that were never explicitly approved.
With comprehensive visibility, board metrics reflect actual risk. Without it, reporting is limited to the portion of the environment that is visible, while unseen activity continues to drive the exposure that matters most.
Reco’s Knowledge Graph analyzes SaaS activity continuously, identifying risks that periodic reviews overlook. App Factory enables support for new applications within days rather than quarters. The result is board reporting that reflects the true security posture, not a partial view.
You have eight hours. Here's the action plan:
Tonight:
Tomorrow:
Five minutes. Three slides. One clear ask.
The board does not need to understand your security architecture. They need to understand your risk posture in the same terms they use for every other capital decision. Do that, and the conversation shifts from follow-up questions to budget approval.
Security posture does not fail in the boardroom because it is weak. It fails because it is translated poorly. When you quantify exposure in dollars, show the trend, and present a clear investment decision, security becomes a capital allocation discussion - not a technical debate. Five minutes, three slides, and one defined ask are often all it takes to move from explanation to approval.

Gal is the Cofounder & CPO of Reco. Gal is a former Lieutenant Colonel in the Israeli Prime Minister's Office. He is a tech enthusiast, with a background of Security Researcher and Hacker. Gal has led teams in multiple cybersecurity areas with an expertise in the human element.
